Need Software Development Team?
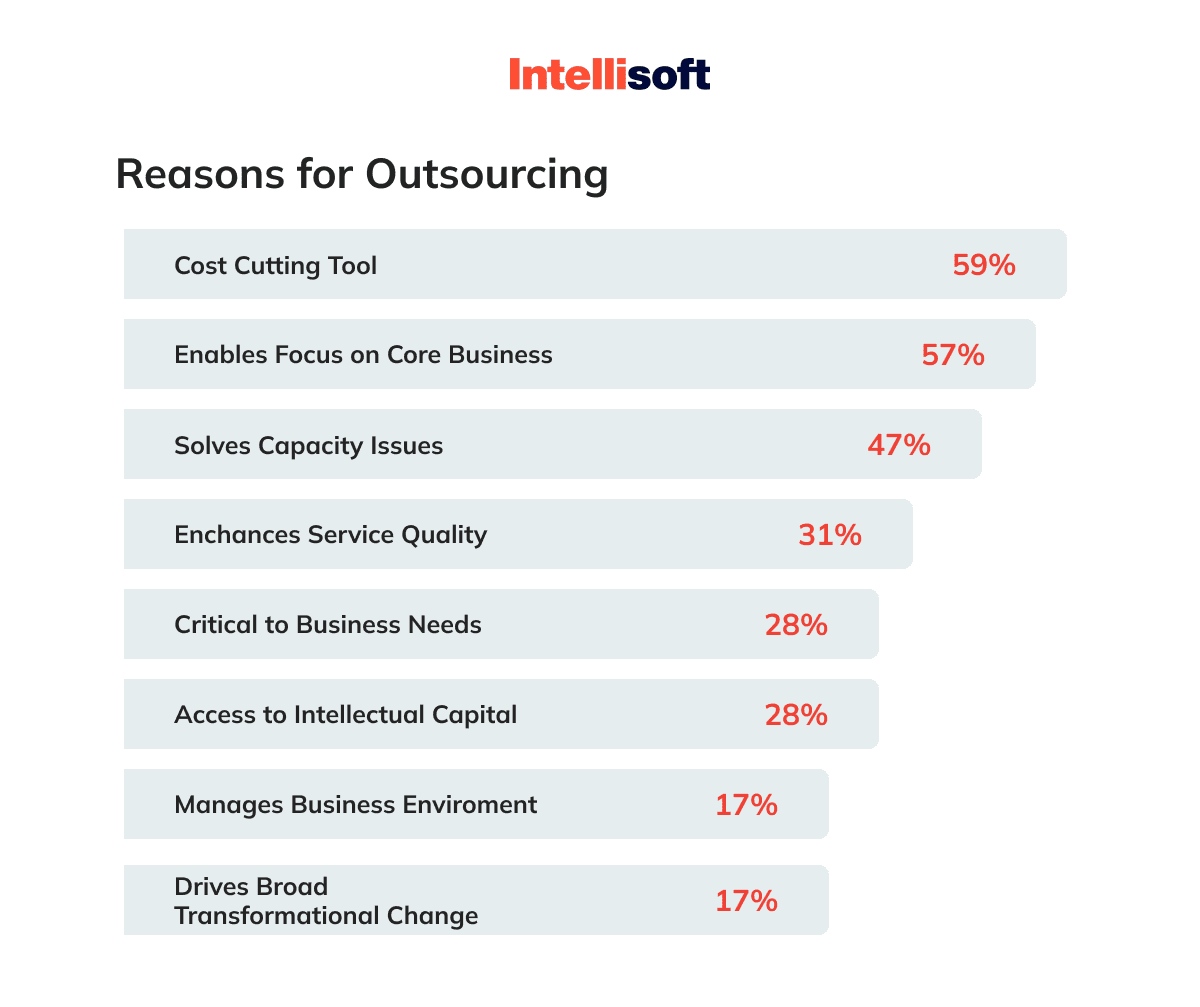
Over twenty million dollars! You risk losing this much if you don’t adhere to the General Data Protection Regulation (GDPR). This sum exceeds the budgets of many start-ups and small businesses.
Imagine having to pay a penalty that is one hundred times larger than your annual budget because of careless handling of app user sensitive info. You should exercise extreme caution whenever dealing with confidential information to prevent such a disaster from occurring. How? Delegating data management to the most trustworthy partners is a time-tested method. That is when the term data processing agreement (DPA) arises.
Signing a data processing agreement (DPA) between controllers and processors is a key component of GDPR compliance. The importance of signing a legally binding contract cannot be overstated. What exactly does it mean, and how does it apply to software development outsourcing?
Ask IntelliSoft. In our experience, we have faced signing a DPA with almost every partner or client we had. For instance, when we worked on projects for Cambion Healthcare Systems Denmark. Our team signed a DPA with this client to have a right to access and transmit patients’ records as well as work with IoT medical devices that send patient data directly to the electronic medical record (EMR) and clinical information system (CIS).
A crucial contract known as a data processing agreement protects you from many legal worries and fines, and we will explain it in detail in this article.
Table of Contents
What Is a DPA?
A DPA stands for a data processing agreement, which helps companies ensure that all data processing activities comply with GDPR policies. By signing the document, both parties protect the project’s details and come up with a strategy to prevent and eliminate info breaches.
This agreement should be implemented before a third party is given access to sensitive customer information and/or during the early stages of a startup’s development. Assume the following.
Imagine a company called HookahX, which is a made-up Austrian startup. It plans to use its website and mobile app to offer hookah delivery services. The startup signs a contract with a software development firm, say, it would be called Buildenture, to create that site along with the application. Customers who wish to place an order must do so by sending their full name and contact information via text message to HookahX. However, this is sensitive individual data, and the startup, being based in the EU, must adhere to the GDPR.
An outsourcing agency in this case also operates a website and an app through which clients can access their information. HookahX must ensure that the contracted developer is held liable in the event of any data breach.
Hence, HookahX enters into a DPA with Buildenture. The developer warrants that it will process customer data in accordance with the GDPR, per the terms of the Agreement.
Buildenture could still cause a breach, leading to legal action against their client. This DPA serves as a legally binding agreement demonstrating that the startup has taken all necessary steps to protect customer data. See what we mean now?
One more example. Bank clients would be the subjects of the data collected by the IT firm if it were to create online banking software. Data such as names, contact information, email addresses, physical addresses, zip codes, timestamps, access and authorization information, contracts, financial information, and credit card numbers are made available to the developers. In each scenario, the list will look slightly different.
The following are some examples of possible goals:
- Access to a network for the purposes of data transmission
- Communication with data subjects
- Data center storage of personal information
- Software product updates
- Data backups
- Computer processing of personal info, including transmission, retrieval, and access
- Software product configuration, operation, monitoring, and functionality assurance
However, the purposes of creating a DPA are more-or-less similar across the industries. Let’s check that.
Check These Readings Too:
- Legal Requirements for Storing Data: Key Insights for Storing User Data
- Everything About Technology Product Roadmaps. Tips & Tricks with Examples
- Most Effective Ways to Extend Your Software Development Team
- What Is the Technology That Protects the Intellectual Property Rights of Software?
- In-House vs. Outsourcing Software Development Teams
Objectives of DPA
By signing a DPA, ultimately, we at IntelliSoft want to make sure your information is secure enough. Non-encrypted data processing can be protected, including user names, birthdays, addresses, email addresses, file operations, login attempts, etc.
The details you’ll provide in your project are sensitive because they can be used to pinpoint an individual’s location. To avoid this, you should come to certain terms.
The Eurozone requires DPA, so it’s not merely a suggestion. Any violation could result in fines of up to 4% of worldwide revenue, which could amount to $20 million. Check Article 83 for more info.
Who Should Sign a DPA and Why?
“When do I need a data processing agreement?” That’s a nice question! You actually need one when you plan to outsource some or all project-related tasks. There are three scenarios for working with outside contractors:
- No individual information is handled. For instance, a financial institution may hire an IT firm to conduct UX/UI analysis and create a prototype for a new banking application. Since this processor does not have access to the bank’s customers’ personal information, a DPA is unnecessary.
- The processor handles the data but can’t see it in any detail. Because the IT staff can only access the databases in an encrypted format, a DPA is unnecessary.
- The controller entrusts data processing to a vendor. For instance, a Ukrainian outsourcing IT company receives an order from an EU client to develop a data management application for a medical institution. This project was commissioned by a client in the European Union. Patients’ private information is essential to their work. In this situation, signing the DPA is required. Moreover, before beginning the project, the company must modify its internal processes to meet the requirements of the agreement and achieve GDPR Compliance.
For Ukrainian IT-companies DPA plays a crucial role when entering into contracts with customers from the EU. This is because the data transfer goes beyond the EU, and the customer needs to make sure that the contractor. complies with GDPR and can guarantee a sufficient level of data protection. In this case, the DPA becomes a guarantee and proof for the customer.
Kosta Mitrofanskiy – CEO @ IntelliSoft A technology expert and entrepreneur with 20+ years of experience in the web & software development business.
Data Controller and Data Processor in Software Development Outsourcing
According to DPA, the terms “controller” and “processor” describe two distinct roles in the management of data. Both parties deal with the private information of people living in the European Union.
Information that can be used to determine an individual’s identity falls under the umbrella term “personal data,” but this definition does not exhaust the subject. For instance, in contrast to details like your address, the name of your favorite author does not constitute personally identifiable information.
Now, as for these two roles. A controller “determines the purposes and means of the personal data processing.” It could be “any person, organization, public authority, or other body, whether legal or natural.” A processor, on the other hand, “processes personal data on behalf of a controller.” Any company or individual you’ve hired could also qualify.
As the example above implies, HookahX is the DPA data controller while Buildenture is the DPA data processor. The startup must actively demonstrate full compliance with all data protection principles.
Buildenture is now considering using cloud storage services (e.g., Amazon Web Services). If this happens, AWS will be considered a sub-processor with access to sensitive customer information.
Buildenture must obtain HookahX’s written consent before using AWS to comply with the Regulation. With this approval, an outsourcing company will be able to enter into a “back-to-back contract” with AWS, which includes the same processor obligations as the original DPA. Vendor’s original DPA will remain valid and enforceable once the contract has been signed.

Do not forget that sometimes a sub-processor may show up on the horizon. We have already discussed it on the example of AWS.
Although a sub-processor technically falls under the definition of “processor,” it is not included in the DPA’s direct signature chain with the controller. However, the DPA signed by the processor with the controller must include a provision binding any sub-processors. A sub-processor is an external organization or company that gains access to data from the processor.
Make Sure You Check This Before Signing a DPA
Don’t be in a hurry. Remember that a DPA should only be signed after careful consideration of a few key factors, including:
- Should we have faith in the offered assurances?
A data breach that occurred on the processor’s end may still result in the controller being held liable under the GDPR. Therefore, it benefits both parties if the processor has enough available bandwidth to adequately secure all the info they receive from the controller. If a breach does occur, the data processor should be able to act swiftly to reduce the damage. - Does it always take that much time?
A DPA can be difficult to draft and may call for additional effort and time, but the results will be well worth the trouble. Your DPA will ensure that your responsibilities regarding data processing and security are consistent with GDPR requirements. Now, if you make mistakes when creating your DPA, it could be almost as bad as not signing it at all. Overall, DPAs can help your organization improve general security in regards to data handling. There is no certain answer to the question, “How long does it take to compose and sign a DPA?” It is all individual, but we recommend avoiding to postpone it. - Is there any “wiggle room” here?
It’s important for a DPA to have clear and concise language. For instance, if the controller will be auditing the processor, the entire procedure, down to the last detail, must be laid out. That way, both the processor and the contractor will know exactly what is expected of them, and the agreement will be solid all the way through. - What purpose will the data serve in the processor’s hands?
The data controller is responsible for making sure the processor’s DPA does not go beyond what is allowed by the underlying legal ground for processing. In other words, the data must be used exclusively for the purposes outlined in the contract between the company and the outsourced service. The data controller must verify the data processor’s intended use of the information.
What Are the DPA Requirements?
In order to write your own paper, you must use the GDPR DPA law as your Bible, which includes all descriptions mentioned in it. To save you some time, we will summarize the most important considerations.
- Informational abstract.
The info being described is the primary component. Include all potentially embarrassing details of the project to be discussed. Perhaps these are the names, addresses, and phone numbers of patrons. Every little thing matters, so pay attention to it. - Clarification of appropriate and inappropriate data manipulation techniques.
In what ways will data be encrypted, accessed, stored, and tested? Can security, privacy, and availability of processing systems and services be guaranteed by both parties? Specify the tools and databases you’d like to use if you need to get more technical. - Focus of the data controller.
When unanticipated data-handling situations arise, what steps should the data controller take to mitigate the situation? Does the data controller have any obligations regarding data access or data transfer formats? - The domain of the data processor.
Set the time frame for the processor’s access to the data. What sort of safety precautions are in place? How will the system use the data they process? Specify and stress everyone’s roles and responsibilities as the project progresses.
It is important to remember that the data controller is the one who must draft the contract and schedule any necessary follow-up meetings to ensure its legality and correspondence to the law.
Need Help With Project's MVP?
The DPA data processing agreement should have detailed terms. The rules and expectations should be made crystal clear to all parties involved. There is absolutely no “wiggle room” or “gray area.” This is why it is so important to clearly delineate the functions of both controllers and processors.
Things to Include in a DPA
Below, you can find a free DPA template in case you decide to create a DPA on your own.
General Provisions
Each of the following parties should be identified in a DPA:
- In charge of the data (controller). Those in control of the data are the stakeholders who have given the third party access to the data.
- Computes data (processor). An individual or another organization that processes data on the controller’s behalf.
In addition, the following are detailed in the introduction:
- Contents of DPA Records (data that will be accessed by a third party).
- Participants in a study.
- The reason for processing information.
- The extent of consumer records.
- Database Protection Administrator Software (data processing systems, tools, or software solutions).
- Terms for keeping private information (or enterprise data usage).
- A description of information storage.
Moreover, how long does a data privacy agreement (DPA) typically last? The following should be outlined:
- Period of time covered by this agreement.
- Termination of Agreement and Effects.
Remember to specify that the data processor must delete your information from their systems after the DPA expires. In other words, any information sent must undergo an irreversible deletion process.
Roles and Responsibilities of Stakeholders
For this section, you’ll need to have:
- A data controller’s privileges and obligations.
In this section, go over what your rights and obligations are as the data controller. DPA mandates that you ensure a processor treats data in accordance with the terms, processing instructions, and regulations you provide. - A data processor’s legal protections and obligations.
Data processors’ privileges and obligations are laid out in this section. To what end does one employ a data processor? Their primary responsibility is to keep all sensitive information secure at all times. A data processor has an obligation to provide you with a reliable response in case of a breach.
You have the right to audit a data processor’s compliance with the DPA and require them to keep records of any data-related activity they engage in.
Instructions And a Breakdown of the Steps
The third section focuses on the precautions taken by everyone involved in the outsourcing process to safeguard personal information and ensure its secure processing. Better yet, mention both of the following:
- The administrative aspects of ensuring data privacy and adhering to contracts.
- Similar to the previous point, but more focused on the technical details.
Final Clauses
Typically, this is where a company talks about:
- The terms under which the agreement can be modified.
- The statements proving DPA is superior to any other documents.
Annexes
Data Processing Agreements may have annexes that contain any supplemental documentation required for the agreement’s completion. Such as:
- Formulated in easy-to-understand tabular form, the procedures described herein.
- Confirmed findings from an audit.
- Critical sections of the General Data Protection Regulation.
How to Prepare to Work in Accordance with the GDPR?
You’ve probably heard of General Data Protection Regulation. What is GDPR? In a nutshell, it’s a rule that makes it mandatory for all businesses operating in the European Union (EU) to safeguard their customers’ personal information. As a software company founder, you should be aware that failing to comply with GDPR will cause serious issues. Here is how to get ready to comply with GDPR.
- Collaborate with law enforcement to investigate the firm’s actions.
Data access, storage, and processing methods, as well as the legal basis for processing them, must all be established through a GDPR check (a.k.a. audit). To comply with the Directive, it is necessary to analyze how data collection and processing will affect the rights and freedoms of individuals whose information is being collected and used (Data Privacy Impact Assessment – DPIA).
- Develop a policy for the treatment of personal data.
The process of using the data should include the collection, processing, storage, protection, and management of the data. It is essential to accept the terms of the concept of privacy by design and privacy by default.
In accordance with the concept of privacy by design, the organization must take into account the risks associated with the data processing when designing the processing procedure, developing functional requirements for IT systems, setting up protection measures, and transfering the data to the archives and its destruction. The concept of privacy by default implies that a company must process a sufficient amount of data with respect to clearly stated objectives.
- Establish an order in legal documentation.
It is necessary to develop a policy statement and an agreement that includes provisions on data processing and how consent to data processing can be given, as well as contains explanations of the data processing policy for the company’s own web pages.
- Establish order in the software.
Pay attention to the Data Governance class solutions. Availability of complete and up-to-date information about data, their storage methods, processing methods, and access rights will help in practical implementation of the law’s requirements. Also, special attention should be paid to the requirement to collect consents for processing and the quality of the data processing process.
Launch Discovery Phase For Your Project
In accordance with GDPR requirements, a simple click on the About or Continue box and the ten-page rules are no longer appropriate: The search must be done in such a way that every visitor really understands it. In addition, it should be very flexible and easy-to-use.
Nowadays, almost every web page you visit offers a pop-up message with the following content, “Dear user, in order to work correctly, the website collects your content (cookies, IP address, etc.). By continuing to use the site, you agree to the usage of your data.”
- Make sure that you do the appropriate work with the staff.
It is worth making sure that everyone is familiar with the GDPR and its procedures in order to prevent accidental loss of the flash drive with critical data.
What to Write in the DPA? Examples
Article 28(3) of the GDPR specifies the elements that must be included in the DPA. Using a sample contract between a customer (controller), on the one hand, and an IT firm, on the other, we will describe the various components in more detail below (processor).
- Treatment in accordance with the written directives of the controller.
Only per the controller’s written instructions may the processor handle sensitive personal data.
In April 2022, CHIL imposed a EUR 1,500,000 fine on DEDALUS BIOLOGY. The company developed IT solutions for laboratory management. 3,000 private and 30 government laboratories bought licenses for the software. In 2021, 491,840 patients’ personal data were leaked and sold on the darknet. During a CHIL audit, they found that DEDALUS BIOLOGY extracted more information than required and processed the data in violation of instructions.
How Much Will Your Project Cost?
Such situations result in millions of dollars in fines. Therefore, GDPR documents should include a detailed description of the amount of processing and security measures.
- For any breach of the rules, every person with access to the information must bear the consequences in mind.
The processor limits access to sensitive data to those who have agreed to maintain its secrecy. The team members also need to be under a DPA and undergo consistent training.
- Bringing in a sub-processor after approval from the controller.
In order to hire new staff or independent contractors, written permission must be granted. The DPA should clearly state the conditions for using a subprocessor. Data processing may be outsourced by an IT firm under the following conditions:
- It signs contracts with third parties to perform work on its behalf; notifies the client of any personnel changes to the sub-processing team.
- It is accountable for violations committed by subcontractors.
- It examines the subprocessor’s security and privacy procedures before beginning work to ensure it can provide the level of protection for individual data specified by the DPA.
- It publishes or, upon request, provides a list of the team members as of the DPA’s effective date.
The customer may object to changes in the team’s composition and within a certain period of time to notify them. However, the DPA needs to include terminology allowing for replacements due to unforeseen circumstances. If the situation calls for it, an IT firm can switch out a subcontractor without giving them any advance warning. For example, a developer gets laid off.
Hiring contractors without the controller’s permission can end in fines. For example, in May 2022, Wens Experience SRL paid 1,500 euro for engaging an employee to process data without written authorization, and thus violated the requirements of GDPR Article 28.
- Obeyance of Data Protection Regulation Article 32 Security Measures.
Anonymization and encryption, as well as testing the efficacy of measures and ensuring ongoing confidentiality, integrity, availability, and resilience of processing systems and services, timely data recovery, and resilience are all on the list of security measures. In order to begin work on a project, an IT firm must first put in place such safeguards.
- Assisting the controller.
For instance, when reviewing requests from data subjects or regulators, the processor will work with the controller.
- Erasing data.
The client has the option of requesting that the controller export, retrieve, or delete any remaining personal data.
- Data sharing for compliance.
Both the client and their auditor have the option to inspect the current state of security. The DPA suggests specifying the audit’s methodology and timeline. The controller, for instance, typically emails audit notices 60 days in advance. Audits must occur no more often than once per year. There will only be three full days for the audit. The audit may take place electronically if both parties agree to this. Don’t forget to determine who bears the cost of the audit.
It is better to examine several good examples of contracts before drafting your own. In order to illustrate, look at the publications from distinguished corporations that have something to do with programming:

By the way, the official GDPR site also features a sample data processor agreement.
Conclusion
Everything you need to know about the significance of DPA has been included in this article. The security of your company’s and your customers’ data is crucial to its success. Knowing the potential consequences of a data breach and making every effort to prevent one are both important. Hiring a reliable software engineering vendor is an excellent method of lowering exposure to danger. Still, you need to know all the nuances to be included in the corresponding agreements like a DPA.
Using the provided data, we expect you’ll be able to find a trustworthy, high-quality software development company. IntelliSoft is here to help businesses find and hire skilled offshore developers in a wide variety of technologies. Get in touch with us to find out more about preparing and signing DPAs and dedicated teams for your projects.
AboutKosta Mitrofanskiy
I have 25 years of hands-on experience in the IT and software development industry. During this period, I helped 50+ companies to gain a technological edge across different industries. I can help you with dedicated teams, hiring stand-alone developers, developing a product design and MVP for your healthcare, logistics, or IoT projects. If you have questions concerning our cooperation or need an NDA to sign, contact info@intellisoftware.net.