Web applications are prime targets for hackers, providing an easy gateway to a vast audience and enabling the rapid spread of malicious code. Unfortunately, many companies only start thinking about securing their web applications after a breach has occurred.
Let’s be real; this oversight comes at a steep cost. In 2024, data breaches are projected to cost the world a staggering $9.5 trillion. However, many of these incidents could be avoided with a proactive and defensive approach to web security. Therefore, you should learn more about web application security vulnerabilities.
At IntelliSoft, we’re here to help you protect your resources and peace of mind. That’s why we’ve put together an article on the most common web application vulnerabilities and the best practices to safeguard your web apps from malicious attacks and accidental damage in 2024. Save yourself the stress and financial loss by staying ahead of the game.
Table of Contents
What Are Vulnerabilities In Web Applications?
Vulnerability is a weak point of a system that hackers can leverage to compromise one’s business. As you might know, web applications communicate with multiple users and different networks and leverage some external resources (APIs and SDKs) for some functionality. For that reason, web application security vulnerabilities may include weaknesses in the app codebase and threads from third-party software.
Cyber Security Vulnerabilities In Numbers
We’ve researched an in-depth Application Security Report conducted by Fortra, a cybersecurity agency, to showcase current cybersecurity trends and threads. Guys from Fortra surveyed cybersecurity professionals from different organizations and industries to learn about current trends, solutions, and challenges that exist in the cybersecurity field.
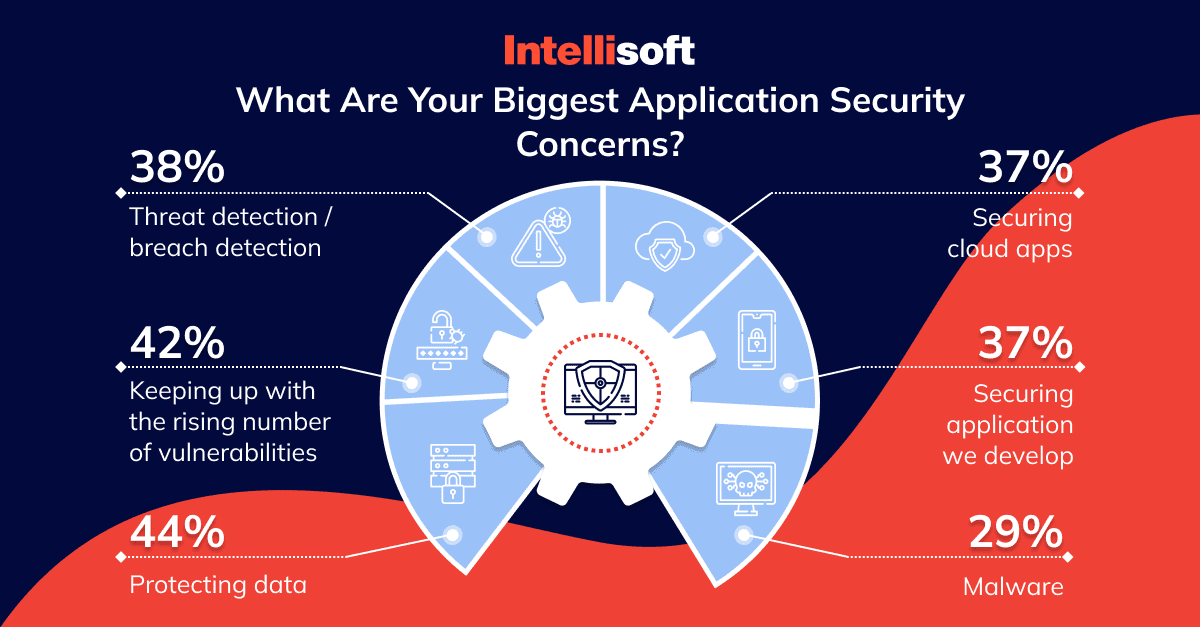
Here is a short overview:
- 44% of respondents said that protecting data is the most significant web app security concern.
- Keeping up with the rising number of cybersecurity vulnerabilities is the main challenge for 42% of respondents. In comparison, 38% are concerned about breach detection, and 37% consider cloud application security improvement as their primary goal.
- Cybersecurity professionals also cited other concerns, such as adding extra security layers for web apps they create (37%) and securing their systems against malware (29%).
- As for the main types of apps that bring the highest security risks to organizations, 42% of respondents answered that they are web apps that communicate with clients, and 40% think they are legacy apps.
- Other apps that still pose a risk include mobile applications for 30% of respondents, desktop applications (28%), and web applications used by organizations’ employees (26%).
But why can’t businesses better defend themselves against attacks? Well, there are several challenges, such as
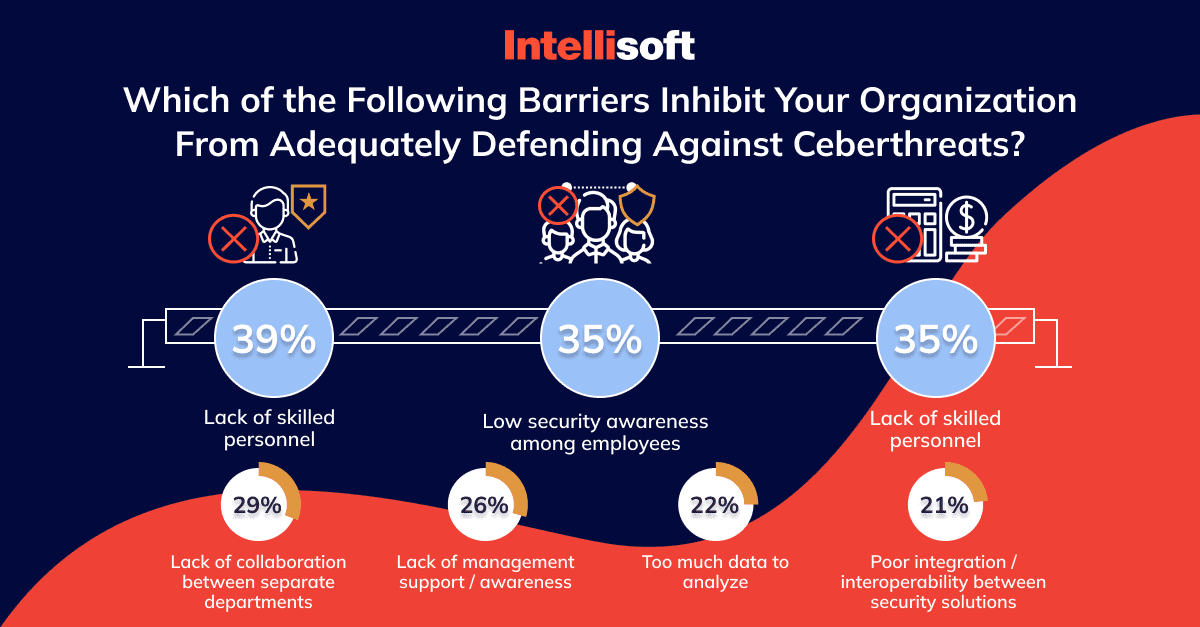
- Lack of skilled personnel (for 39% of respondents).
- Low-security awareness among workers (35%).
- Lack of security budgeting (35%).
- Poor collaboration between different departments (29%).
- Lack of management support and awareness (26%).
With this information in mind, let’s see how common web application vulnerabilities are and what data hackers steal.
How Common Are Attacks On Applications? What Forms Do They Take?
The Application Security Report also shows us some insights into the frequency of attacks on organizations:
- 44% of respondents have experienced data breaches.
- 20% of respondents experienced cyber attacks within the past year.
- 24% of respondents haven’t had data breaches.
- 32% of respondents can’t answer whether they have previously experienced cyber-attacks.
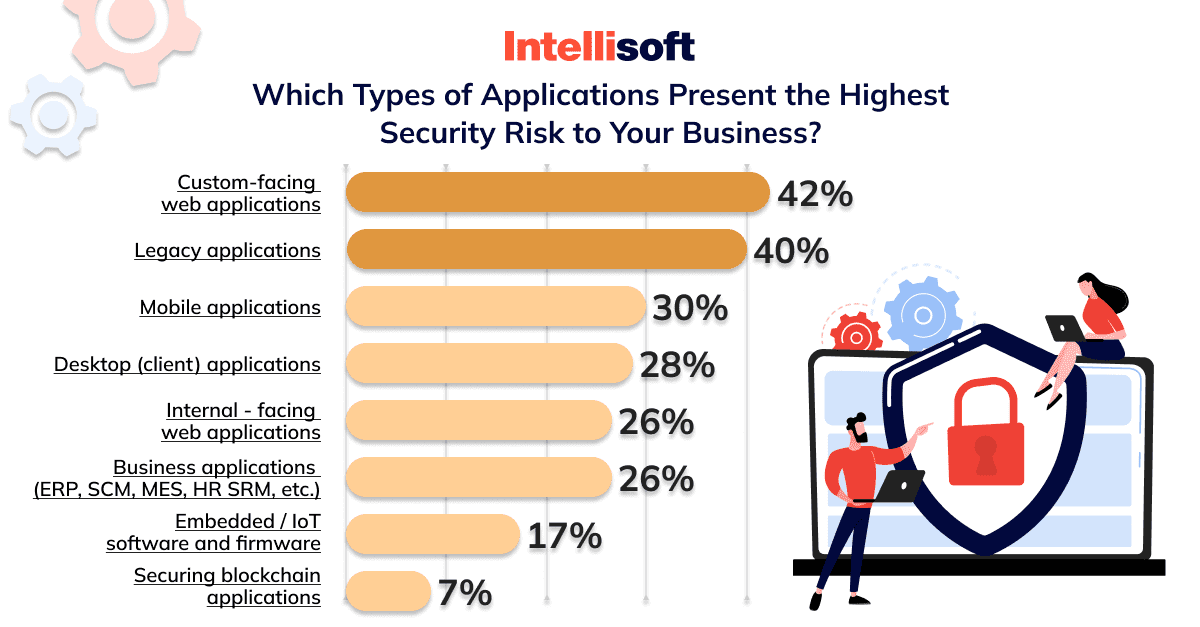
As for the security attacks against applications within the last 12 months, types, and forms they take, organizations shared the following information:
- 31% of respondents experienced malware attacks.
- 23% were targets of distributed denial-of-service (DDoS) attacks.
- 21% have experienced application misconfiguration.
- 20% of respondents have stolen user credentials.
Attacks on web applications are common, but organizations can’t eliminate web application vulnerabilities due to different business challenges. Now, let’s dive into more details of web applications’ most crucial security risks.
Top 10 OWASP Web Security Vulnerabilities [2021 List]
Open Web Application Security Project (OWASP) is an online community that analyzes, monitors, and evaluates web application security weaknesses and advises on how to prevent them. Why do we talk about OWASP?
Since 2003, OWASP participants have created OWASP’s Top 10 web application vulnerabilities list every 2-3 years to keep up with upcoming changes.
This way, this organization informs developers and web security experts about common security risks to help mitigate them in their web projects. OWASP members also share documentation, tools, articles, and methodologies in the field of web application security so that anyone can freely access those materials without paying anything.
Now, look at the recent web application vulnerabilities list of common types of vulnerabilities showcased by OWASP.
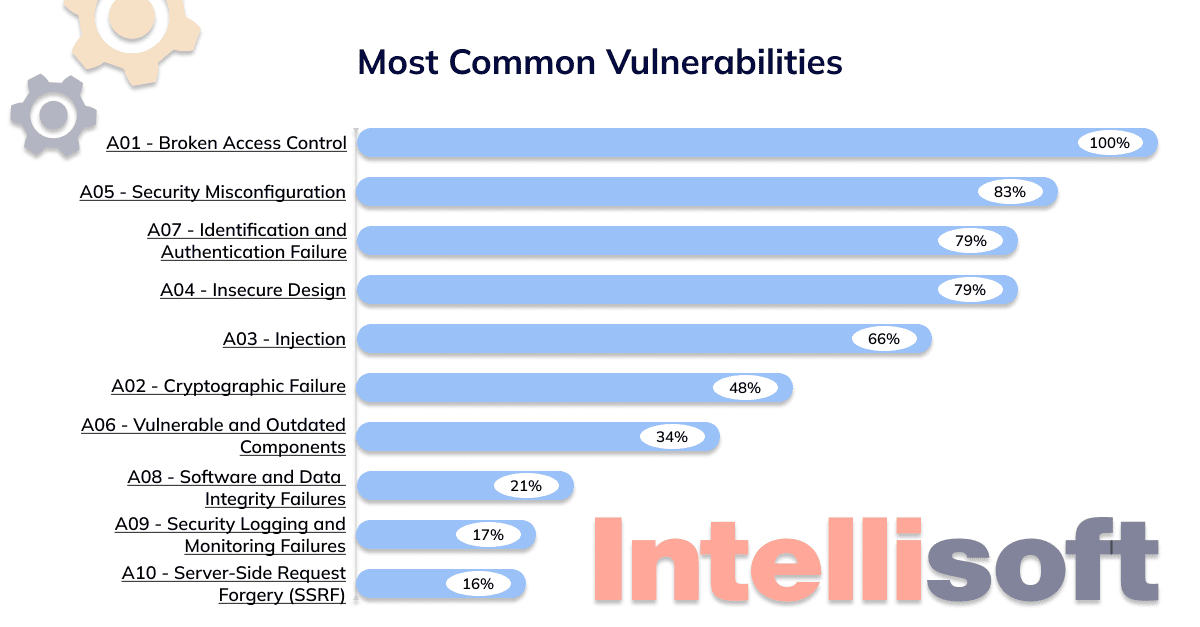
Broken Access Control
Broken access control is one of the database vulnerabilities that provides hackers access to user accounts. This vulnerability also means that average users can receive admin access with privileged functions. Thus, all web app owners should invest in extra security measures for access mechanisms that isolate users from administrator privileges.
Cryptographic Failures
Cryptographic failures are the type of web application security vulnerabilities previously named Sensitive Data Exposure. This weakness includes the lack of data protection in transit and at rest. Due to this vulnerability, third persons can receive your user’s passwords and credentials, health records, credit card numbers, user addresses, and other sensitive information that will compromise your web businesses and lead to the loss of reputation.
Cryptographic failures are hazardous if your business must comply with PCI Data Security Standards (PCI DSS) and data privacy regulations, including EU General Data Protection Regulation (GDPR).
Injection
Your application is vulnerable to this attack if it doesn’t validate, filter, or sanitize users’ data. This vulnerability also arises when the application uses dynamic queries or non-parameterized calls without context-aware escaping directly in the interpreter. In this way, the application allows attackers to send hostile data, comply and execute data on the server.
The most common types of injection flaws include NoSQL, OS, SQL command, LDAP, Expression Language (EL), Object Relational Mapping (ORM), or Object Graph Navigation Library (OGNL) injection. The best options to define whether the app is vulnerable to this attack are regularly running source code reviews and automated testing of all parameters, headers, URLs, cookies, JSON, SOAP, and XML data inputs.
Insecure Design
Insecure design is a broad category that includes different security weaknesses caused by missing or ineffective control design. In other words, some IT companies create web apps without security in mind. Or developers create web applications that do have a secure design but include flaws that can lead to exploitable vulnerabilities.
For example, if developers ignore Business Risk Profiling, an approach that helps developers identify risks, their likelihood, consequences, and measures to eliminate them. As a result, such a team will fail to determine the required level of security design.
Security Misconfiguration
OWASP Security Misconfiguration appears when your web app lacks security hardening across the tech stack. Developers improperly configured cloud service permissions and enabled or installed unnecessary features. Another scenario is if developers forgot to change the default accounts and their passwords for some reason or didn’t configure security features after the last system upgrade.
Related readings:
- Common Security Risks of Cloud Computing
- Top 10 Data Warehouse Software Tools for Your Business
- Cloud Computing Scalability: What Is It and Why It’s Important?
- The Great Cloud Storage Debate: ownCloud vs Nextcloud – Which One Is Right for You?
- What Is Kubernetes And When to Use It: Key Trends in 2023
Vulnerable and Outdated Components
The reason you may face this type of vulnerability is simple – once the software provider stops supporting outdated components, they become vulnerable to external attacks.
There are some sights that your web app has this vulnerability: you or your developers don’t know which version of third-party software your web app is directly using (on both client and server sides), including nested components.
Another reason is that any OS, database management system (DBMS), APIs, components, runtime environments, or libraries your app leverages are outdated, and their providers no longer support them. Your web app is also at risk if your developers don’t regularly scan web application vulnerabilities and don’t subscribe to security bulletins related to the components the app leverages.
Identification and Authentication Failures
This category of vulnerabilities in web applications reflects security problems with confirming user identity, broken authentication attack, and session management. Thus, you must protect all these elements to avoid authentication-related attacks. Otherwise, attackers can make automated attacks, receive a list of usernames and passwords, and other sensitive data.
Your application is also vulnerable if it uses weak or ineffective credential recovery processes, lacks multi-factor authentication, or reuses session identifiers after successful login.
Software and Data Integrity Failures
This vulnerability refers to the infrastructure and code without protection against integrity violations. Such an application may use plugins, libraries, or modules from untrusted sources, repositories, and content delivery networks (CDNs). If your web project has an insecure CI/CD pipeline, be ready for unauthorized access from attackers, malicious code, or another system compromise.
You should also be extremely careful if your app has auto-update functionality. Such functionality enables downloading updates for software components without sufficient integrity verification. In this case, your app can receive harmful updates from attackers that will impact all installations.
Security Logging and Monitoring Failures
If your application can’t detect security risks and respond to them, it has a security vulnerability named Security Logging and Monitoring Failures. Why? Because developers or DevOps can only effectively detect data breaches with proper detecting, monitoring, and logging. Here are also other signs that show your application is in danger:
- Developers don’t monitor logs for suspicious activities.
- The system stores log only locally.
- The system doesn’t log logins, failed logins, and high-value transactions.
- The system generates inadequate or confusing log messages in case of warnings and errors.
- The application fails to detect, escalate, or alert developers for active attacks in real-time or near real-time.
Server-Side Request Forgery (SSRF)
If your web application fetches remote resources without validating the user-supplied URL, your project is likely in danger. Why? Because such a scenario allows hackers to send a crafted request to an unexpected destination. Even if you protect your server with a firewall, VPN, or rules from the network access control list (ACL), your server becomes vulnerable when it accepts unvalidated URLs as user inputs.
As you can see, cyber security vulnerabilities take different forms and can arise inside the web app and external resources it uses. But there is a solution – a vulnerability management program. Let’s check how to mitigate all the risks by adopting such a program in your organization.
How To Manage Web App Vulnerability: 4 Stages
A Vulnerability Management Program is a continuous process within a business to identify and remediate cyber security risks and vulnerabilities. The team that usually works on such a program includes specialists from different departments, such as security staff, development and operations teams. They leverage assets management, vulnerability scanning, and vulnerability assessment software to create a Vulnerability Management Program.
Creating such a program includes several stages that ensure the team didn’t overlook any vulnerabilities and addressed them correctly. Such a process will consist of the following steps:
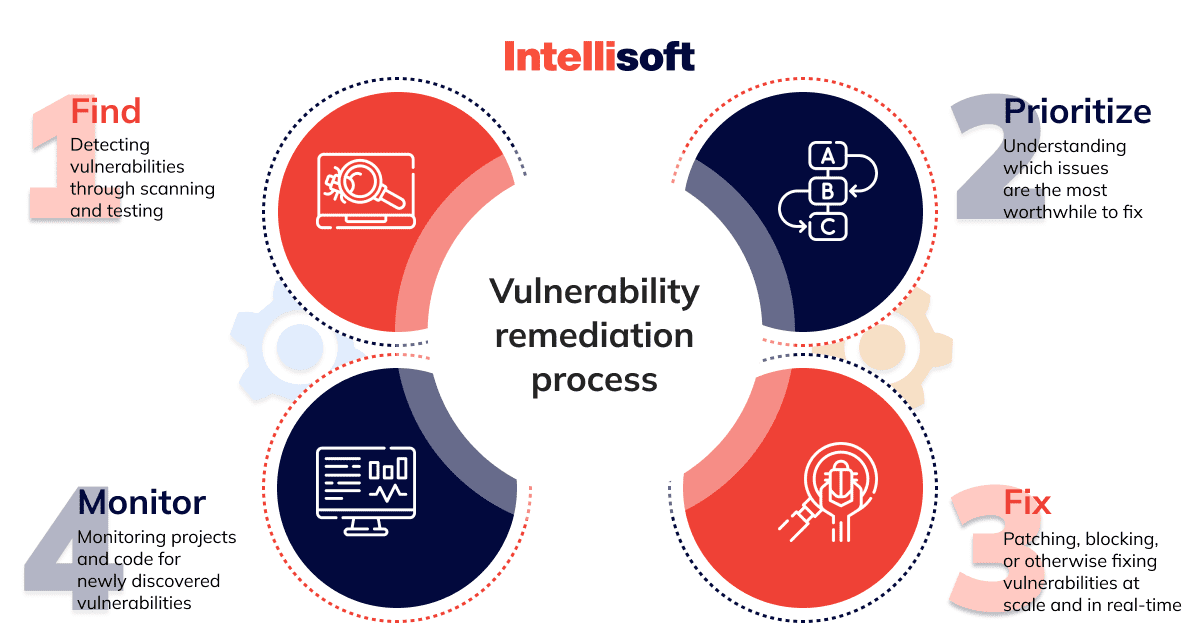
Step 1. Identify
During the first stage, the team identifies vulnerabilities that affect the web application and creates a list of vulnerabilities in web applications. The team will leverage threat intelligence information and vulnerability databases for this stage to identify threads. The team will also apply vulnerability scanners to help identify affected components and gather all the vulnerabilities into one list.
Step 2. Evaluate
Once your team finds all the vulnerabilities in your application, they can prioritize them. It means that some vulnerabilities are more dangerous than others and require significant resources. Developers must fix such vulnerabilities first to ensure that the app is secured enough and can handle attacks while the team is fixing minor vulnerabilities.
But how will they know which vulnerability is more dangerous than the other? A common Vulnerability Scoring System (CVSS) is very handy in this case. This system evaluates levels of all the vulnerabilities from the list by inherent characteristics, temporal traits, and specific impacts of exposures to your application.
Step 3. Treat
With the list of vulnerabilities and their evaluation, your team can begin illuminating them, starting from most important to less important. There are three ways the development team can react to vulnerabilities:
- Remediate. This way includes patching the vulnerability and fully fixing it, which is the most preferred way.
- Mitigate. When the team can’t fully remediate the vulnerability, the team reduces the likelihood of harming exposure to the system by applying compensating controls.
- Accept. The team can apply this approach only for low-risk vulnerabilities. Or in cases when the solution to a vulnerability will require resources bigger than the vulnerabilities thread.
This stage requires a close collaboration of such team members as system administrators, product owners, and your security team to handle each vulnerability adequately. When the team eliminates all the vulnerabilities, they should scan the system again to ensure they are nailed to mitigate or remediate all the threads.
Step 4. Monitor
The ability to detect and prevent threats will help your business to manage future risks that may arise. For that reason, you should continue to evaluate your vulnerability management program, even if everything seems okay after the first round of risk mitigation. What will help your team to achieve this goal? We recommend using the visualization reporting feature presented on most vulnerability management software.
This way, your developers will have all the insights that tell them what technique to apply to eliminate the most vulnerabilities with minimal effort and time. Besides this, monitoring will help your security team track vulnerability trends over time and report on risk reduction progress to you and other stakeholders.
To streamline reporting and monitoring, we advise integrating web application security vulnerabilities management software with IT ticketing systems and patching tools. This way, all the team members across different departments will be updated on the current situation and can take action more effectively.
Since it is clear how to treat vulnerabilities in your web app, let’s see what tools your team will need.
What Solutions Can Prevent Web Application Vulnerabilities?
We have gathered solutions that will help your team to cope with vulnerabilities and improve the security of your web project. This list includes different software testing techniques and technologies we applied in previous projects, which performed great in all stages of the software development lifecycle – from development to maintenance and support. Thus, you can make these technologies and approaches a part of your Vulnerability Management Program.
Static Application Security Testing
Static application security tests (SAST) include the technique that allows developers to analyze the application source code for vulnerabilities and security risks during the development stage. With the help of SAST, the development team can successfully identify issues in design and coding that will potentially threaten the app’s security. Developers also use SAST before committing the new code to the development codebase and building new application releases.
Note that static application security tests are now a silver bullet – since it is rule-based, test results can include false data. Thus, QA managers and developers must carefully analyze and filter test results to detect real security issues.
Dynamic Application Security Testing
Dynamic application security tests (DAST) allows the development team to analyze the application and find potential weaknesses in code deployed in a staging or production environment.
During DAST, testing software sends different requests, including unexpected and malicious inputs, and then analyzes the results to find vulnerable elements of the application.
We can compare tests DAST tools perform to tests done by manual penetration testers leveraging Fiddler, Postman, Burp Suite, and other application security testing software.
Interactive Application Security Testing
Interactive application security testing (IAST) software combines two approaches we previously mentioned – dynamic testing like DAST software performs, and static analysis made by SAST software. In this way, IAST tools help developers and testers to gather and monitor the app behavior, such as input, output, data flow, and logic and find vulnerabilities in real-time.
Developers should deploy the IAST agent in the app to perform runtime analysis of such components as memory, data flow, and code.
Penetration Testing
A penetration test (pen test) is the approach that simulates the actual attacks on the web application to identify potential weak spots. For this type of test, testers leverage the same tools, techniques, and processes as hackers do and attack the system security infrastructure with planned attacks.
As a rule, organizations prefer outsourcing penetration testing to sub-contractors. Why? Because the person who will run this test mustn’t know about system security measures. This way, you’ll receive a clear picture of blind spots your developers missed during the development stage.
Runtime Application Self-protection
Runtime Application Self Protection, also known as RASP, works great as a personalized web application security solution. This web application security solution analyzes the app’s state and data, and after identifying potential risks, it applies in-application instrumentation to block them.
Developers can integrate RASP directly into the codebase via SDK or deploy the RASP agent to the host at runtime.
Software composition analysis
Software composition analysis (SCA) is a fully automated process testers use to identify open-source software and third-party components in a project’s codebase. Since such integrations are becoming part of a system, you should regularly monitor security, license compliance, and code quality to avoid any threads such integrations can include.
Web Application Firewall
Web application firewall (WAF) is a web application security solution developers leverage to add an extra protection layer to the system, which performs as a filter barrier between attackers and the targeted server.
Using WAF, you can protect your web project from the most common web application firewall vulnerabilities, including file inclusion, SQL injection, cross site request forgery, and cross site scripting (XSS).
Web application firewalls leverage pre-defined rules – policies that protect the system from attacks and filter malicious traffic. Developers can set up their policies and modify existing ones within minutes to respond immediately to various attacks.
Ensuring Ultimate Security For Your Web Application With IntelliSoft
As you can see, security is essential. In our experience, the best way to take care of your web project is to develop it with safety in mind. Unfortunately, 46% of software development teams do not automate testing security vulnerabilities of a web application during the development lifecycle.
Unlike other development companies, the IntelliSoft team takes cybersecurity as the main priority of our projects. Proof of this is that we are successfully developing projects for Healthcare and eLegal industries, where security trumps everything.
Suppose you are looking for a reliable tech partner who will help your organization solve web app security vulnerabilities or develop a secured web project from the ground up and ensure further maintenance and IT support. In that case, you are in the right place.
At IntelliSoft, developers and QA engineers know everything about the latest web application vulnerabilities, so they are ready to empower your IT project with additional security measures. The last thing that remains is to contact us and tell us about your project.