The healthcare industry is increasingly becoming a battleground for cybercriminals. With each passing year, the industry’s digital footprint expands, carrying with it a treasure trove of sensitive patient information. From medical records to financial information, the stakes are undeniably high.
The healthcare industry has held the unfortunate title of having the highest information breach costs for the last couple of years. This grim statistic demonstrates the urgent need for robust encryption in healthcare.
A data breach in healthcare is a breach of trust. Patients entrust their most intimate details to medical professionals, expecting unwavering confidentiality. When this trust is violated, the consequences can be detrimental. It’s time for the healthcare industry to shift from reactive to proactive, and data encryption in healthcare is the cornerstone of this transformation.
IntelliSoft, with a fifteen-year legacy in the healthcare sector, understands the complexities and encryption challenges in healthcare. We’ve witnessed the devastating impact of data breaches and are committed to empowering healthcare organizations with cutting-edge encryption solutions.
Table of Contents
What is Encryption?
Let’s explore the encryption basics.
By applying intricate mathematical algorithms, encryption scrambles information, making it unintelligible to anyone lacking the correct decryption key.
In essence, encoding acts as a digital fortress, shielding data from prying eyes and preserving its confidentiality. It is a fundamental component of information security, particularly in industries like healthcare, where sensitive patient information demands the highest level of protection.
Banner
Text: Looking For Healthcare Data Encryption Experts?
CTA: Hire Now
Link: https://intellisoft.io/contacts/
Encryption in Healthcare
Encryption usage in a regulated healthcare environment policy is a cornerstone of information security within the healthcare industry. It’s a process that converts readable data into a coded format, rendering it unintelligible without a decryption key.
Key Applications of Encryption in Healthcare
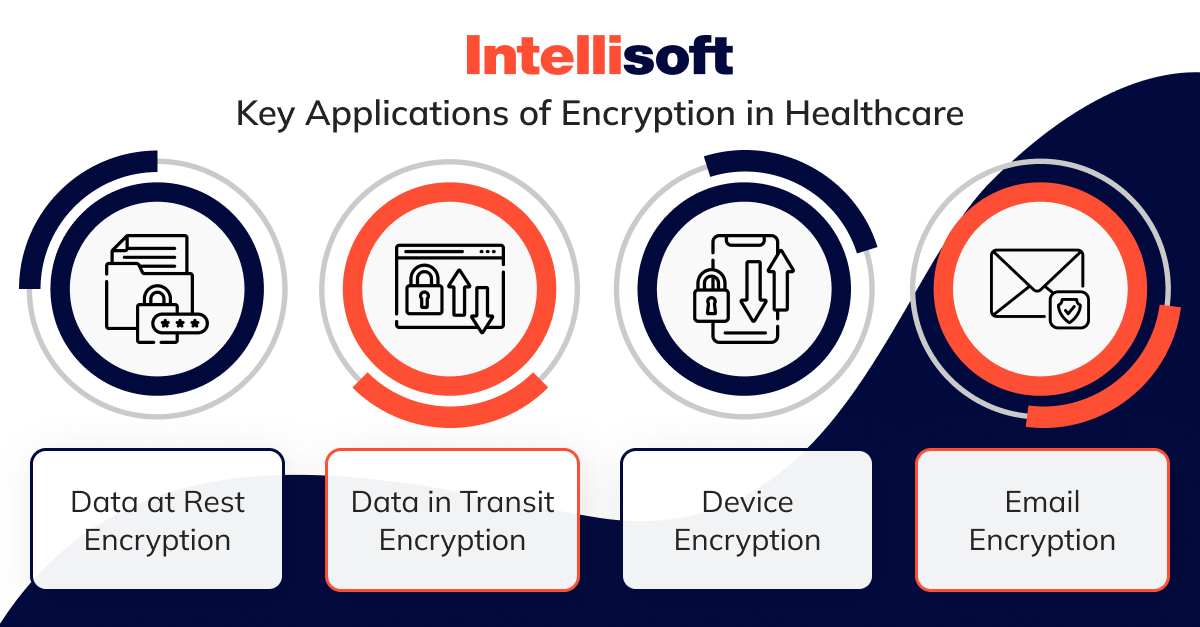
- Data at Rest Encryption. This involves encrypting information stored on servers, hard drives, or cloud storage platforms.
- Data in Transit Encryption. As healthcare information is frequently shared between different systems and locations, encryption is essential to protect it during transmission. For example, when patient records are transferred between healthcare providers or medical images are sent for remote consultation, encoding ensures information confidentiality.
- Device Encryption. With the increasing use of mobile devices in healthcare, encrypting these devices is crucial. Whether it’s a clinician’s smartphone or a patient’s tablet, encoding safeguards sensitive information stored on the device from unauthorized access if it’s lost or stolen.
- Email Encryption. Given the reliance on email for communication within healthcare organizations and with patients, encrypting email content is essential. This protects patient information from being intercepted and read by malicious actors. For example, encrypting emails containing appointment details, test results, or prescription information can significantly reduce the risk of information breaches.
Security and encryption in healthcare is vital in protecting other sensitive healthcare data, such as research information, billing information, and employee records, beyond these core applications. By implementing comprehensive encoding strategies, healthcare organizations can significantly enhance their security posture and build trust with patients.
The Importance of Encryption in Healthcare
As Peter G. Neumann mentioned, “It’s sometimes said that cryptography doesn’t fix problems, it changes them. You start with an information privacy problem, and cryptography replaces it with a key management problem.”
Homomorphic encryption in healthcare transforms information into a code that is unreadable to unauthorized users, ensuring that even if a breach occurs, the information remains inaccessible and secure. This is especially important for healthcare providers who store vast amounts of personal and medical information, from health records to insurance details.
Consider a scenario where a hospital’s database is compromised by cybercriminals. Without encoding, attackers could easily access patient records, potentially exposing confidential information such as medical histories, test results, and personal identification details. However, if the information were encrypted, the information would be rendered useless to the intruders.
A real-life example of the importance of healthcare data encryption can be seen in the 2017 WannaCry ransomware attack, which severely impacted the UK’s National Health Service (NHS). The attack paralyzed systems across the NHS, leading to the cancellation of thousands of appointments and surgeries.
While the attack was not directly linked to a failure in encoding, it highlighted the devastating consequences of insufficient cybersecurity measures in healthcare. Encryption could have been a critical component in minimizing the damage, ensuring that even if the ransomware accessed the information, it would remain encrypted and, therefore, unusable.
HIPAA Privacy and Security Rules
The HIPAA Privacy Rule was created to ensure the confidentiality of patients’ medical information by establishing strict guidelines for the use and disclosure of personal health information (PHI).
This rule is applicable to healthcare providers, health plans, and healthcare clearinghouses, and it stipulates that patient information can only be shared under certain conditions, such as for treatment, payment, or healthcare operations.
In contrast, the HIPAA Security Rule is focused on protecting electronic protected health information (ePHI). It requires healthcare organizations to adopt comprehensive security measures that include administrative, physical, and technical safeguards to ensure the safety of electronic health data.
Among these, technical safeguards like encoding play a pivotal role. While the Security Rule does not mandate encoding, it strongly encourages its use to protect ePHI both at rest and in transit. The importance of encryption is underscored by its ability to render information unreadable to unauthorized individuals, thus preventing breaches and ensuring that patient information remains secure.
The Relationship Between Data Encryption and Patient Privacy
Data encryption is vital for protecting patient privacy in healthcare. It transforms sensitive health information into an unreadable format, ensuring that information remains secure even if intercepted or accessed by unauthorized individuals.
Moreover, encryption supports compliance with regulatory requirements such as HIPAA, which emphasizes the protection of patient privacy through robust information security practices. Healthcare providers are increasingly facing cyber threats, and encryption acts as a critical defense mechanism, reducing the likelihood of information breaches that could compromise patient privacy. By integrating encryption into their information management strategies, healthcare organizations not only protect their patients but also uphold their reputations and avoid costly penalties associated with non-compliance.
How Does Encryption Protect Sensitive Data?
This process involves using algorithms to generate complex, random text from the original data. Only those with the appropriate key can reverse this transformation, restoring the data to its original, readable state. This concept, known as cryptography, forms the foundation of modern data security.
However, encoding is not a foolproof solution.
The effectiveness of encryption depends on various factors, including how, when, and where the data is encrypted and decrypted, as well as how the decryption keys are protected.
For instance, encrypting data stored on hard drives (known as at-rest encoding) protects it from physical threats, such as unauthorized access to the storage devices. However, it does not protect against vulnerabilities within the applications that process this data, such as bugs that could be exploited by attackers.
Similarly, encrypting information during transmission over networks (known as in-transit encryption) safeguards it from being intercepted by unauthorized parties. This is commonly seen in HTTPS protocols used on the web.
However, this type of encoding does not protect information from being compromised once it reaches its destination, such as when it is processed on a server that may be vulnerable to attacks. Additional measures, such as Server-Side Encryption (SSE), can further reduce exposure by hiding data from attackers within servers, but even these measures require decryption at some point to allow for information processing.
Encryption Algorithms and Key Lengths
Encryption algorithms and key lengths are critical components in the protection of sensitive information. An encryption algorithm is essentially a set of mathematical procedures designed to convert readable information into an unreadable format, ensuring that only authorized parties can access the original information.
The effectiveness of this conversion process relies heavily on both the algorithm itself and the length of the encoding key, which is a specific sequence that dictates how the information is encrypted and decrypted.
Various encryption algorithms cater to different security requirements. For example, the Advanced Encryption Standard (AES) is highly regarded for its combination of speed and security, making it a popular choice for safeguarding a wide range of information, from financial transactions to confidential government information.
On the other hand, RSA encryption is particularly effective for securing data in transit over the internet, utilizing an asymmetric approach that involves different keys for encoding and decryption. This dual-key system enhances security, especially in scenarios where secure key exchange is critical.
The length of the encoding key, typically measured in bits, is a crucial factor in determining the strength of the encryption. Longer keys result in a higher number of potential combinations, which dramatically increases the difficulty for unauthorized individuals to crack the code through brute-force attacks.
For instance, a 256-bit key used in AES provides an exceptionally high level of security, with a vast number of possible combinations that far exceed the capabilities of older, less secure systems like the 56-bit key used in the now obsolete Data Encryption Standard (DES). However, it is important to note that while key length significantly contributes to encoding strength, the overall security also depends on the resilience of the algorithm against contemporary cyber threats.
Ensuring that both the encryption algorithm and key length are robust enough to withstand modern attacks is essential for maintaining the integrity and confidentiality of sensitive information.
Related Readings:
- What is EHR Software? Build Your Custom System and Digitize Doctor’s Scribbles with IntelliSoft
- Data Warehousing in Healthcare: Transformative Strategies
- Fast Healthcare Interoperability Resources (FHIR) Explained
- Healthcare App Developers for Hire: Which Option to Choose
- Transforming Healthcare Communication: Integration of HL7 Interface Engine
Encryption Standards and Regulations
Encryption standards and regulations provide a framework for safeguarding sensitive information. They outline the cryptographic algorithms and key management practices required to ensure data confidentiality, integrity, and availability. Adherence to these standards is crucial for maintaining security and compliance in today’s digital landscape.

Advanced Encryption Standard (AES)
Overview
- AES is a widely recognized encoding standard developed by the National Institute of Standards and Technology (NIST). It provides a strong foundation for securing sensitive data across various sectors.
Key Features
- Key Lengths. AES supports 128, 192, and 256-bit key lengths, offering different levels of security.
- Usage. Commonly used by government agencies, financial institutions, and private enterprises to protect everything from personal data to classified information.
- Global Adoption. AES is the benchmark for encryption due to its balance of security and performance, making it a global standard for data protection.
General Data Protection Regulation (GDPR)
Overview
- GDPR is a comprehensive data protection regulation implemented in Europe to safeguard personal data and privacy.
Encryption Requirements
- Mandatory Encryption. Organizations must use appropriate encoding methods to protect personal data, particularly to avoid heavy fines in case of a data breach.
- Data Breach Response. If encrypted data is breached but remains secure due to encryption, penalties may be reduced, emphasizing the importance of strong encoding practices under GDPR.
- Global Impact. Though a European regulation, GDPR has influenced data protection practices worldwide, making encryption a critical component of global data security strategies.
Health Insurance Portability and Accountability Act (HIPAA)
Overview
- HIPAA is a U.S. regulation that governs the protection of health-related information, ensuring that patient data remains confidential and secure.
Encryption Guidelines
- ePHI Protection. HIPAA strongly encourages the encoding of electronic protected health information (ePHI) to prevent unauthorized access.
- Flexibility. While encryption is not explicitly mandatory, organizations must implement it or an equivalent security measure and document their reasoning if they choose not to use encryption.
- Compliance. Encrypting health data helps healthcare providers comply with HIPAA regulations, avoiding significant penalties and maintaining patient trust.
Payment Card Industry Data Security Standard (PCI DSS)
Overview
- PCI DSS is a security standard that regulates how payment card data must be protected to prevent fraud and data breaches.
Encryption Requirements
- Data Transmission. PCI DSS requires that cardholder data be encrypted during transmission over public networks to protect against interception.
- Data Storage. Sensitive data, such as credit card numbers, must be encrypted when stored, ensuring it is secure even if the storage medium is compromised.
- Industry Compliance. Adhering to PCI DSS encoding standards is crucial for businesses that handle payment card transactions, as non-compliance can result in hefty fines and loss of customer trust.
Banner
Text: How Much Will Your Project Cost?
CTA: Calculate Now
Link: https://intellisoft.io/it-outsourcing-prices/
Best Practices Of Data Encryption in Healthcare
In the healthcare sector, securing sensitive patient data through effective encryption is crucial to prevent unauthorized access. To maintain the highest standards of data security, healthcare organizations should adhere to the following best practices:
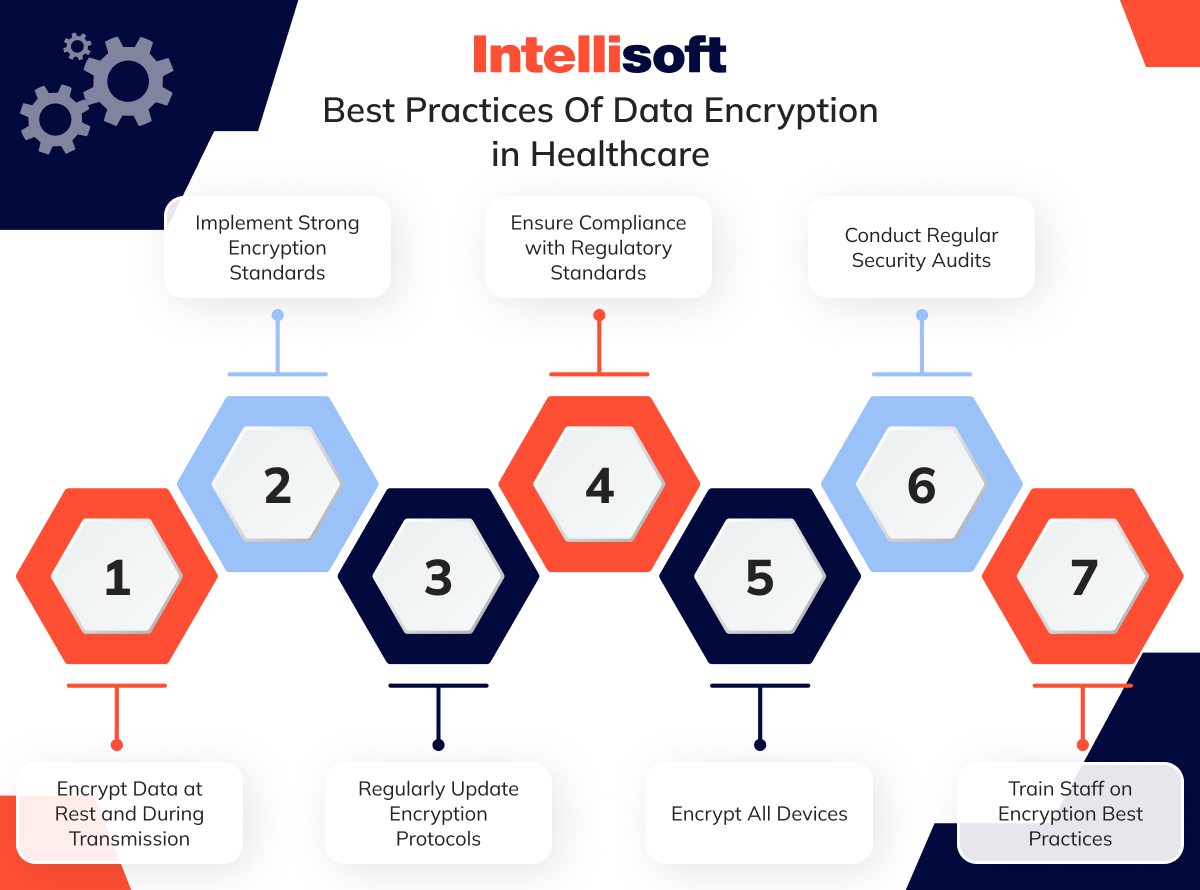
Encrypt Data at Rest and During Transmission
Patient data should be encrypted both when it is stored (at rest) and when it is transmitted across networks (in transit). Encrypting data at rest shields it from physical threats, like unauthorized access to storage devices, while encoding during transmission protects it from being intercepted during communication. This comprehensive approach ensures that patient data remains secure, no matter where or how it is accessed.
Implement Strong Encryption Standards
Healthcare organizations must use strong encoding standards, such as AES-256, to secure sensitive information. Advanced encryption algorithms are more resistant to hacking attempts, providing a higher level of protection against cyber threats. Adhering to well-established, up-to-date encryption standards ensures that patient data is effectively safeguarded.
Regularly Update Encryption Protocols
As cyber threats continuously evolve, so too must encryption protocols. Regular updates to encryption software and practices are essential to defend against emerging vulnerabilities and potential attacks. This includes applying patches, adopting new encoding technologies, and regularly evaluating the effectiveness of existing encoding methods to maintain their security.
Ensure Compliance with Regulatory Standards
Healthcare organizations are required to comply with regulatory standards such as HIPAA in the U.S. and GDPR in Europe, which often mandate or strongly advise the encryption of patient data.
Encrypt All Devices
All devices that store or access patient data, including servers and mobile devices, should be encrypted. Encrypting devices ensures that sensitive information remains secure even if a device is lost or stolen, which is especially important in healthcare settings where portable devices are frequently used by practitioners.
Conduct Regular Security Audits
These audits should evaluate the effectiveness of encoding protocols, verify compliance with regulatory standards, and pinpoint potential vulnerabilities. By conducting regular audits, healthcare organizations can proactively address security issues before they lead to breaches.
Train Staff on Encryption Best Practices
Staff training plays a critical role in maintaining robust encoding practices. Healthcare employees need to understand the significance of data encryption, how it works, and the correct procedures for handling encrypted data. Regular training ensures that staff stay informed about the latest security protocols and can effectively contribute to protecting patient information.
Wrapping Up
Data encoding is more than just a checkbox in healthcare – it’s a vital part of keeping patient information safe and secure. By focusing on strong encryption practices, like securing data at rest and in transit, using the latest encoding standards, and staying on top of updates and regulations, healthcare organizations can build a solid defense against cyber threats.
Encrypting every device, running regular security checks, and making sure staff understand the importance of encryption all contribute to a safer, more secure environment for patient data.
In a world where patient information is constantly at risk, encoding is your frontline defense. Making it a priority not only protects your patients but also strengthens your organization’s trust and credibility.
Need help fine-tuning your encryption strategy? Reach out to IntelliSoft today – we’re here to help you keep your data safe and secure.