Protecting the intellectual property software isn’t just a precaution—it’s essential. When you’re pouring your heart and soul into developing a new product, you’re not just hoping for the best; you’re setting the stage for incredible success. Every brainstorming session, every hypothesis tested, and every innovative breakthrough brings you closer to the moment your product earns the recognition it deserves. That’s why every feature and function you develop is so crucial—they help your product shine in a crowded market.
But here’s the catch: navigating the intellectual property protection for software can be tricky. Not only do you need to shield your own creations—your copyrights, patents, and trade secrets—but you also need to tread carefully around the IP of others. A simple misstep could lead to accusations of infringement, turning your hard work into a legal nightmare.
Intellectual property law is complex, with intricate regulations that you must adhere to throughout the software development process. Consider this: 90% of the total value of S&P 500 companies lies in their intellectual property, compared to just 10% in tangible assets.
This article will dive into the nuances of intellectual property protection for software, especially when working with outsourcing companies. We’ll highlight key considerations to keep in mind to safeguard your innovations while collaborating externally. Let’s ensure your intellectual property is secure as you bring your visionary products to life.
Table of Contents
1. What Is the Meaning of Software Intellectual Property?
According to WIPO, your software may be categorized as IP. It means that others can use all programs only if the owner allows this. The exclusive right belongs to the company that: 1) created the object (software solution or code); 2) acquired the rights to it. Using the object without its consent is considered illegal.
Intellectual property and software is a valuable intangible asset for both a startup and an “experienced” IT enterprise. Working with innovative technologies comes with increased security risks. But the main threat lies inside the company. Yes, employees may be involved in theft as well. There are also many dangers outside of business: scammers, cybercriminals, and rivals.
There are many options to protect your product before it is released to the market, such as signing an NDA with each employee or restricting team members from accessing a product under development. However, a security guarantee can be obtained only in one case: if you get a legal right. So, there are four types of IP rights applicable to intellectual property software. Note that the first three refer to protecting the product itself and the last to its name, motto, etc.

Types of IP rights
- Patents
The point is to protect the functional part of the software as an invention. It allows you to dispose of the object at your discretion: produce, use, or sell it. To do this, describe the program’s algorithm implemented with technical devices and the results of its use.
For your application to be approved (for example, in the US, the Patent Office does this), the object must meet critical conditions: uniqueness, a benefit for users, and innovativeness. Patentability also plays a major role, i.e., whether your object meets the criteria established in a particular country. No one can legally manipulate a patented object other than its owner.
A patent makes you a long-term monopolist for 20 years. During this time, you can get tremendous benefits from owning the invention. In addition, patenting helps you protect software intellectual property that other rights do not qualify for (authorship or privacy). It applies to ideas, algorithms, and methods implemented in the product, for example, unique UI features or editing functions.
- Copyright
If it’s about an idea, then this right won’t suit you. Copyright can only extend to the results of ideas: code (object, source) and even UI elements. Such a right arises with the program’s author and remains with them for life (plus 70 years) or passes to a third party. If the product was created by hired professionals, then the period is 95 years from publication (or 120 years from creation).
Copying, editing, distributing, and selling copies are included in the list of your intellectual property rights in computer software. Unauthorized actions of others with your product are regarded as copyright infringement. It applies to both plagiarism and piracy, such as using the program after the subscription ends or selling counterfeit versions.
This right is acquired automatically in many countries, including the United States. However, you can only bring the violator to justice after registering your software intellectual property rights. As a rule, such objects are equated with literary works. When registering, you should list elements taken from third-party sources (audio, graphics, text).
- Trade secrets
This term refers to information that your company prevents from disclosing. The goal is to obtain commercial benefits and avoid unnecessary costs and risks. For example, the original design of clothes belongs to authorship, but the method of its manufacture is a trade secret. It is important that competitors do not access it and do not use the data for personal gain.
You may keep in secret the following:
- source codes and object codes not distributed publicly;
- trial versions of programs;
- project design;
- formulas and algorithms;
- ideas that shape your competitive advantage;
- information about products under development and their functions
- information about customers and contractors;
- information about project management: methods, decisions (planned, adopted, and in progress), etc.;
- data on financial and economic activities and marketing;
- data on business relations with other companies;
- data on the methods of protecting information and equipment.
In fact, such data can be hidden while the owner maintains its privacy or a third party does not discover it. This software intellectual property does not include elements that can be studied with legal methods, such as reverse engineering (research of the principle of operation of a ready-made solution).
- Trademarks
Unlike previous rights, it does not protect your technology from being recreated or imitated. For example, when it comes to design, it’s about copyright. A trademark refers to a name, logo, or slogan that you use to sell or promote your product.
You can trademark any material that identifies you as the creator. It will prevent another company from using your brand name if it has the same type of product and market.
The owner may declare that the trademark belongs to them and is protected in certain territories. There are distinguishing symbols and designations: ® (registered) and ™ (not registered). The second character is used for new products or when you apply for registration.

You should protect your product before it is released to the market and presented to the audience. First of all, hire a competent software intellectual property attorney with experience working with IT companies to study your rights and understand how to protect them. We also recommend patenting technologies and registering trademarks wherever possible. It will be good to ask all your team members and contractors to sign the NDA.
Now your product is ready to be marketed and distributed. What’s next? You need to arrange its licensing.
Related Readings:
- SaaS Security Tips and Checklists: Best Practices To Protect Your SaaS Application
- Legal Requirements for Storing Data: Key Insights for Storing User Data
- Understanding the New Rules: MDD vs. MDR
- Monolitic vs Microservices Architecture: Pros and Cons
2. Licensing as a reliable way to protect software intellectual property
A license is a legal instrument that determines the peculiarities of using a product. Also, it’s another source of income for businesses: many are willing to pay big money for the opportunity to work with the IP of another company. You can license all kinds of ownership discussed above (except for trade secrets, of course).
In fact, a license is an agreement between the owner (licensor) and a person who wants to use the product in their activities (licensee). Such an agreement contains detailed descriptions of the possible actions of both parties and measures in case of their violation. Thus, the client gains access to your property and undertakes to use it on your terms and following your restrictions.
If you want a guarantee that your code won’t be copied and the product won’t end up in the hands of third-party users, a licensing management system is vital for you. It also allows you to take control of all licenses that have been sold. The main goal is to build a strong strategy based on the licensing model.
Each model contains parameters that characterize software deployment and the use of your intellectual property. It would be best if you offered different licensing options to suit the wants and needs of all customers while still providing a decent level of intellectual property protection software. Next, we will look at common models that you can apply in your practice.
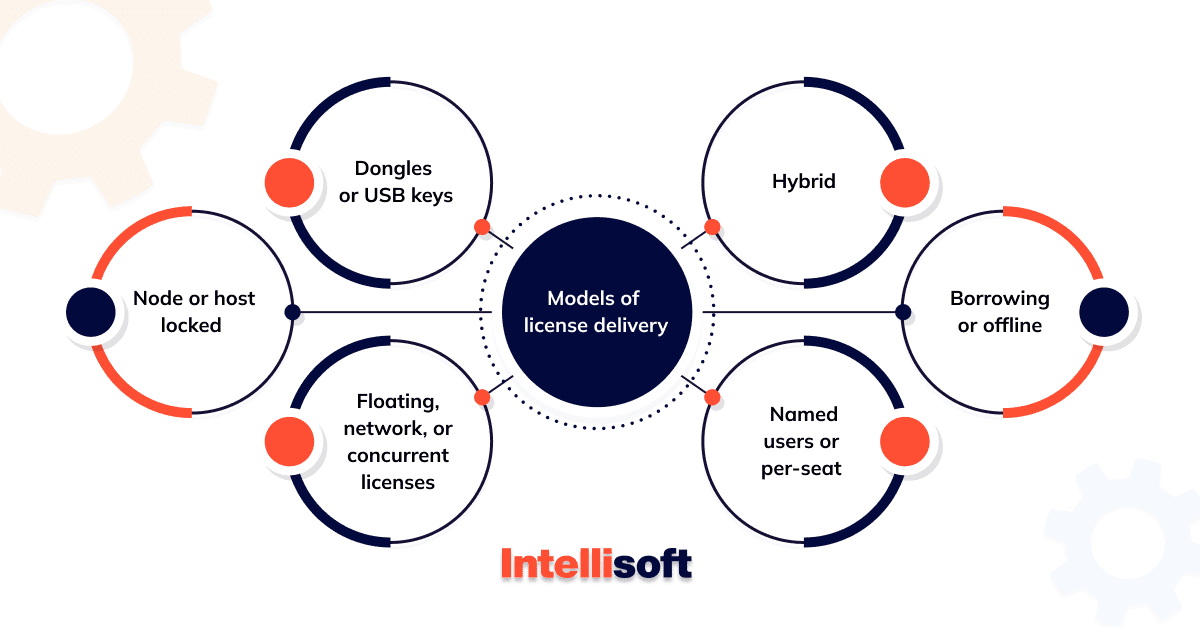
Models of license delivery
- Dongles or USB keys
This type implies that the user connects a physical device to their PC on which the program will be used. Access is provided through a hardware key, which contains the code. Why is it convenient? There is no need to turn to cloud technologies for activation. No Internet connection is required, which reduces the risks too.
Furthermore, your program will be available only to the user who has the key. For example, if a copy of the product is transferred to a third party, they can not use it without a physical key. The limitations of this model are the impossibility of customization and the need for a physical object.
- Node or host locked
According to this approach, the license is tied to a specific node such as a PC, smartphone, or IoT device. Unlike the previous type, you do not need a physical object for activation: just install or download.
The node has a unique identifier that the user enters during setup or first checkout. You get a guarantee that the program will not be transferred to another person and installed on a third-party PC. Due to its features, this model is known as single-use.
- Floating, network, or concurrent licenses
It’s also about code that needs to be downloaded or installed on a PC. However, the difference is that it is available to multiple network users and different devices. If you are looking to improve the security of your intellectual property in software, we recommend that you pay attention to this option.
It is also beneficial if your client wants the software to be available to several employees (or on many devices). For example, 15 out of 150 employees may have access at the same time. By offering a floating model, you ensure the correct distribution of assets between users over time (in turn or depending on demand).
- Named users or per-seat
It is similar to the host node model, but there is a person instead of a computer. What’s the point? A specific user can activate the code. To gain access, it is required to enter your credentials. This approach is also called single-seat.
It makes sense to offer this option if your client is interested in providing access to the product to specific employees (for example, an invoicing tool for accountants or a graphics editor for designers).
- Borrowing or Offline
Such licenses are only valid for the current user and PC for which they were obtained. The license is removed from the free license pool and needs to be returned. The fee is charged for the entire period of its use, which makes this option the most expensive.
The main advantage is that the user does not need to connect to the license server and have a stable Internet connection. That’s why this option is in demand for employees who are often on business trips or are forced to work without access to the network.
- Hybrid
You can combine many of the listed models to adapt to the requirements and wishes of each licensed customer. For example, provide USB keys only to 2 or 3 employees of the client’s company (it is beneficial if there is no stable Internet connection, but you need to secure data) and give the rest access through the cloud. Or offer a per-seat model for specialists from the department who use the program regularly and a concurrent model for those who do it not so often.
Why Software Intellectual Property Protection is Essential for Your Product
Imagine your startup as a nation, and your intellectual property as its treasure vault. Just as Fort Knox guards its gold, your software—rich with innovative code, data, and tools—deserves robust protection. Sometimes, the value emerges even before your development is complete. Picture this: You’ve been coding, gathering data, and developing tools, all aimed at enhancing your project. Suddenly, these “side creations” might sparkle with unexpected appeal, possibly overshadowing your main product. Recognizing and securing their worth is crucial; neglect this, and you might find your competitors have swept them up before you realize their potential.
IP software is any software where the publisher retains intellectual property rights to the source code. Addressing intellectual property software should top the list of priorities for any startup team, ideally resolved among co-founders early on. History is riddled with examples of successful projects that later derailed into years of legal battles and misunderstandings. Consider the infamous Facebook lawsuits involving the Winklevoss twins, which not only led to considerable strife but also inspired a subplot in the award-winning film The Social Network.
However, the goal here is not to script a Hollywood hit but to safeguard your creative assets from the get-go. Effective protection of intellectual property for software is not just a legal shield; it serves as the foundation for your business model and provides motivational leverage for your team. By establishing a solid IP protection strategy, you ensure that your startup’s innovations are secured, preventing any “chip on the shoulder” moments for you and your partners.
Safeguarding the Intellectual Property Protection for Software: Proven Strategies
The risk of intellectual property theft looms in intellectual property rights software development. While having an in-house team might seem like a safer option, it doesn’t entirely eliminate these risks—especially when specialized skills necessitate outsourcing. Fortunately, adhering to best practices can substantially lessen these concerns. Here’s how you can keep your intellectual property management software secure:
Select a Reputable Software Engineering Firm
When it comes to outsourcing, choosing the right partner is crucial. This relationship needs to be a dance of trust and mutual effort. Look beyond technical skills and cost—consider their commitment to provide robust intellectual property software solutions. Evaluate their policies, check for legal expertise, and assess their track record in safeguarding client IP. Make sure they proactively address IP concerns and manage related risks effectively. A reliable partner like IntelliSoft, for instance, ensures that clients are fully briefed on their protective measures and internal processes.
Start with a Strong Non-Disclosure Agreement (NDA)
Before you dive deep into partnerships, secure an NDA. This agreement should clearly define what constitutes confidential information, outline breach consequences, and establish liability. Remember, the lifespan of an NDA can outlast the project itself, making it a fundamental shield for protecting software intellectual property.
Define IP Rights in a Master Services Agreement (MSA)
Common practice in outsourcing involves setting up an MSA, which typically grants exclusive IP rights to the client for all developments during the project. This contract clarifies ownership issues upfront, allowing you to focus more on innovation and less on legal nuances.
Integrate IP Protection Into Your Project Management
Fine-tune your project management to ensure that intellectual property database software protection strategies are meticulously followed. Pay attention to how your project team handles IP in their day-to-day operations. It’s often the small details that can lead to significant breaches, so keep a vigilant eye on compliance throughout the project lifecycle.
15 Key Strategies IntelliSoft Adheres to Provide Intellectual Property Asset Management Software
At IntelliSoft, safeguarding your intellectual property (IP) is a priority. Here is our approach to deciding how to protect software intellectual property:
Company Policies and Procedures
- We adhere to a comprehensive Information Security Policy that underpins all our efforts to protect intellectual property.
- We maintain extensive liability insurance coverage through a reputable U.S. insurer to secure our contractual commitments and professional risks.
- Our in-house legal team provides ongoing expertise, aiding our project and account managers in safeguarding against IP risks.
- We incorporate specific intellectual property rights software protection measures in all client contracts, including NDAs and Master Service Agreements.
- Our operational processes are designed to maintain the confidentiality of client information and project outcomes.
Standards for Staff
- Every team member involved in client projects signs an NDA and receives thorough training on handling IP with care.
- Our project and account managers are well-versed in the nuances of IP management, ensuring meticulous handling.
Information Security
- We protect our IT infrastructure and individual projects with cutting-edge security protocols outlined in our Information Security Policy.
- We ensure the secure exchange of information, both internally and with external partners.
- Access to client resources is strictly regulated, requiring explicit authorization and secure connections.
- Our code repositories are securely managed with daily backups and restricted access, virtually eliminating unauthorized use.
Engagement with Clients
- We initiate all client engagements with a Non-Disclosure Agreement, reinforcing our commitment to IP security from the outset.
- Clients can rest assured that their data is protected against any compromise in confidentiality, integrity, or availability.
- We meticulously verify the legality of third-party software and services used in projects, ensuring compliance and securing necessary client permissions.
- We maintain transparency with our clients about how we protect their intellectual property, addressing any concerns and responding swiftly to queries.
Contact IntelliSoft today to get your software intellectual property protection solution.