Let’s imagine that you hire software engineers to create your IT project. You signed the NDA and the contract and prepared your software requirements specification.
What will come next? How will you ensure that all the tasks are delivered on time?
Will all the features work as expected? The good news is that you shouldn’t control everything. There is a person for that, called the Project Manager (PM) – responsible for assigning taste and tracking overall dev team performance. However, if you want to dig deeper into the software development lifecycle details, you are at the right place.
Being in the software development market since 2007, the IntelliSoft team has delivered numerous successful projects. You can find some of them in our portfolio.
But what is notable about those projects? We apply a secure software development life cycle when developing them. Secure SDLC framework guides secure software development. It encompasses a series of processes and activities aimed at ensuring that software is designed and built with SDLC security considerations at the forefront.
Want to know more about a secure software development life cycle? Read on. In this article, we have gathered the best practices, secure SDLC phases, and processes of secure software development life cycle so that you can leverage our tips for your project.
SDLC is a methodology that will help you achieve all these goals and significantly reduce your development cost while increasing productivity. It’s a plan that eliminates common bugs and pitfalls by evaluating existing systems for weaknesses.
Table of Contents
What Is the Secure SDLC?
It is a framework that reduces the entire set of procedures for detecting and correcting risks and errors. The US National Institute of Standards and Technology (NIST) has calculated that software security lifecycle can reduce the cost of fixing vulnerabilities at the design stage by 15 times.
At the same time, it should be understood that Secure Software Development LifeCycle is a classic textbook risk-based approach. Its implementation doesn’t eliminate vulnerabilities completely; it only reduces them to the minimum acceptable level.
Why Does SDLC Matter?
SDLC is the best software development and testing solution if you want to fix defenselessness at an early stage.
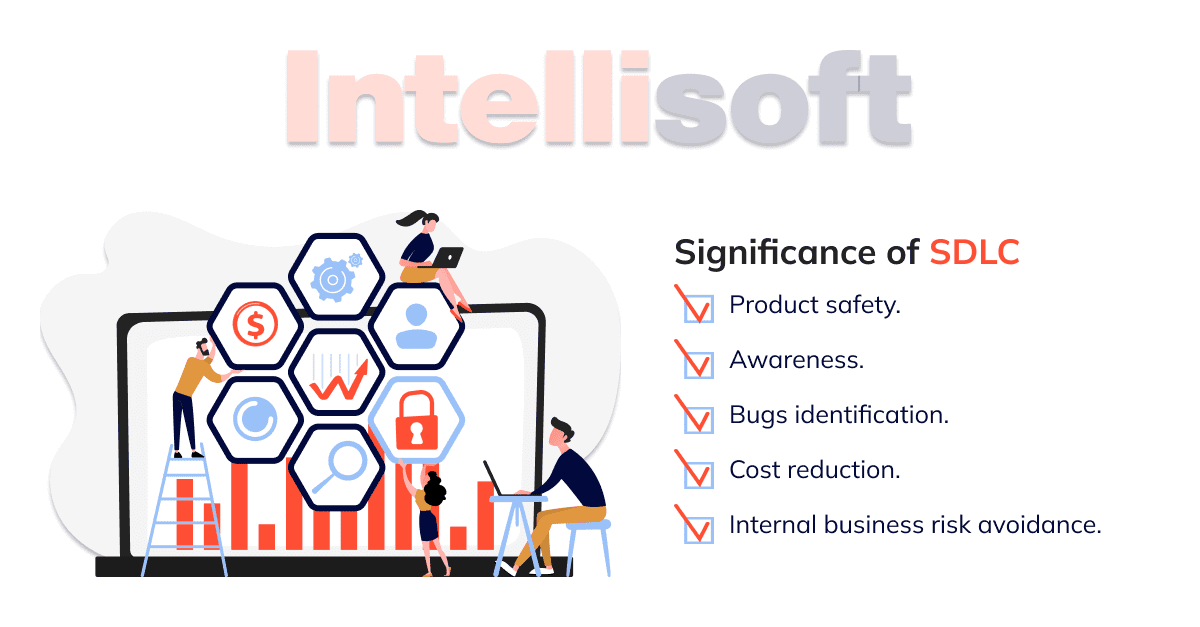
Secure Software Development Life Cycle includes comprehensive architecture, code, and build reviews. It provides several benefits for your product:
- Product safety.
- Awareness.
- Bugs identification.
- Cost reduction.
- Internal business risk avoidance.
In fact, SDLC can steer your workflow in the right direction by reducing risks and costs.
SDLC Practices: A Brief History and Evolution of Models
The Secure Software Development concept emerged in the 1960s when there was a need to manage complex business systems efficiently. Massive corporations tried to develop frameworks to structure massive data, multifactorial processes, analysis processes, and implement other SDLC practices.
Also, new secure development models began to appear together with this concept.
SDLC and Application Security
All of our applications can be weak to vulnerabilities in one way or another. This, in turn, can lead to financial losses and provoke customer data leakage.
SDLC security is being applied as a concern at every stage of development. It is a methodology that involves automating software security checks by embedding this secure SDLC process into the application at the development stage.
In fact, Microsoft spoke about this approach to software development in 2004, but companies have only recently begun to resort to secure development lifecycle in their work.
This system development life cycle methodology allows developers to identify and fix most vulnerabilities before release, keeping applications secure. Moreover, the cost of this service is several times less than the cost of correcting errors after a low-quality product release.
Related readings:
- Time-Saving Success: Crafting the Perfect Scheduling App from Concept to Launch
- Step-by-Step Guide to Integrating a Paperless Document Management System
- RabbitMQ vs Kafka: Choosing the Right Messaging System for Your Needs
- Story Point to Hours: Which Estimation Approach to Choose?
- Making Sense of Databases: How to Choose the Right One
What are the Secure Software Development Life Cycle Processes?
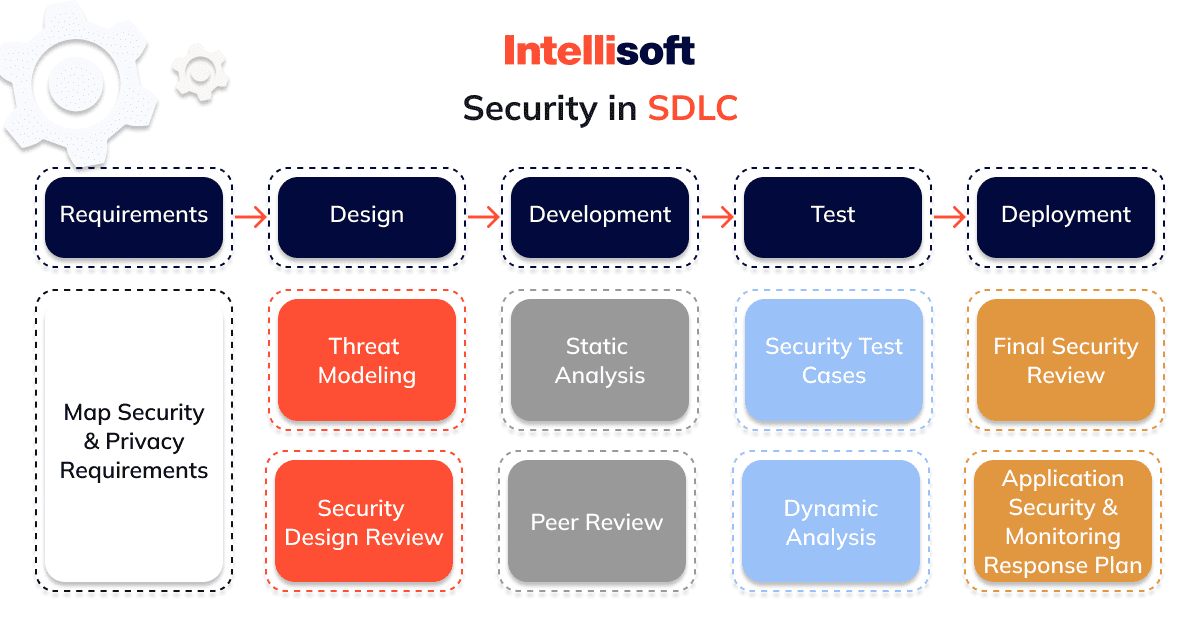
Integrating security into the Software Development Life Cycle (SDLC) transforms every step of secure software engineering. Adopting a security-focused mindset from the start ensures that potential vulnerabilities are addressed early on, during the requirements and development stages. This proactive approach not only boosts efficiency but also cuts costs dramatically compared to fixing issues after the secure software has been deployed. Essentially, embedding SDLC security means that it becomes a fundamental aspect of secure SDLC phases.
Emphasizing security throughout the SDLC isn’t just a philosophy—it’s a practical necessity. Although the security tasks vary by phase, the commitment to a secure foundation is crucial and requires a collective effort from all team members. This integrated approach ensures that security is not an afterthought but a prime consideration throughout the entire secure software development process.
6 Secure SDLC Phases and Processes
The concept has a precise sequence and is divided into six stages of SDLC. Of these, the first three secure SDLC phases prepare the project and answer the main strategic questions. Meanwhile, the last three stages are optimized to implement the points in the secure SDLC checklist.
Stage 1. Analysis
At this early stage, requirements for new features are collected from various stakeholders. Identifying any security considerations for collecting functional requirements for a new release is essential.
Stage 2. Planning
You will review the security requirements and considerations and answer questions such as:
- What do you want to do?
- What should be your final product?
This stage also involves an analysis of possible risks and shortcomings.
Stage 3. Architecture and Design
This is the moment when you and the stakeholders answer the question “How will you achieve your goals in the SDLC security checklist?” that you posed in the previous step. It includes two key steps:
- High-Level Design (HLD).
- Low-Level Design (LLD).
Participants also develop data specifications, components, structure, and processing at this stage.
Stage 4. Software Development
Now that you know what you want and how it should look, you can move on to implementing your plan. So, engineers are involved in the process and create a system with the help of code and the necessary technologies.
Customers also have the opportunity to look at the future product and evaluate all the operational functions.
Stage 5. Testing
Quality checks are the next step after its creation. At this moment, you test the technical requirements, all code fragments, device compatibility, and security conditions.
Checks and testing will occur until you receive the product you see in your plans.
Stage 6. Secure Software Deployment
The final stage is where you update and release the application. It is necessary to maintain the app regularly, make the necessary updates, support, change and expand it.
5 Popular SDLC Models and Their Pros and Cons
Today, companies and startups use dozens of different schemes. Each secure development model has specific pros or cons. Among them, there are SDLC best practices — the most popular six models used according to a particular situation.
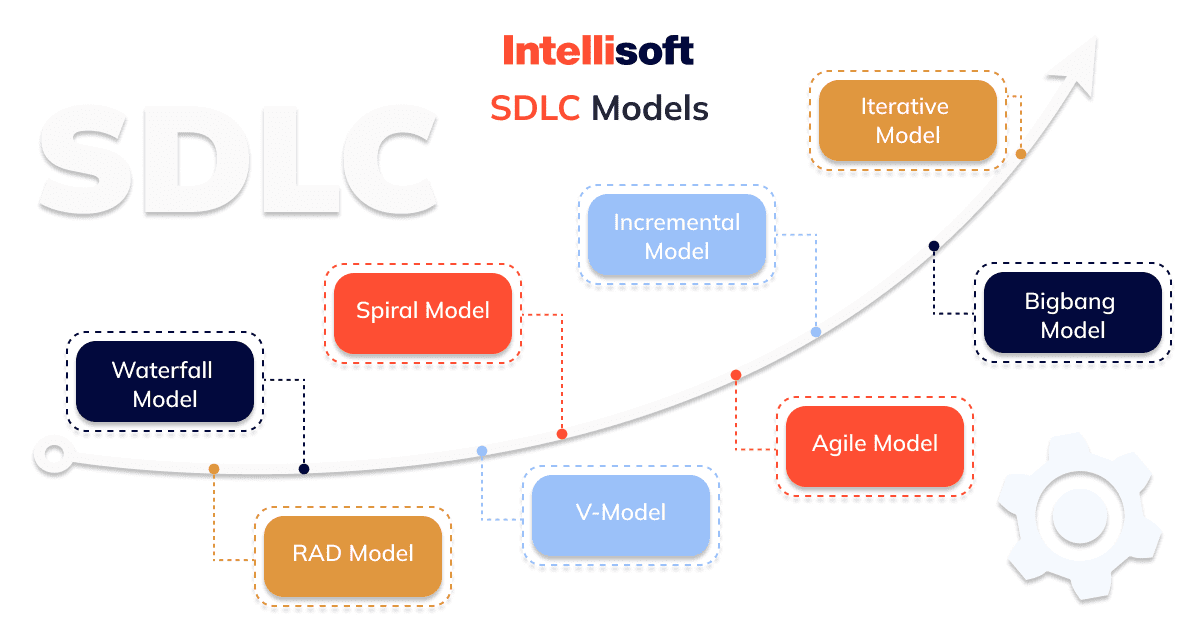
Waterfall Model
It is one of the main and most popular models. It provides organized control over the project. Waterfall Model pros lie in the following:
- Advanced planning.
- Minimal risks.
- Clear structure.
As for the cons, there are not so many of them:
- This model is not subject to change.
- Inconvenient for long and complex projects.
This security development model is easy to understand and implement and has been the go-to model for a few decades (it was formed in the 1970s).
V-Shape Model
This model has become the next step in secure development lifecycle models. It was created in Germany in the 1980s for defense projects and provides a more in-depth approach thanks to several features:
- It separates the secure development lifecycle phases.
- Great for time management.
- Stable testing.
- Timely detection of bugs.
- Clear separation of secure SDLC phases.
However, the V-Shape Model has some disadvantages:
- High risks.
- Difficult to be flexible.
- It has no prototypes.
This security development model is ideal for projects where accuracy is critical.
Iterative Model
When the Waterfall model failed to meet the challenge, the IT community created a new scheme in 1975. This was an innovation because the Iterative Model paved the way for new control models. What advantages does it have:
- Simple and transparent reporting of the process.
- Modification flexibility.
- Adaptability.
- Low risks.
Of the shortcomings, it has such moments as:
- Incompatibility with changing requirements.
- Rigid iterations
The Iterative Model is only suitable for large projects!
Spiral Model
If you are looking for a security system development life cycle model for software with vague requirements, this model is just what you need.
It is a model hybrid that directs a command to accept elements of one or more secure development lifecycle models, such as a waterfall or an iterative model. Spiral Model pluses are as follows:
- Excellent risk management.
- Flexibility in control.
- Well-documented focus.
At the same time, it should be borne in mind that this is a relatively expensive model and requires special knowledge and skills.
Agile Model
This is the youngest and most popular system. It is designed to cut down on bureaucracy. This methodology appeared in the 1990s, and today we know about 50 of their types. Why the Agile Model is so good:
- Flexible system.
- Rapid reaction.
- Prompt delivery.
- Close collaboration between stakeholders.
However, this methodology is not suitable for large teams (15 members or more).
Why SDLC is Useful for Business
Whether you’re building a company, a tool, a complex program, or a completely new product, SDLC is good for ensuring quality and focus on users. Why?
Because it is used for several purposes at once:
- To help reduce time to market.
- Providing better performance.
- Save money and increase the potential value of your product for the stakeholders you care about.
SDLC security best practices are especially helpful in secure software engineering because it forces you to work within strict limits.
In other words, it’s a methodology for doing the right things at the right time for the right reasons. The SDLC will get you to follow every step you need to take.
Think of the SDLC as a blueprint for success: blindly following it doesn’t guarantee you anything, but it increases the likelihood of being happy with the results.
SDLC Ensuring and Implementing
What ensures decent app development and SDLC security? First of all, these are suitable sequences and tools:
- Safe programming practice.
- Carrying out autotests.
- Code analysis is dynamic.
- Pentests for checkings and penetration.
- Functional testing.
- Testing protocols.
- Threat monitoring.
An important role is also played by timely registration for incidents.
Also, a fairly common tool for ensuring secure software development, which can be used at all secure SDLC phases (starting from the fourth in this case), is static SAST. It comes down to code analysis without running the program, which means it is guaranteed to be suitable for secure development, testing, deployment, and operation stages.
How to Ensure SSDLC?
Creating a secure software development lifecycle isn’t just about coding; it’s about shaping the way your team thinks and works. Here’s how you can make security a cornerstone of your security software development process:
Embed Security in Your Culture
Start by shifting the mindset of your developers. Security needs to be a priority from the ground up, influencing every stage of your project. This might mean embracing new cultural norms within your teams, along with introducing automated checks and processes that reinforce SDLC best practices throughout the development life cycle.
Tailor Your Approach
There’s no one-size-fits-all solution for SecSDLC. The strategy that works best for you will depend on the unique strengths and challenges of your development team. This personalized approach ensures that security measures are not only effective but also integrated seamlessly into your existing processes.
Manage Change Wisely
Transitioning to a secure software development lifecycle means more than just new tools; it involves a fundamental change in your organizational culture. This transformation requires careful management, ensuring that all teams across various business units are onboard and aligned with the new security-focused direction.
5 Best Secure Software Development Cycle Process Practices
Without going into the full checklist, you can adopt these five SDLC best practices to ensure a smooth, secure development lifecycle and optimize your work. Which of the following secure SDLC phases does the SECSDLC involve? All of them:
- Education. Developers should develop skills and knowledge in SDLC and SSDLC for clear guidelines for problem detection and resolution and an understanding of secure coding.
- Specific requirements. Explicit requirements are the basis for any secure lifecycle management success. You must be as concise and clear as possible in your recommendations and safety guides. It is important that all project participants offer their solutions.
- Development. It applies to everything: the team’s thinking, growth, and communication. Teams are ready for a change in interaction due to secure development lifecycle, so the developers and the security team must work together, allowing each other to fulfill the obligation.
- Initiative. It means that you can use additional initiatives like DevOps or DevSecOps.
- Priorities. Sort and distribute attention in solving problems. This aims to prevent security issues from entering the production environment and ensure that existing vulnerabilities are sorted out and fixed over time.
So, secure SDLC framework can become your guide, or rather, the way to achieve the goal of a “cool product.” It is a multi-factor framework that will improve and speed up secure development and release and provide reliable app security.
Conclusion
The traditional approach of testing for vulnerabilities only after an application is in production simply doesn’t cut it anymore. The landscape of cyber threats is constantly evolving, demanding a more comprehensive approach to securing applications. Here’s how you can create secure software from the ground up:
- Start Early: Embed security considerations right from the requirement gathering stage. By addressing potential security concerns at the beginning, you’re setting a solid foundation.
- Cultural Shift: Cultivate a team culture that prioritizes security. This shift will influence all aspects of your development process, ensuring security is never an afterthought.
- Automate Security Checks: Integrate automated security verification into your deployment process. This helps catch vulnerabilities early and often, before they become bigger issues.
- Adopt a Secure SDLC: Embrace a Secure Development Lifecycle that incorporates security at every stage—from planning to deployment. This holistic approach ensures that security is woven into the fabric of your application’s development.
By shifting the focus of security leftwards to the very inception of project requirements, secure SDLC phases allow you to tackle security issues at their root, rather than scrambling to patch them during maintenance phases. This proactive approach not only enhances the security of your application but also provides peace of mind knowing that you’ve built your system on a secure foundation.