Looking for Cyber Security expert?
In recent years, the adoption of Software-as-a-Service (SaaS) has skyrocketed, revolutionizing how businesses operate and manage their applications. But, with this rapid growth comes the emergence of complex safety challenges that organizations must confront to safeguard their data and maintain customer trust. A recent survey highlights data leakage protection, access control, and password management as the main concerns related to SaaS security, emphasizing the need for businesses to stay vigilant and informed.
IntelliSoft, a cloud application development and security services provider understands the importance of SaaS security and its unique challenges. With over a decade of experience and a dedicated team of highly-qualified experts, we have gained valuable knowledge in the subject and now want to share some insights and best practices to help you protect your SaaS applications and ensure a firm safety policy.
Table of Contents
Why Do Companies Need Cybersecurity?
In today’s digital landscape, companies increasingly realize the importance of cybersecurity. With cybercrime projected to cost the globe $10.5 trillion annually by 2025, businesses are scrambling to protect their assets and customer data. Any data breach can cost a company millions of dollars, not to mention its devastating impact on customer trust and your company’s reputation. Let’s explore the reasons behind the need for robust cybersecurity and discuss some of the most common SaaS app safety issues businesses face today.
What is Software as a Service (SaaS)?
SaaS is a software licensing and delivery model where applications are hosted centrally on the cloud and provided to users on a subscription basis. Instead of installing and maintaining software on individual devices, users access these applications online, usually via a web browser. SaaS providers handle all the technical aspects, such as infrastructure, maintenance, updates, and security, allowing businesses and users to focus on their core tasks without worrying about software management. Examples of popular SaaS applications include Microsoft 365, Salesforce, and Google Workspace.
SaaS App Security Issues
As SaaS applications become more popular, they become more attractive targets for cybercriminals. Let’s review some of the most common SaaS app safety issues that businesses need to address:
Security Misconfiguration
Incorrectly setting up computing assets can lead to vulnerabilities that allow attackers to exploit the system. Companies must configure every tool properly and update them regularly to prevent threats.
Too Many Controls
Overly permissive access rights can put sensitive data at risk. Companies should avoid granting unnecessary access rights to end users and regularly review access permissions to prevent data breaches.
Underinvestment in SaaS Security Tools and Staff
Inadequate investment in SaaS security tools and staff can leave a company vulnerable to cyberattacks. Companies should prioritize investment in safety tools and personnel to avoid cyber threats.
Non-use of SSPM (SaaS Security Posture Management) Tools
SSPM tools are essential for monitoring and managing the security posture of SaaS applications. Businesses must use these tools to avoid security breaches and non-compliance with industry regulations.
Cross-site Scripting (XSS)
XSS attacks are a common security vulnerability that impacts nearly two-thirds of all SaaS applications. They allow attackers to inject malicious code into web pages viewed by users, potentially leading to session hijacking and other security breaches.
Identity Theft
Online transactions, such as credit card payments, can expose users to identity theft. Companies should use security tools like LDAP, firewalls, and encryption to protect sensitive information during transit and at rest.
Insufficient Logging and Monitoring
Companies risk overlooking unauthorized activities that could lead to data breaches without proper logging and monitoring. Regularly monitoring and auditing logs can help identify and prevent malicious activities.
Securing SaaS applications is paramount in today’s digitally driven business environment. Tackling prevalent security concerns associated with SaaS apps helps protect your valuable assets, preserves customer trust, and steers clear of the expensive repercussions of a data breach. By consistently evaluating risks and adopting industry best practices, you can maintain a proactive stance against cybercriminals and safeguard your SaaS applications from constantly evolving cyber threats.
Top SaaS Security Threats to Look Out For
SaaS businesses face a multitude of potential threats and risks to their platforms. Awareness of these challenges is crucial to protecting sensitive data and maintaining customers’ trust. Let’s discuss the most significant SaaS security threats you should know and understand how to mitigate them.
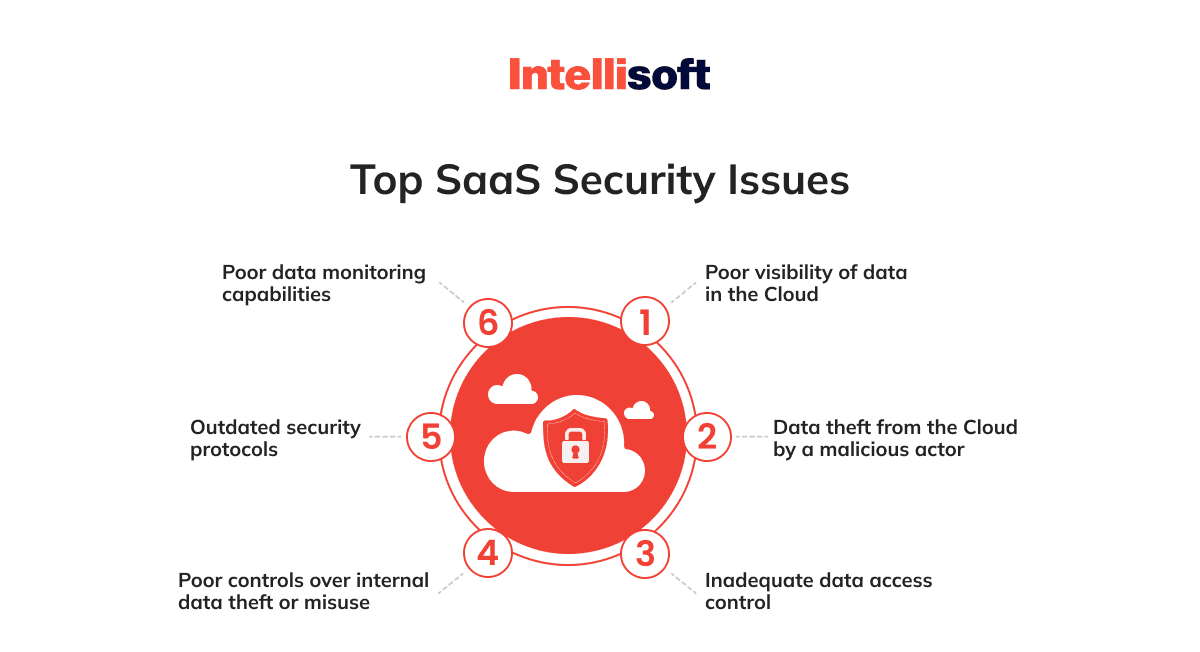
Phishing
Phishing attacks are a common concern, as over 90% of cyberattacks begin with phishing emails. Cybercriminals use these deceptive messages to trick users into exposing sensitive data or downloading malicious software.
Account Takeovers (ATOs)
ATOs involve threat actors compromising an employee’s corporate credentials, often through credential phishing campaigns or purchasing stolen credentials on the Dark Web. Once an attacker gains access to an account, they can cause significant damage to the organization.
Data Access Risk
Entrusting sensitive data to a third party, such as a SaaS provider, inherently carries some risk. Businesses must ensure their SaaS providers follow strict security protocols to protect this data from unauthorized access.
Lack of Transparency
Service providers may not always be transparent about their security practices, making assessing the risks involved in using their services challenging. Before choosing a SaaS provider, you should request clarity on safety measures and protocols.
Inadequate Federated Identity Management
Employees may have multiple identities across different SaaS providers. When an employee leaves the company, automatically shutting off access to all these accounts may not be possible, increasing the risk of unauthorized access.
Weak Service Level Agreements (SLAs)
Insufficient SLAs and contracts can make it difficult to hold parties accountable in the event of a security breach. Companies should negotiate robust SLAs that clearly outline security responsibilities and expectations.
Vendor Lock-in
The lack of interoperability among vendors can put businesses at risk if a SaaS provider goes out of business or gets acquired by a competitor. When selecting SaaS providers, consider vendor lock-in risks and plan for contingencies.
Identity Theft
Poor access management and inadequate security solutions can lead to identity theft and unauthorized access to company data compromising sensitive user information.
Data Theft
Data breaches pose a significant risk to SaaS businesses, as they often store sensitive information, such as financial data, customer records, intellectual property, and personally identifiable information. Cybercriminals typically target attacks to exfiltrate this valuable data.
Outdated Security Standards
SaaS providers who maintain outdated security standards increase the risks associated with data safety. Companies should verify that their SaaS providers adhere to modern security standards to minimize potential threats.
Emerging Malware and Zero-Day Threats
Cybercriminals are constantly developing new malware and exploiting previously unknown vulnerabilities, known as zero-day threats. SaaS businesses must stay vigilant and prepared for these ever-evolving risks.
Compliance and Audits
Failing to adhere to government mandates and industry-specific regulations, such as GDPR, PCI DSS, HIPAA, and SOX, can result in hefty fines and reputational damage. SaaS businesses must comply with all relevant regulations to avoid costly penalties.
Insider Threats
Security risks can also come from within an organization, including malicious intent, user negligence, sharing credentials, and weak passwords. Companies must establish solid internal security practices and train employees to minimize these risks.
Increasing organizational awareness of security risks is vital to mitigating and eliminating potential threats. By assessing risks and implementing intelligent controls, you can significantly enhance the security of your company’s SaaS applications, protect valuable data, and maintain the trust of your customers.
Understanding SaaS Security Checklists
A SaaS security checklist is a step-by-step guide to help companies build user trust and enhance their application safety at a reasonable cost. These checklists offer security guidelines that outline best practices and standards for SaaS and cloud-based apps. Executives, including Chief Technology Officers (CTOs) and Chief Security Officers (CSOs), utilize these checklists to assess current SaaS tools and evaluate potential new solutions.
Businesses providing SaaS as a B2B platform can also apply these checklists to ensure their software meets their customers’ required security standards. Some lists could be general and flexible, while others cater to specific industries or use cases.
The Function and Application of SaaS Security Checklists
SaaS security checklists are a reference point for organizations evaluating their safety measures. Companies can use an existing checklist to assess their current SaaS tools, evaluate new solutions, or create custom checklists tailored to their unique needs and goals.
Generally, SaaS security checklists aim to evaluate an organization’s current safety measures and ensure robust standards moving forward. Although checklist items may vary, the categories that each list should cover include the following:
- Sensitive data protection
- Protection for employees
- Customer protection
- Securing the SDLC and deployment
- Infrastructure protection
- Ensuring compliance with regulatory requirements
Let’s take a closer look at each of them.
Sensitive Data Protection
Data safety is a critical aspect of any SaaS security checklist. Protecting the main SaaS application and database from breaches and attacks is paramount. Lists should contain items that strengthen data integrity, monitor application databases for signs of violations, and outline data deletion policies.
Protection for Employees
Checklists should provide steps for employee education and training. Implementing multi-factor authentication, role-based access controls, and other permissions can protect employee accounts from being compromised.
Customers Protection
Organizations using SaaS software to interact with customers and store their data must ensure that the software and databases are robust enough to protect sensitive customer information and comply with relevant standards.
Securing the SDLC and Deployment Process
SaaS vendors should include action items in their checklists that pertain to each phase of the development process, helping to perform effective security reviews at each stage. Using dedicated SaaS on cloud providers like Amazon and Google can facilitate secure deployment.
Protection for Your InfrastructureA SaaS security checklist should consider the entire IT infrastructure. You would want to ensure that a single breach on one part of a single SaaS application doesn’t compromise the whole network or infrastructure.
Ensuring Compliance
Government requirements and industry-specific mandates are critical components of SaaS security. Compliance with such regulatory standards as GDPR, CCPA, PCI DSS, HIPAA, and SOC 1 and SOC 2 should be a part of the checklist.
Utilizing SaaS security checklists is essential for businesses to assess their existing safety protocols, implement industry best practices, and adhere to proper regulations. By leveraging these checklists, your organization can considerably improve the security of its SaaS applications, safeguard critical data, and uphold the confidence of its customers.
Related readings:
- What Threatens Your Web Application Security
- What Are the Security Risks of Cloud Computing? Threats & Solutions
- What is Cloud Computing? Understanding the Basics, Services and Benefits
- What Is a Secure Software Development Life Cycle? Stages, Methodologies, and Best Practices
Security Checklist for SaaS Applications
To ensure the security of your SaaS application, you should follow a comprehensive checklist that covers the most critical aspects of cloud SaaS security. Here are the main steps to follow:
1. Implement robust access control:
- Develop and enforce password policies.
- Use multi-factor authentication (MFA) for added security.
- Implement role-based access controls and privileged access management.
2. Conduct regular security assessments:
- Perform vulnerability analysis and threat risk modeling.
- Conduct penetration testing to uncover weaknesses.
- Continuously monitor and review your security posture.
3. Encrypt sensitive data:
- Use data encryption and tokenization to protect sensitive information.
- Ensure encryption at rest and in transit.
4. Monitor user activity:
- Log and monitor user actions to detect potential security breaches.
- Use real-time alerts and notifications for unusual activities.
5. Keep software up to date:
- Regularly update your SaaS application and underlying infrastructure.
- Apply security patches promptly to minimize vulnerabilities.
Examples of SaaS Security Checklist Questions
To help you evaluate your SaaS application’s security, here are some example questions to consider:
- Are strong password policies enforced for all users?
- Is multi-factor authentication implemented and required?
- Is sensitive data encrypted both at rest and in transit?
- Are regular security assessments and penetration tests conducted?
- Are software updates and security patches applied promptly?
SaaS Implementation Checklist
When implementing a new SaaS solution, following a structured approach is crucial. Here is a list of steps to consider during the implementation process:
- Evaluate the SaaS solution for compliance with relevant security standards (e.g., GDPR, PCI DSS, HIPAA).
- Develop a detailed security guide, including risk assessment, security controls, and strong security culture.
- Implement a secure Software Development Life Cycle (SDLC) with safe coding practices, vulnerability analysis, threat risk modeling, and penetration testing.
- Establish automated backups for disaster recovery and business continuity.
- Configure security controls, including identity and access management (IAM), data encryption, malware prevention, data loss prevention, and logging and monitoring.
- Train employees on security best practices and promote a security-conscious culture within the organization.
- Monitor and review the SaaS solution’s security regularly to ensure ongoing protection against emerging threats.
After implementing the SaaS solution, it would be reasonable to maintain its safety through ongoing efforts. Keep up with the latest security trends and best practices and update your strategy in response to evolving threats and risks.
Schedule regular internal and external security audits to verify compliance with security policies and industry standards. Encourage your employees to identify and report potential issues proactively.
By maintaining a focus on security even after implementing the SaaS solution, you can ensure that their applications remain protected against the constantly evolving landscape of cyber threats.
SaaS Security Best Practices Essential for Protecting Cloud Applications
The increased risk of cyber threats and data breaches comes with the growing adoption of SaaS. SaaS providers must implement robust safety measures to ensure user data security and privacy. It’s time to review essential SaaS security practices, from access control and authentication to data encryption and modern cloud security mechanisms.
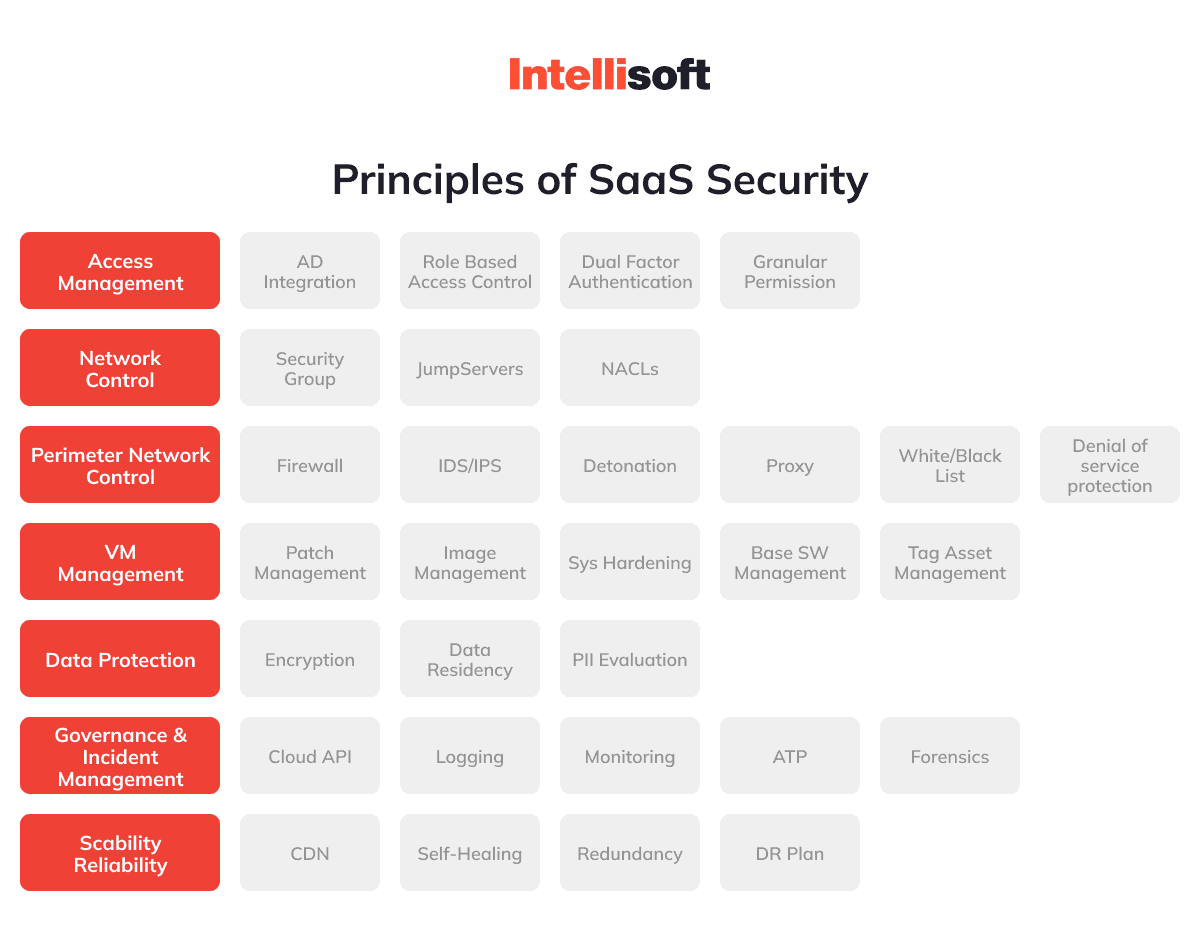
1. Create a Comprehensive SaaS Security Checklist
Develop a checklist that addresses potential security flaws, SaaS security standards, and internal measures to promote safety. Collaborate with software developers, stakeholders, and domain experts to establish a robust security checklist and ensure it stays up-to-date and accessible. Incorporate multiple levels of security, such as organizational policies, employee education, and customer education.
2. Adopt a Secure Software Development Life Cycle
Integrate security activities at every stage of the development process, from incorporating SaaS application security requirements to employing secure coding methodologies and penetration testing. Utilize DevOps security and a CI/CD pipeline for the fast delivery of features and fixes, including safety-related updates.
3. Establish a Shared Responsibility Model
Define clear roles and responsibilities between your organization and customers for SaaS security. SaaS providers must handle the infrastructure, network, operating system, and application while their customers manage their data and identity. It would be wise to separate duties and accounts within your operational teams.
4. Enhance Data Protection at Customer and End-User Levels
Implement security protocols like role-based permissions, access control, and the rule of minimal privilege to reduce internal security gaps. Only administrators should have unrestricted access to sensitive data and the ability to decide which users receive specific permissions. Utilize multi-factor authentication (MFA) to minimize entry points for attackers.
5. Conduct Thorough SaaS Security Testing
To identify and address vulnerabilities:
- Engage in comprehensive security testing, including automated, manual, and simulated attacks.
- In addition to standard quality assurance and automated testing, perform security-specific testing using tools like static application security testing (SAST) and resources like OWASP Top 10 security issues.
- Consider employing external professional penetration testers to audit your SaaS platform thoroughly.
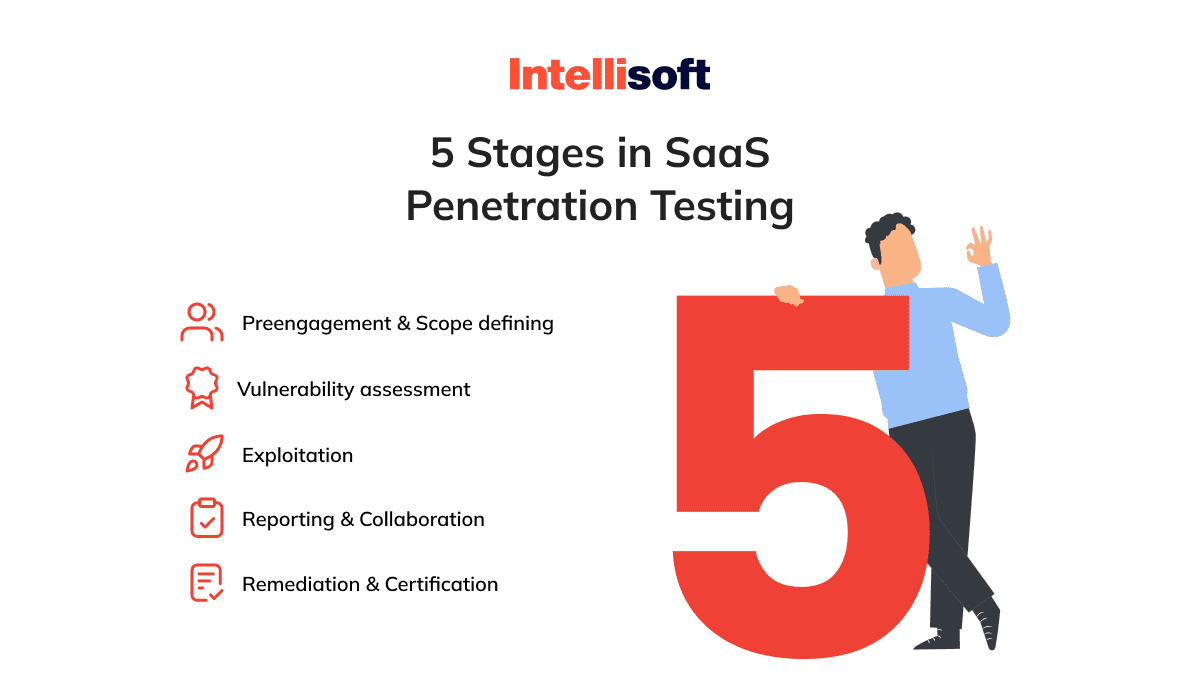
6. Obtain Certifications and Conduct Audits
Obtain certifications like PCI DSS to demonstrate secure data transmission, processing, and storage. Perform audits, such as SOC 2, to evaluate security, processing integrity, and confidentiality controls. Create data retention and deletion policies in compliance with regulations like GDPR and ensure customers are aware of these policies. Monitor industry standards and regulations to maintain compliance and address security gaps.
7. Incorporate Real-Time Protection
Integrate real-time monitoring to detect malicious attacks and use tools such as firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) to enhance security. Implement automatic logging mechanisms and procedures to investigate potential security breaches. Consider data loss prevention (DLP) systems to protect sensitive information and enable customers to perform regular monitoring or audits.
8. Choose a Secure SaaS Application Deployment Method
Opt for self-hosted deployment or cloud deployment through vendors like Amazon or Google. Ensure adherence to vendor-recommended best practices and compliance with relevant security principles and standards— research certifications and documentation before selecting a cloud services provider.
9. Secure Your Virtual Machines (VMs)
The security of both on-premises and cloud-based VMs has become a pressing concern. You must have a strategic plan to maintain a secure infrastructure and prevent unauthorized access to your VMs and other company assets. Ensure the guest operating system of the VM is up-to-date with the latest patches — disable unnecessary or seldom-used features. Activate the secure boot feature.
10. Utilize Data Encryption
Implement robust data encryption techniques for data at rest and in transit to safeguard against data breaches. Establish secure encryption protocols ensuring that sensitive information remains protected from unauthorized access. Provide customers with the ability to manage their encryption keys as an added layer of security. This approach bolsters overall data security and fosters trust between the organization and its customers, demonstrating a commitment to maintaining the confidentiality and integrity of their information.
11. Use Reliable Cryptography Tools
Utilize top-tier cryptography libraries, mechanisms, and tools to ensure strong authentication and encryption processes. You may be interested in looking into Java Cryptography Architecture (JCA), CertMgr.exe, and SignTool.exe. By leveraging these trusted resources, you can bolster the security of your data and communications, effectively mitigating the risks associated with unauthorized access and tampering.
12. Adopt Modern Cloud Security Mechanisms
Consider the Secure Access Service Edge (SASE) model, which includes components like Zero-trust network access (ZTNA), Software-defined vast area network (SD-WAN), Firewall-as-a-service (FWaaS), Cloud access security brokers (CASBs), and Secure web gateways (SWG) for advanced data protection.
13. Implement SaaS Security Posture Management (SSPM)
You can use SSPM tools to monitor SaaS applications for configurations, user permission settings, and compliance. These tools automatically detect and mitigate security risks, such as misconfigurations, excessive user permissions, and inactive accounts.
SaaS security is paramount to protecting user data and maintaining customer trust. By focusing on access control, data encryption, and adopting modern security mechanisms, you can safeguard your SaaS applications against potential threats and ensure a secure and reliable experience for their users. By implementing the recommended practices discussed in this article, you can enhance the safety of your SaaS apps and stay compliant with industry standards and regulations. Remember, a robust security strategy requires ongoing monitoring, updates, and improvements to stay ahead of the ever-evolving cybersecurity landscape.
Top 5 Cyber Security SaaS Solutions
Let’s review the top five cybersecurity SaaS solutions available today. These solutions help organizations protect their data and applications from potential cyber threats.
Let’s review the top five cybersecurity SaaS solutions available today. These solutions help organizations protect their data and applications from potential cyber threats.
- Astra Security
Astra Security offers a comprehensive suite of security tools for businesses of all sizes. It includes firewall, malware, intrusion detection and prevention, vulnerability scanning, and more. Astra Security’s user-friendly interface makes it easy for businesses to manage their security needs effectively. - Cipher
Cipher is a leading cyber security SaaS solution that provides a wide range of security services, including managed security services, threat intelligence, incident response, and consulting. Cipher’s platform helps organizations protect their assets, detect threats, and respond to incidents in real-time. - Intruder
Intruder is a powerful SaaS security platform that helps businesses identify and remediate system vulnerabilities. Intruder continuously checks for security flaws with its automated scanning capabilities, ensuring your applications and infrastructure remain secure. Its intuitive dashboard allows users to manage and prioritize vulnerabilities easily, minimizing potential cyberattack risks. - Fidelis Cybersecurity
Fidelis Cybersecurity offers a comprehensive cybersecurity platform that combines network, endpoint, and cloud security solutions. It detects, analyzes, and responds to advanced threats and data breaches. Fidelis provides organizations with the tools to protect their assets, monitor networks, and maintain a strong security posture. - Tenable
Tenable is a well-known SaaS security solution focusing on vulnerability management and compliance. Its platform helps organizations identify, prioritize, and remediate system vulnerabilities. With its continuous monitoring capabilities, Tenable ensures that businesses stay on top of their security needs and maintain compliance with industry regulations.
How to Choose the Best SaaS Security Solution for Your Organization
To select the most appropriate SaaS security solution for your business, consider reviewing the factors below.
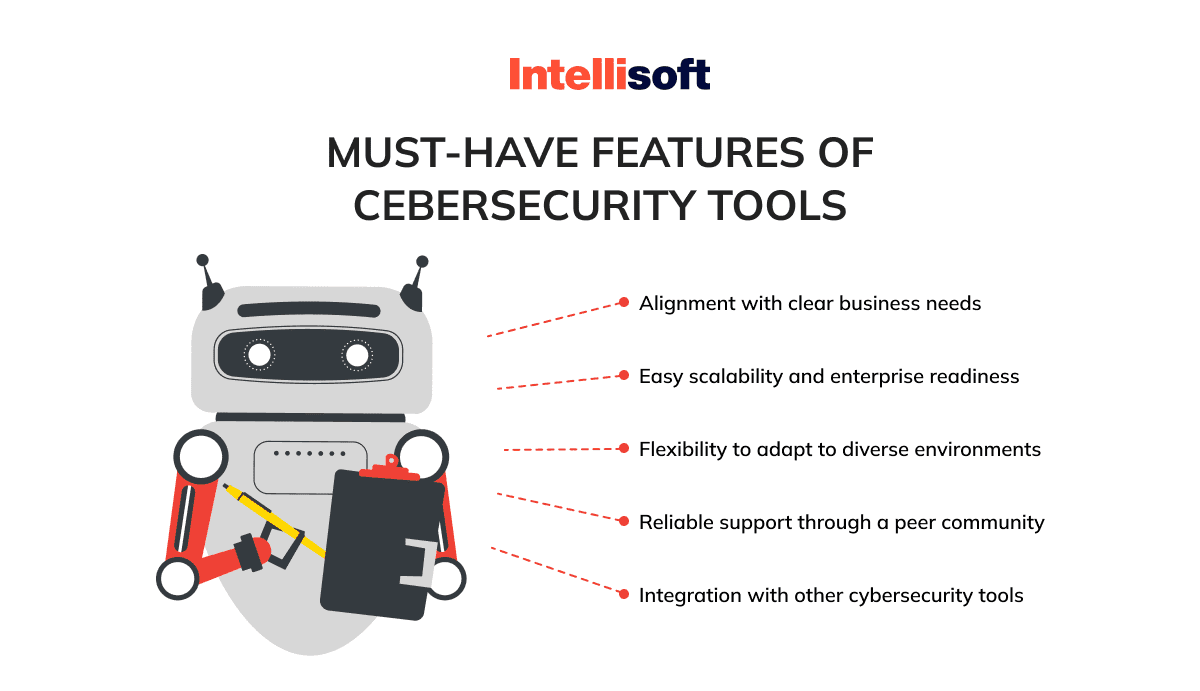
Customization
Choose a SaaS security vendor that allows you to customize access and monitoring policies, offers robust reporting and backup management capabilities, and combines the benefits of automation with autonomy for clients.
Performance
Ensure that the SaaS security solution offers fast performance without compromising security measures. Avoid providers that cause slowdowns or require you to reduce encryption and access protections.
Transparency
Opt for providers with clear privacy and data storage policies, a strong track record with regulators and customers, and that store the minimum amount of data necessary for their services.
Edge Security
Select a SaaS provider that takes network edge security seriously, offering tools like firewalls, authentication, real-time monitoring, and tailoring security strategies to your needs.
Scale
Look for SaaS partners that can scale their operations according to your business growth without sacrificing network security.
Support
Choose a SaaS provider that invests in quality support teams to help you onboard security tools and maintain cloud services. Prioritize companies that you trust and avoid basing your decision solely on cost.
Choosing the right SaaS security solution for your organization cannot be overstated. With an ever-growing number of cyber threats, investing in a robust security platform that aligns with your organization’s specific needs and goals is crucial. Remember that the cheapest option may not be the best – prioritize quality and trust when selecting a provider.
Conclusion
Throughout this article, we have examined the vital role that SaaS security plays in protecting businesses from cyber threats. We have discussed the importance of creating a solid security architecture, promoting a security-first culture, and ensuring compliance with industry standards and regulations.
As the situation on the digital scene evolves, businesses must stay vigilant and proactive in addressing security concerns. By implementing the best practices and investing in a reliable SaaS security solution, you can substantially reduce the risk of data violations and cyber-attacks, protecting your business and ensuring its success in the long run.
If you need a reliable tech partner that understands your organization’s unique needs consider partnering with IntelliSoft. Whether you require a single specialist, a dedicated team, or an entire R&D center, IntelliSoft is committed to delivering senior tech talent and solid development expertise to build world-class products, including comprehensive and tailored SaaS security solutions.
We can provide professional cloud consulting services to guide your path from premises to the cloud. We can also take care of cloud security, analyzing and preventing cyber threats in real-time 24/7 to block unauthorized access, data breaches, and account compromises.
Don’t leave your company vulnerable to cyber threats. Contact IntelliSoft today to learn how our services can help protect your business and achieve peace of mind in the digital era.
AboutKosta Mitrofanskiy
I have 25 years of hands-on experience in the IT and software development industry. During this period, I helped 50+ companies to gain a technological edge across different industries. I can help you with dedicated teams, hiring stand-alone developers, developing a product design and MVP for your healthcare, logistics, or IoT projects. If you have questions concerning our cooperation or need an NDA to sign, contact info@intellisoftware.net.