The Internet of Things (IoT) is steadily reshaping how we engage with everyday objects, transforming them into smart, connected devices that seamlessly gather and share data. This shift isn’t driven by one breakthrough but rather a combination of advancements in sensor technology, communication networks, and small-scale embedded systems. In fact, by 2027, IoT Analytics projects will have over 29 billion IoT connections, enhancing how our surroundings respond and adapt to our needs.
At the core of this evolution is IoT architecture—a sophisticated, often hidden framework that makes these interactions possible. But how exactly does it all come together? Drawing on years of experience in IoT development, we’re here to unpack the key components and explain how this remarkable technology operates.
Table of Contents
Understanding IoT Basics
Before we discuss the nitty-gritty of IoT cloud architecture, let’s simplify it. The Internet of Things (IoT) involves linking everyday objects—like sensors, smart gadgets, and software—to communicate and share data. Imagine your city; traffic lights, cars, and buildings all connected, working together to gather information and make things run smoother. That’s essentially what IoT is on a larger, global scale.
Now, let’s zoom in on the essential components that make an IoT system tick:
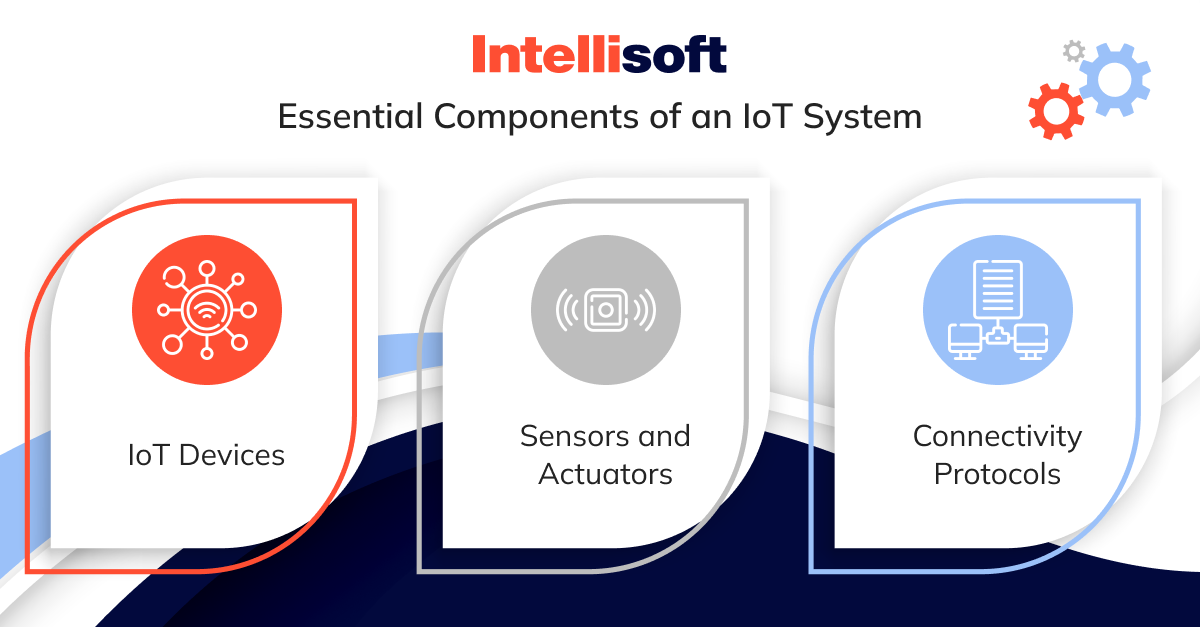
IoT Devices
Physical objects are the backbone of any network, spanning from small devices such as fitness trackers to more sophisticated industrial machinery. These devices come with sensors that monitor various environmental factors such as temperature, pressure, or motion. In some cases (for example, with smart thermostats), they also include actuators that enable the device to interact with its surroundings based on the information they collect.
Sensors and Actuators
Sensors are like the senses of an IoT device—constantly on alert, picking up all sorts of information, whether it’s temperature, light, or motion in the surrounding environment. They gather this data in real-time, whether it’s the warmth in a room or the vibrations of machinery. Then, you’ve got the actuators—think of them as the device’s limbs. They take the cues from the sensors and do something about it. Picture a smart thermostat; with a temperature sensor and an actuator, it can automatically adjust the room’s climate to keep you comfortable without needing to do anything.
Connectivity Protocols
Think of IoT devices like people trying to converse—they need a common “language” to communicate correctly. That’s where protocols come into play. These protocols set the guidelines for sharing information between devices and systems. You’ve probably heard of some, like Wi-Fi, Bluetooth, or cellular networks, which handle shorter-range exchanges. LPWAN (Low-Power Wide-Area Network) technologies such as Sigfox and LoRaWAN are used for longer distances, especially when conserving power is critical. Choosing the right protocol for the IoT network architecture comes down to a few essentials; what kind of data is being sent, how far it needs to travel, and how much energy the devices can afford.
Architecture of IoT
There’s no blueprint for IoT architecture, as designs often shift based on specific business objectives. Some setups are straightforward, while others require more layers and complexity.
A notable example is the Reference Model, introduced at the 2014 IoT World Forum by Cisco, IBM, and Intel. This model presents a seven-layer framework developed to aid IT departments, developers, and CIOs fast-track IoT implementation. However, regardless of how many IoT architecture layers are incorporated, the essential components remain the same:
- Smart devices that collect data.
- Networks and gateways that link these devices to the internet, typically using low-power technology.
- Middleware or IoT platforms that offer data storage, computing power, and analytics.
- Applications that enable user interaction with the system and allow control over the physical environment.
These elements form the backbone of any IoT system, which can then be expanded into a multi-tiered architecture. Commonly, the IoT platform architecture consists of four primary layers:
- Perception layer where smart devices operate.
- Connectivity layer transmits data from devices to the cloud through networks and gateways.
- Processing layer handles and processes data streams via IoT platforms.
- Application layer provides analytics, reporting, and control tools for users.
In some cases, three additional layers come into play:
- Edge (or fog) computing layer processes data closer to the devices, often using gateways.
- Business layer utilizes data insights to guide decision-making within companies.
- Security layer encompasses all other layers, ensuring robust data protection.
While these extra layers might seem optional, they enhance the system’s adaptability to meet contemporary business demands, making it a more resilient and flexible IoT architecture.
Perception Layer
The first step of any IoT system begins with a diverse range of “things” or endpoint devices that connect the physical and digital worlds. These devices come in all shapes and sizes, from tiny chips to massive vehicles. Depending on their roles, IoT devices generally fall into three main categories:
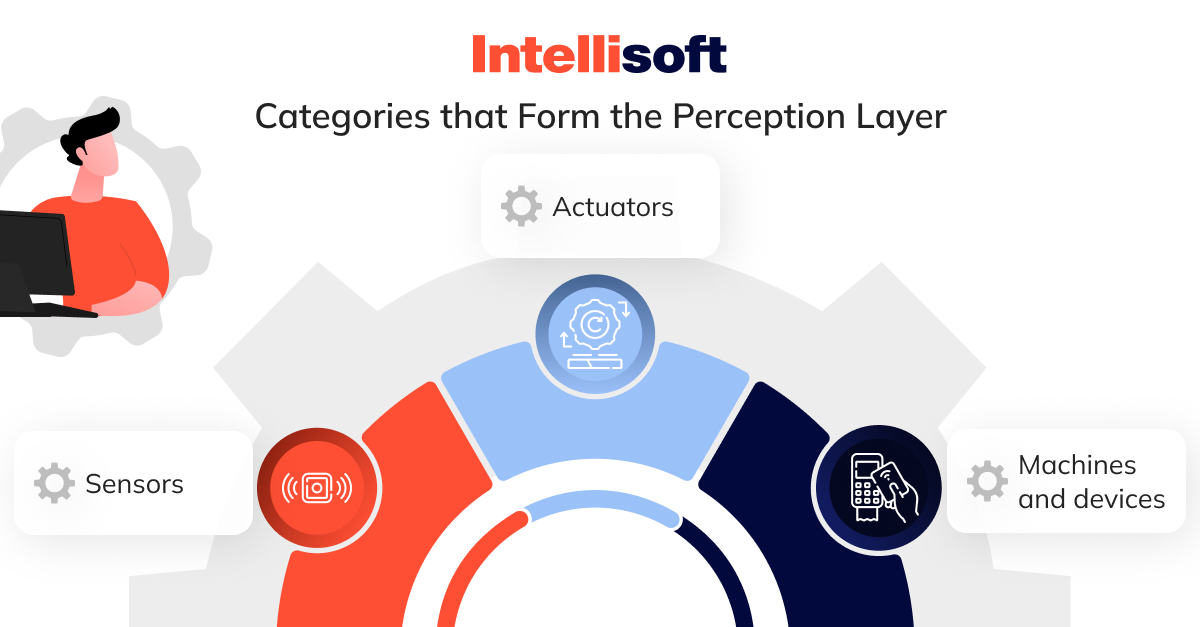
- Sensors. These include probes, meters, and gauges that gather real-world data like temperature or humidity. They convert this information into electrical signals, which are then sent to the IoT system. Sensors are usually small and energy-efficient.
- Actuators. These devices take electrical signals from the IoT system and turn them into physical actions, powering components like motor controllers, lasers, and robotic arms.
- Machines and devices. These often incorporate sensors and actuators as connected components or built-in parts.
One key point to remember: IoT systems don’t limit the number or location of these devices. An IoT network could be as small as a few devices in one room or as large as thousands of sensors spread across the globe.
Connectivity Layer
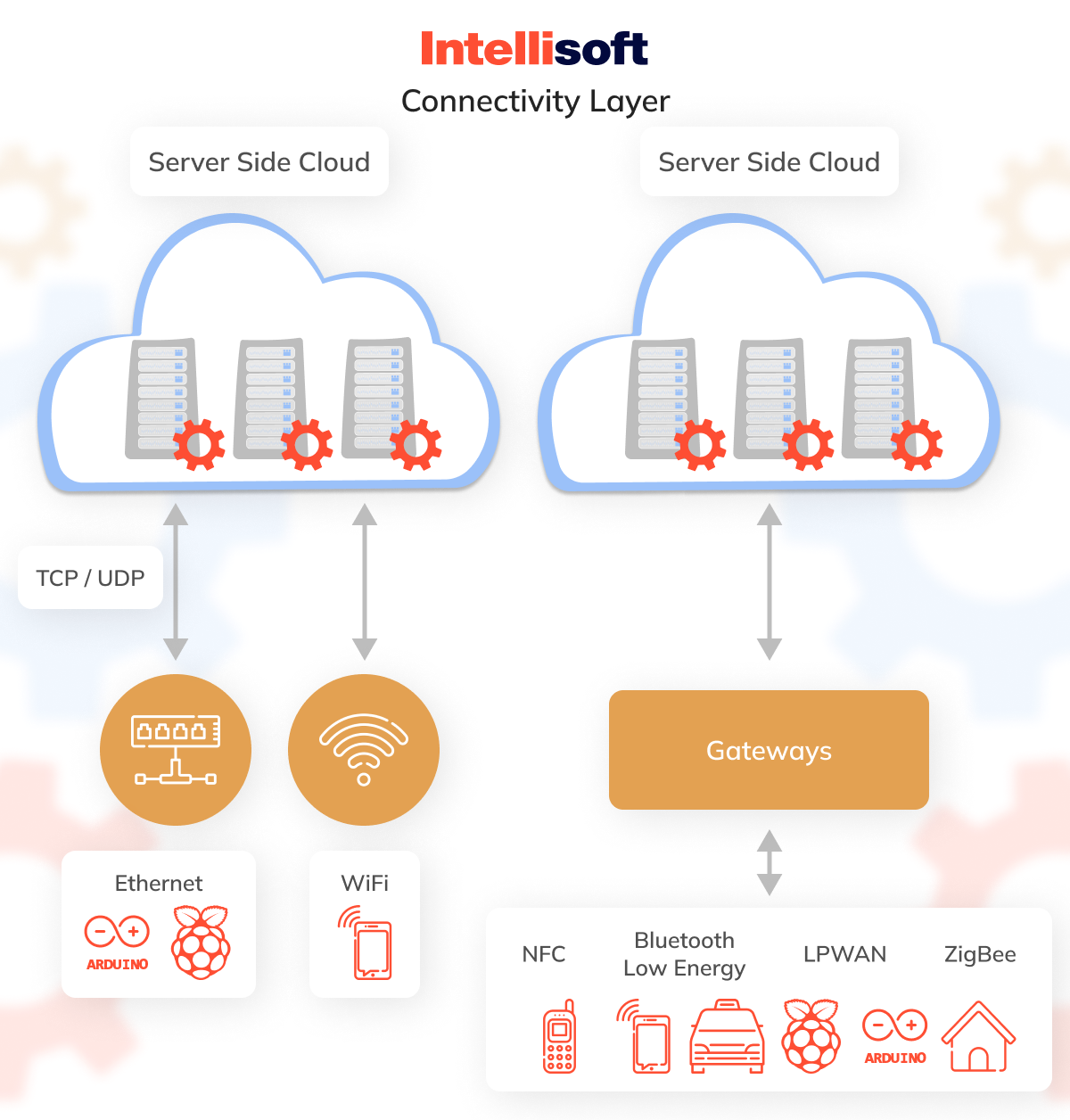
The second layer of IoT infrastructure manages communications between devices, networks, and cloud services. This exchange typically occurs in two ways:
Directly through the TCP or UDP/IP stack.
Indirectly via gateways—these are either hardware or software components that translate between various protocols and handle the encryption and decryption of IoT data.
There are multiple networking technologies used for these communications, each suited to different applications:
- Ethernet. Most effective for stationary devices such as security cameras, industrial machines, or gaming consoles.
- WiFi. Ideal for IoT setups that require transferring large amounts of data, such as smart home devices that are easy to recharge and usually confined to small spaces.
- NFC (Near Field Communication). Suitable for fast and secure data exchanges between devices within a very short range, usually no more than 10 cm.
- Bluetooth. It is a common short-range communication technology in wearable technology. The Bluetooth Low-Energy (BLE) standard is specifically designed for devices that need to conserve power while efficiently transferring small amounts of data.
- LPWAN (Low-power Wide-area Network). Best for applications that require long-range connections but use minimal power. Devices on these networks can often operate for over a decade, making them perfect for use in smart cities, agriculture, and building management systems that transmit small data packets at extended intervals.
- ZigBee. A low-power option for shorter distances. Its support of numerous nodes—up to 65,000—makes it a great choice for home automation and industrial IoT architecture or medical devices.
- Cellular networks. Offering dependable data transfer over a wide area, with IoT-specific standards like LTE-M, designed for handling larger data volumes, and NB IoT architecture, more suited to transmitting smaller data packets over low-frequency channels.
Once everything is connected, devices still need messaging protocols and the cloud IoT architecture to communicate with each other. Some common protocols include:
- DDS (Data Distribution Service). DDS is often used in real-time systems and enables direct communication between IoT devices and applications.
- AMQP (Advanced Message Queuing Protocol). A protocol designed for exchanging data between servers in a peer-to-peer fashion.
- CoAP (Constrained Application Protocol). This lightweight protocol mirrors the functionality of HTTP but requires far fewer resources, making it suitable for devices like sensors with limited memory and power.
- MQTT (Message Queue Telemetry Transport). A streamlined messaging protocol based on TCP/IP, specifically created to collect data from low-power devices efficiently.
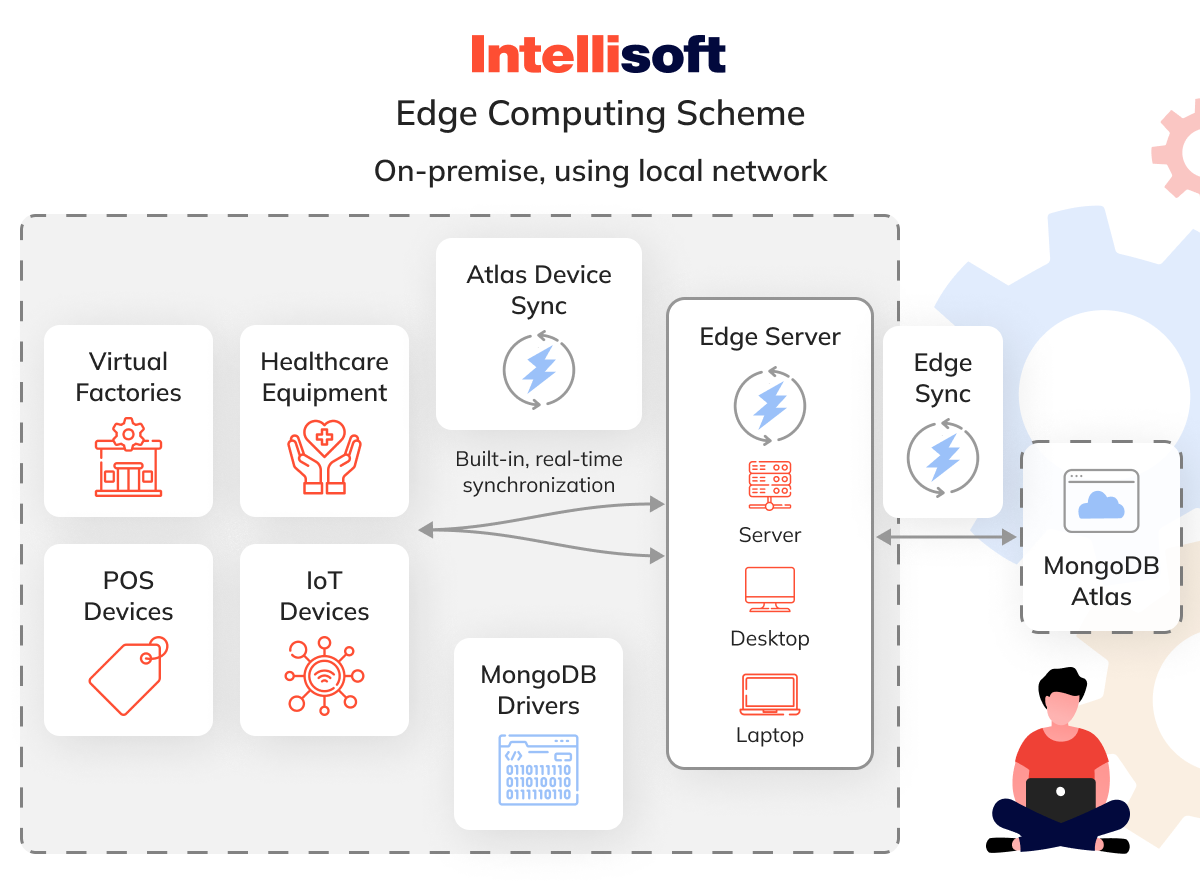
Edge or Fog Computing Layer
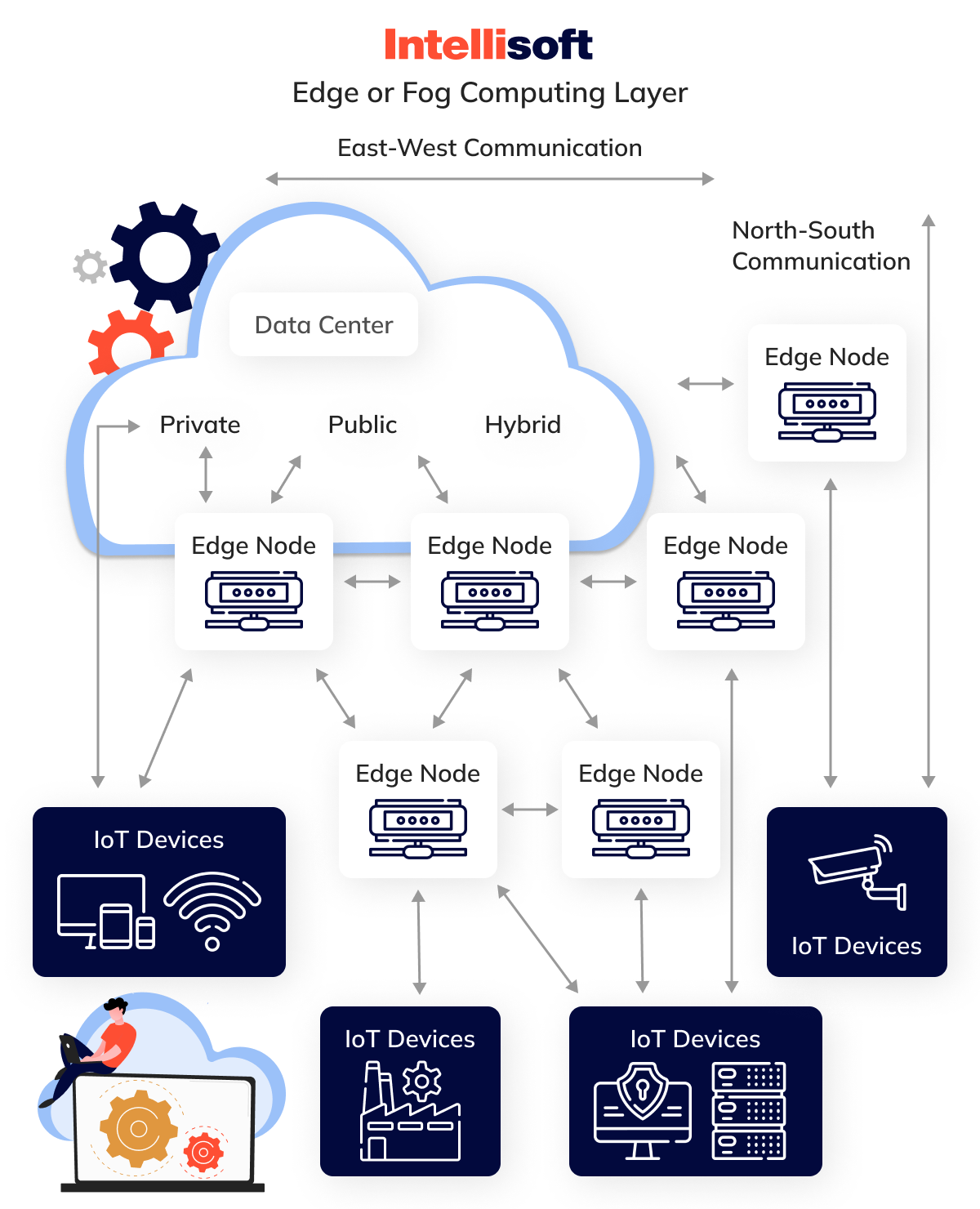
Which of the following best describes the edge technology layer of the IoT architecture? Edge computing is essential in enabling IoT systems to meet the high expectations of 5G networks, which offer quicker speeds, enhanced security, and the capacity to support far more connected devices than 4G could ever handle. With 5G delivering ultra-low latency and lightning-fast connectivity, Azure IoT edge architecture becomes critical in ensuring data processing can keep up with these advancements.
At its core, the idea behind the edge (or fog) computing layer of AWS IoT reference architecture is straightforward; handle and store data as close to its source as possible. Instead of offloading everything to the cloud, this method processes vast amounts of real-time data locally, reducing time and resource consumption. The result? Lower latency, faster system responses, and an overall boost in performance.
IoT edge architecture operates across gateways, local servers, and various nodes throughout the network. At this local level, data can be:
- Analyzed for further processing
- Formatted for easier management
- Decoded or filtered
- And then routed to its next destination
The initial layers of Azure IoT edge architecture keep the data flowing, constantly refining and transforming it. Once the data moves to the next stage, it’s ready for use in consumer applications. This approach is fundamental to unlocking 5G’s true potential, ensuring it can deliver on its promises and more.
Processing Layer
The processing layer is the central hub where data from earlier stages is gathered, stored, and processed. This layer of Azure IoT architecture operates through IoT platforms and is divided into two main stages: data accumulation and data abstraction.
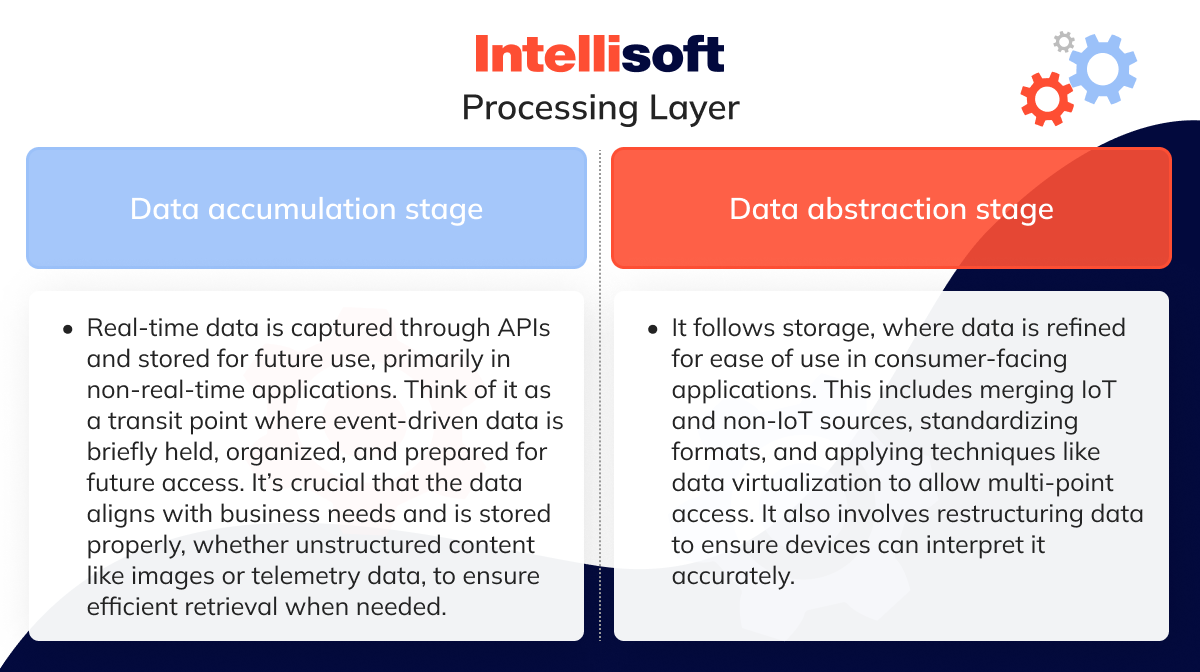
Data accumulation stage
Real-time data is captured via APIs and stored at this point, making it available for future use, especially for non-real-time applications. Picture this as a transit station where event-driven data is temporarily held, prepared, and organized for future access.
During this stage, it’s essential to ensure that the collected data aligns with business needs and is properly stored. Whether it’s unstructured content like images or videos that find a home in an IoT data lake architecture or telemetry data directed to specialized databases, the key objective is to ensure everything is stored efficiently for quick retrieval when necessary.
Data abstraction stage
Once data is stored, it enters the abstraction phase. Here, the focus shifts to refining it, ensuring it’s easy to work with for consumer-facing applications. This process includes:
- Merging data from IoT and non-IoT sources, such as ERM, ERP, and CRM systems
- Standardizing diverse formats
- Aggregating data or applying data virtualization techniques to ensure access from multiple points
- Data restructuring, so it will be sent back to devices, ensuring the systems can interpret it correctly.
Together, these two stages of simple IoT architecture streamline the interaction between smart devices and software. By masking the underlying hardware complexities, developers can focus on addressing business challenges without worrying about compatibility across different devices.
Application Layer
At this point, IoT software architecture can increasingly analyze data to address critical business needs. The scope of IoT applications is vast, ranging from simple systems to highly sophisticated ones, and these solutions operate across different technologies and platforms. Some common examples include:
- Software for monitoring and controlling various devices
- Mobile apps that facilitate user interaction with ease
- Business intelligence tools to enhance decision-making
- Machine learning-driven analytics tools
Nowadays, developers can create IoT applications directly on platforms that provide a comprehensive suite of tools for data mining, advanced analytics, and data visualization. Alternatively, many applications utilize APIs to integrate seamlessly with middleware, simplifying functionality and boosting efficiency.
Business Layer
For data to truly impact business, it can’t just sit there; it needs to actively drive real-world solutions and help fulfill business goals. Insights should inspire collaboration among key players, leading to new processes that enhance productivity.
Decision-making is rarely a one-person job. Typically, it involves multiple tools or platforms working in sync. That’s why the business layer operates at a higher level, coordinating various applications to ensure everything functions smoothly.
Security Layer
A robust security layer must cover all infrastructure levels to truly secure your IoT ecosystem. While IoT security architecture is a huge topic deserving a deep dive, let’s focus on the key safety measures at each level to ensure a solid foundation.
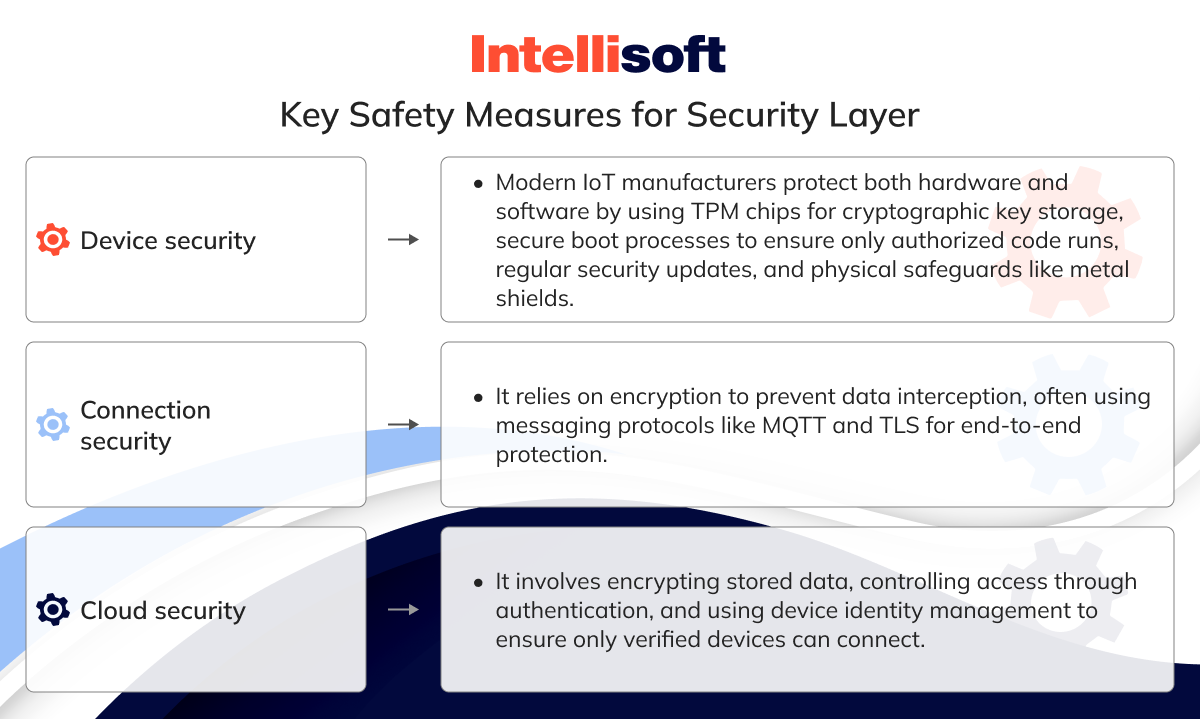
Device security
Modern IoT manufacturers are already taking steps to protect both hardware and software. Key features include:
- Embedded TPM (Trusted Platform Module) chips store cryptographic keys to authenticate and protect endpoint devices.
- Secure boot processes, ensuring that only authorized code runs when a device powers up
- Regular security patch updates to stay ahead of potential threats
- Physical protection, such as metal shields, to block unauthorized access to the device
Connection security
Encryption is crucial whether data is flowing through devices, networks, or apps. Without it, sensitive data could be easily intercepted. Messaging protocols like MQTT, AMQP, and DDS typically leverage Transport Layer Security (TLS) to provide end-to-end encryption, keeping your data secure in transit.
Cloud security
Data stored in the cloud also needs to be protected. Encrypting data at rest is essential to prevent unauthorized access. Cloud security incorporates authentication and authorization to control who can access IoT apps. Device identity management adds an extra layer of protection, ensuring that only verified devices connect to the cloud.
The good news? Leading providers like Microsoft, AWS, and Cisco offer built-in security features like end-to-end encryption, device authentication, and access controls. Still, it’s wise to regularly check your system’s defenses—whether it’s a small IoT device or a large-scale analytical platform. Security is only as strong as its weakest link.
The Stages of IoT Architecture
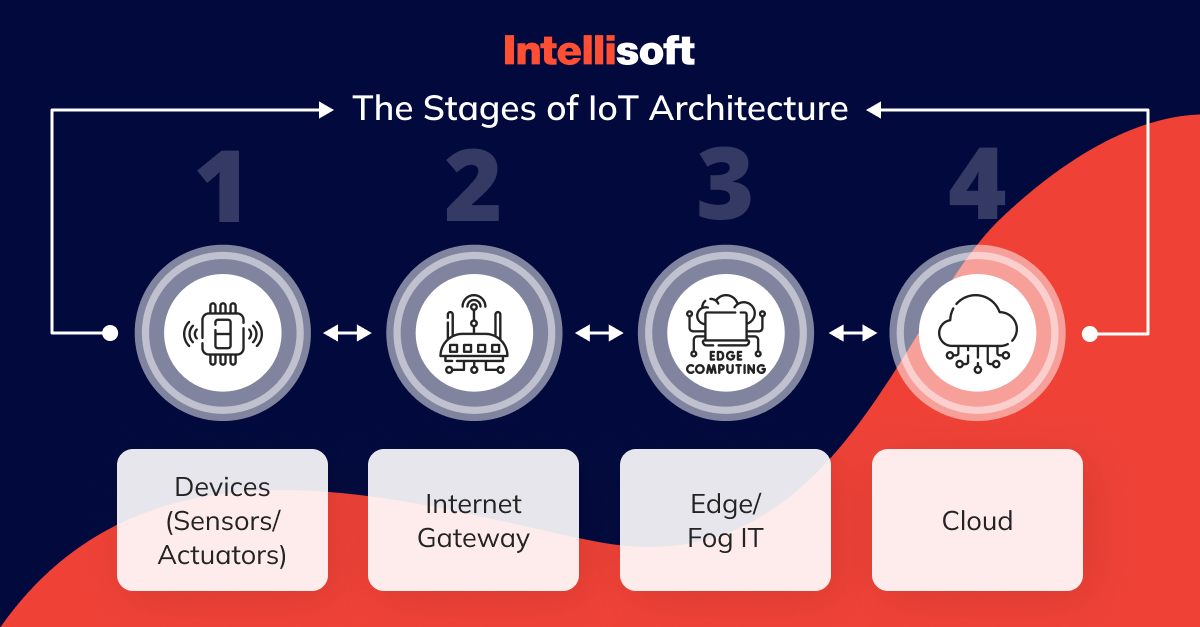
The Internet of Things (IoT) architecture for beginners can be broken down into four key stages, each representing a vital component of how these systems function. The IoT architecture diagram above emphasizes the role of edge computing, which takes on greater significance than in many traditional designs.
- Devices. Everything begins here, at the perception layer, where sensors and actuators gather environmental data. These IoT devices transmit the collected information to the next phase; the IoT gateway architecture.
- Internet gateways. In this stage, raw data from the IoT devices is received and undergoes some preliminary processing before being forwarded to the cloud. The gateway may either be directly connected to the device or act as an intermediary, communicating with sensors over low-power networks and channeling the data to the Internet. Essentially, this stage manages the transportation of data within the IoT framework.
- Edge computing. Once the pre-processed data reaches this point, it shifts to handling it as efficiently as possible. Edge computing plays a critical role here by processing the data near its source, which significantly reduces the need to send everything to centralized cloud servers. By keeping data processing local to the IoT devices and sensors, this method reduces latency, conserves bandwidth, and improves response times—crucial for real-time applications like smart city infrastructure or industrial automation.

- Cloud or data centers. Finally, the data is stored in the cloud or a data center for more comprehensive processing. This is where the application and business layers come into play, utilizing the data to fuel dashboards, management systems, or even develop machine learning models. This phase of AWS IoT architecture diagram handles the resource-heavy tasks, providing advanced insights and supporting long-term decision-making.
Related articles:
- IoT for Fleet Management in 2023: a Complete Guide
- IoT Data Integration with Existing Systems: Bridging the Gap to Legacy Infrastructure
- How To Control IoT Devices To Reach Your Business Goals
- IoT in Oil and Gas Industry: Future of Energy Technologies
- IoT Monitor Network Traffic: How To Optimize Traffic Easier
Common Design Patterns for IoT Architecture
Building scalable, efficient, and secure IoT systems relies heavily on employing the right design patterns. Below is an overview of some of the most widely used and effective design patterns in IoT cloud architecture.
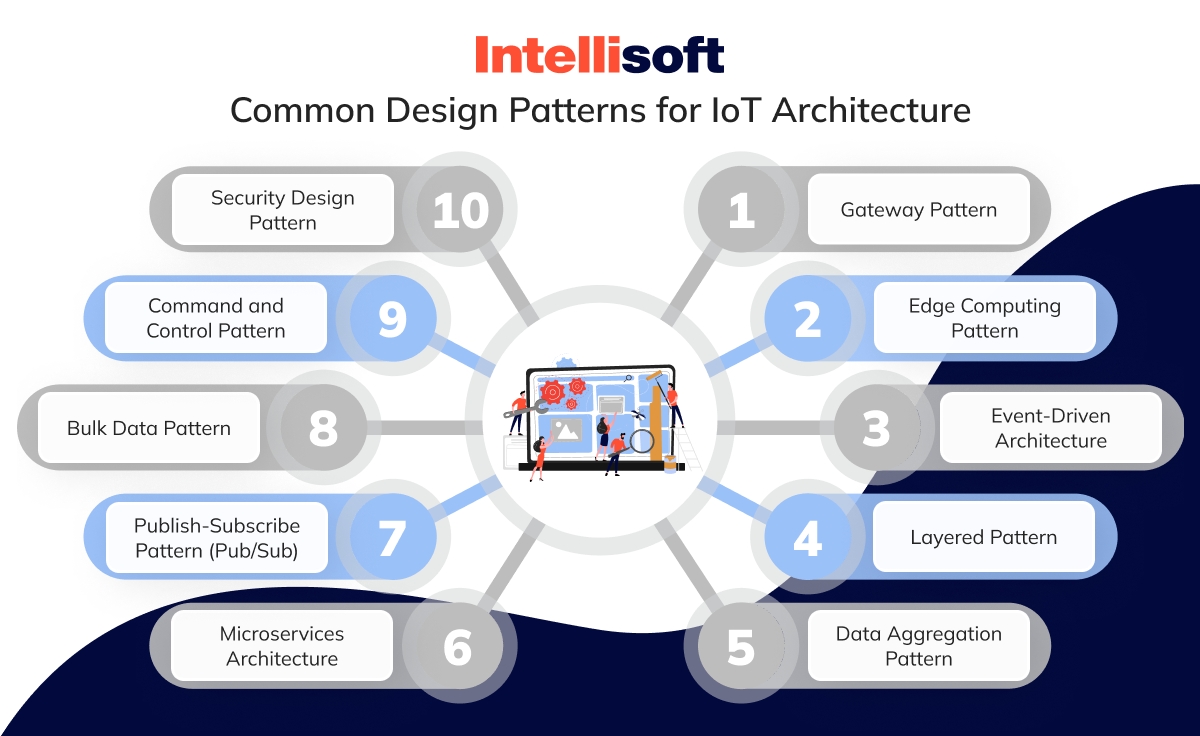
Gateway Pattern
IoT devices typically have restricted processing power and depend on gateways to connect with the cloud. These gateways gather data from edge devices, perform preprocessing, and send it to the cloud or a back-end system. This approach is particularly useful when IoT devices face limitations in connectivity or processing capabilities.
Edge Computing Pattern
Processing data closer to its source, directly on edge devices, minimizes latency and reduces the demand on cloud resources. This approach is crucial for real-time decision-making and helps lower data transmission costs. It benefits IoT systems that need low-latency responses, such as autonomous vehicles or industrial monitoring applications.
Event-Driven Architecture
This IoT in architecture pattern centers on triggering actions based on environmental changes. IoT devices publish events (data) to the system, which can then process or respond as required. It’s ideal for real-time applications, such as security systems, where devices activate alerts when specific thresholds are exceeded.
Layered Pattern
7 level architecture of IoT is structured into distinct layers—such as the device, network, and data processing layers—each responsible for specific tasks. This modular design enables better management and scalability. It’s particularly useful in large-scale IoT deployments where data flow and communication are complex.
Data Aggregation Pattern
IoT data architecture transmit data to an aggregator node or service, which processes and combines the data before sending it to the cloud or a data center. This approach reduces the amount of data transmitted, optimizing resource usage. It’s particularly effective in scenarios with numerous devices, like smart city projects, where large volumes of data are constantly generated.
Microservices Architecture
In IoT, microservices allow various system components, like data ingestion, analytics, and device management, to be managed and scaled independently. Each microservice handles a specific task and communicates with others via APIs. This approach is ideal for scalable IoT solutions with diverse functionality needs, such as connected healthcare systems.
Publish-Subscribe Pattern (Pub/Sub)
In this pattern, devices (publishers) send messages to a message broker, forwarding the data to subscribers, such as processing services. This setup decouples data generation from its consumption, allowing for more flexible communication. It’s particularly useful in IoT systems that require many devices to communicate asynchronously, such as environmental monitoring networks.
Bulk Data Pattern
This pattern is used when IoT devices produce large volumes of data that don’t require immediate processing. Instead, the data is collected and sent in bulk to the cloud or data center for batch processing. It’s ideal for applications like smart meters, where the data can be processed periodically rather than in real time.
Command and Control Pattern
This pattern enables centralized control of multiple devices. A control system sends commands to devices based on data analysis or user input, adjusting their behavior accordingly. It’s commonly used in home automation systems to control lighting, temperature, and security.
Security Design Pattern
This approach incorporates security protocols across every layer of the IoT framework, using encryption, authentication, and access controls to safeguard data and devices from unauthorized access. It’s particularly crucial for IoT applications that handle sensitive information, such as in healthcare or industrial IoT architecture.
Internet of Things (IoT) Architecture Use Cases
The architecture IoT has become instrumental across numerous sectors, showcasing its flexibility in addressing diverse practical challenges. Some prominent examples include:
Smart Cities
Use case: smart traffic management
With the help of a smart city IoT architecture diagram, cities can monitor traffic conditions in real time, allowing for dynamic adjustments to traffic lights and better control over congestion. This system also improves public transportation efficiency by providing data on traffic patterns, making it easier to adjust bus or tram schedules.
Example: In Barcelona, Spain, IoT technology plays a key role in traffic management, controlling street lighting, monitoring air quality, and improving waste collection. The city’s integrated approach boosts resource management and overall sustainability.
Use case: smart waste management
IoT sensors installed in waste bins detect when they are nearly full, sending real-time notifications to waste collection services. This data-driven approach enables optimized waste collection routes, reducing operational costs, fuel consumption, and environmental impact.
Industrial IoT (IIoT)
Use case: predictive maintenance
By embedding sensors into industrial machinery, companies can continuously monitor the health and performance of their equipment. The data is analyzed in real time to predict potential malfunctions or failures, allowing for proactive maintenance. This method prevents costly downtime and extends the life of machines.
Example: General Electric (GE) leverages IoT in its aviation and energy sectors for predictive maintenance, helping reduce unexpected equipment failures, cut downtime, and enhance operational efficiency.
Use case: factory automation
SDN architecture in IoT enables seamless connectivity between factory machines and robotic equipment, allowing for real-time remote monitoring and control. This results in more efficient production, fewer human errors, and improved resource management, such as energy and materials.
Example: Siemens implements IoT technology to automate production lines, monitor equipment status, and optimize energy consumption in smart factories, significantly improving productivity.
Healthcare and Wearables
Use case: remote patient monitoring
Wearable devices with IoT sensors collect vital signs such as heart rate, blood pressure, and glucose levels. This data is transmitted to healthcare providers in real time, enabling continuous patient monitoring, reducing the need for frequent in-person visits, and allowing for timely interventions in case of abnormalities.
Example: Philips Healthcare offers IoT-enabled solutions for remote patient monitoring. These solutions track vital signs and automatically alert healthcare professionals of critical health conditions, ensuring quicker response times and enhanced patient care.
Use case: smart hospital management
IoT systems streamline medical equipment management, patient data, and hospital facilities. Features like smart beds that monitor patient movements, real-time tracking of medical assets, and environmental monitoring (such as temperature or air quality) improve patient care and operational efficiency within the hospital.
Example: Many modern hospitals use GCP IoT architecture to track and manage medical equipment, optimize energy usage, and ensure a better overall patient experience through improved facility management.
Smart Homes
Use case: home automation
IoT devices such as smart thermostats, lighting systems, and security cameras enable users to remotely control and monitor their home environments through mobile apps or voice assistants. These systems enhance convenience, security, and energy efficiency by allowing for automation and remote access to various home functions.
Example: Google Nest offers a range of IoT-enabled solutions, such as smart thermostats, doorbell cameras, and security systems. These allow users to control their home environments and monitor activities remotely, ensuring comfort and safety from anywhere.
Use case: energy management
IoT sensors monitor real-time energy consumption, automatically adjusting heating, cooling, and lighting systems to optimize energy usage. This approach helps reduce waste and improve efficiency, leading to cost savings and a lower environmental impact.
Example: Ecobee and Honeywell provide smart thermostats that analyze real-time data on home occupancy and temperature, making automatic adjustments to minimize energy consumption and increase efficiency while maintaining a comfortable living environment.
Agriculture and Smart Farming
Use case: precision agriculture
IoT sensors monitor critical factors such as soil moisture, temperature, weather conditions, and crop health, providing farmers real-time data. This method allows them to optimize irrigation, pesticide application, and harvest timing, leading to higher crop yields, reduced resource consumption, and more sustainable farming practices.
Example: John Deere integrates IoT technology into its farming equipment to monitor crop health, soil conditions, and environmental factors. This enables precision planting, fertilization, and irrigation, which helps maximize agricultural output.
Use case: livestock monitoring
Kafka IoT architecture devices attached to livestock track their health, location, and behavior in real-time. This approach allows farmers to detect illnesses early, monitor feeding patterns, and ensure the safety of their herds. The data collected helps optimize farm operations and improve the overall well-being of the animals.
Example: Many farms use IoT-enabled collars and sensors to monitor the health and movement of livestock, providing insights that help manage herd health, ensure proper nutrition, and prevent the spread of disease.
Connected Vehicles and Transportation
Use case: fleet management
NB-IoT architecture enables real-time tracking of vehicle locations, fuel consumption, and driver behavior, helping businesses optimize routes, reduce fuel costs, and improve overall safety. These systems provide data insights for better fleet maintenance and more efficient logistics operations.
Example: UPS uses IoT sensors and GPS tracking across its delivery fleet to optimize routes, reduce fuel consumption, and enhance delivery efficiency, ultimately lowering operational costs and improving environmental sustainability.
Use case: autonomous vehicles
Autonomous vehicles rely on IoT sensors to communicate with traffic infrastructure, other vehicles, and real-time traffic data to ensure safe, efficient travel. These sensors monitor surroundings, adjust speeds, and navigate complex driving conditions without human intervention.
Example: Tesla’s autonomous cars use a network of IoT sensors and advanced software to enable self-driving capabilities. They process real-time data to make decisions on speed, route adjustments, and obstacle detection for safer driving.
Retail and Supply Chain Management
Use case: inventory management
IoT sensors and RFID tags enable real-time tracking of inventory levels, automatically triggering reorder processes when stock runs low. This method reduces the risk of stockouts, minimizes human error, and optimizes inventory management by ensuring timely restocking.
Example: Amazon employs IoT-enabled robots and sensors throughout its warehouses to manage inventory, track products in real-time, and optimize the entire fulfillment process, increasing efficiency and reducing operational costs.
Use case: cold chain monitoring
IoT sensors monitor critical environmental conditions such as temperature, humidity, and pressure while transporting perishable goods. This approach ensures the safe handling and storage of food, pharmaceuticals, and vaccines, reducing spoilage and ensuring compliance with safety standards.
Example: Pharmaceutical companies use IoT sensors to monitor the cold chain while transporting drugs and vaccines, ensuring that they are stored and delivered at the correct temperatures, preventing spoilage, and maintaining product efficacy.
IntelliSoft Experience with IoT Architecture Development
An industrial equipment manufacturer set out to transform how customers manage and monitor heating systems. Their goal? To offer a smart, remote control solution that would make system oversight easier and more efficient. However, their current setup couldn’t support the advanced security, real-time data processing, or seamless device connectivity needed for such a system. They needed a reliable partner to help them design a secure, scalable IoT platform that could handle the complexities of remote device control and ensure safe data transmission.
The manufacturer sought IntelliSoft’s help with a tailored IoT solution for remote heating system management. IntelliSoft designed a secure, scalable IoT system architecture focused on performance and real-time monitoring.
Here are the critical components of this solution:
- Gateway and edge computing. Local gateways collected, processed, and transmitted data to cloud servers, reducing latency and enabling real-time decisions.
- Data aggregation. The system aggregated real-time data from thousands of devices, offering centralized insights and continuous monitoring through a dashboard.
- Security. Encryption and multi-factor authentication protected data and access at every level.
- Scalable microservices. The microservices architecture allowed independent scaling of system components, supporting the client’s growth.
- Command and control. A mobile app could allow users to remotely manage heating settings, receive alerts, and schedule maintenance, improving efficiency.
As a result, the IoT system enabled remote control, reduced maintenance costs, and optimized energy consumption, leading to a 30% increase in product adoption in six months while ensuring security and scalability.
Considerations When Choosing an IoT Solution
When selecting the right IoT solution, it’s vital to consider it from multiple perspectives—strategic, operational, and technical. To make the most informed decision, here are a few key questions you should ask as you weigh your options.
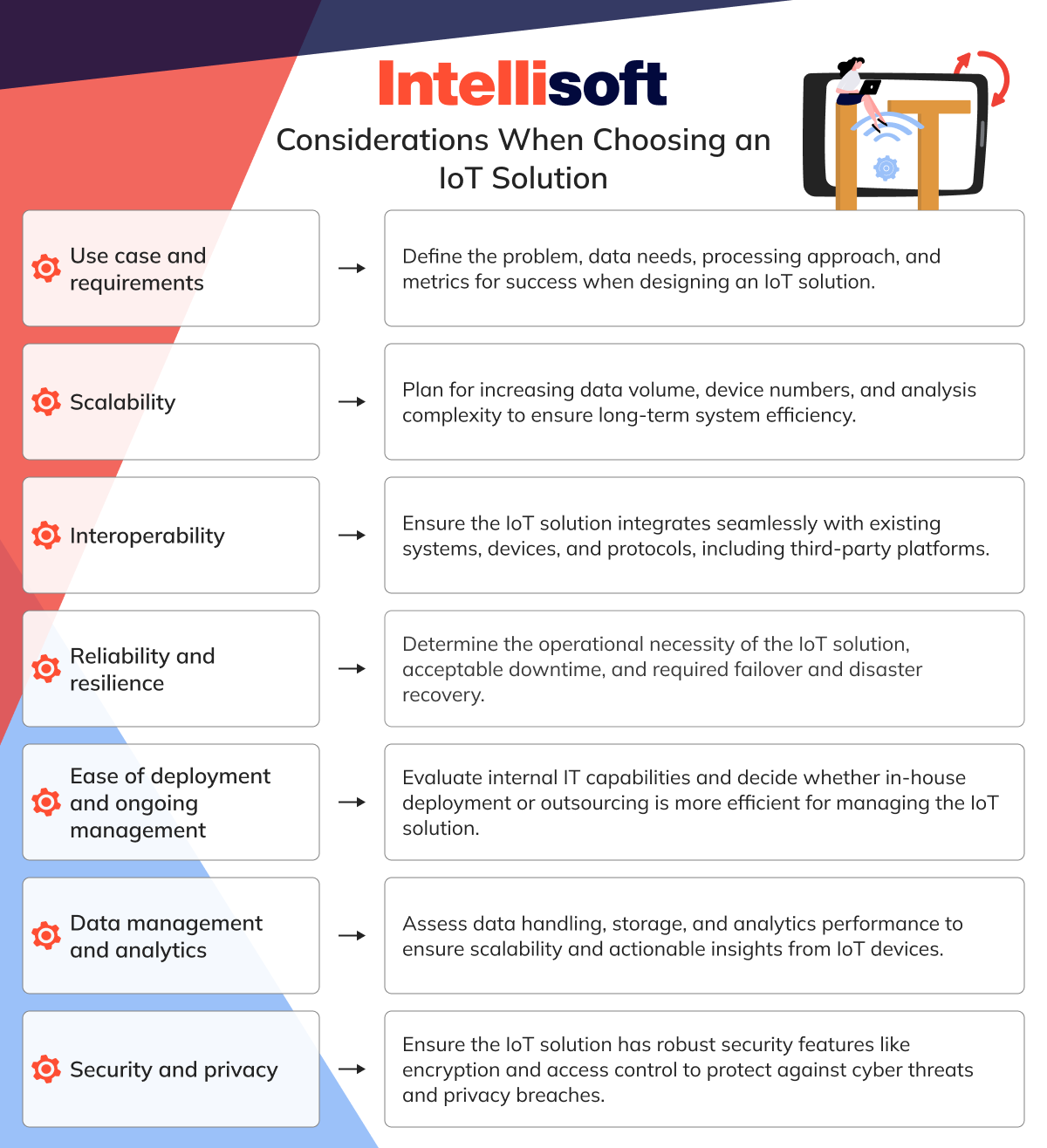
Use Case and Requirements
Clearly defining the use case and requirements for the Azure IoT reference architecture is essential when designing any technical solution. You’ll want to ask yourself key questions such as:
- What specific problem is being addressed?
- What data will be gathered (for example, types and volume)?
- How will this data be processed—will it need to be analyzed in real time, or can it be done after the fact?
- How will you measure success—what metrics will you use to determine if the solution is working as intended?
Scalability
When designing an IoT solution, it’s crucial to consider how it will scale over time. This approach means planning to increase data volume and usage and accommodate a growing number of IoT devices and different types of devices. Additionally, you must consider the complexity of applications and the depth of analysis being performed to ensure the system remains efficient as demands increase.
Interoperability
It’s important to assess how the new IoT solution will integrate with your current systems, devices, and protocols. Compatibility is key to ensuring smooth operations. Additionally, consider how the solution will manage data exchanges with third-party systems, ensuring security and seamless communication between platforms.
Reliability and Resilience
When evaluating the criticality of an IoT solution, it’s essential to determine whether its functionality is operationally necessary.
- Is the functionality of the IoT solution operationally necessary?
- What are the income, customer, and brand impacts if the solution is unavailable?
- What level of downtime, if any, is an acceptable risk?
- What level of redundancy, failover, and disaster recovery capabilities are required?
Ease of Deployment and Ongoing Management
Assessing your organization’s internal IT capabilities is essential to determining what’s needed for the deployment and ongoing management of each potential IoT solution. One key consideration is the opportunity cost: How much would it take to recruit and develop the necessary talent in-house versus outsourcing to an established leader, followed by transitioning to internal management? A SaaS or ready-made platform subscription might be better if internal expertise is limited and hard to acquire. It reduces payroll costs and addresses the scarcity of in-demand skill sets.
Additionally, consider how technically advanced your user base is. A simple, intuitive user interface with dashboarding and visualization tools could be crucial if users are less familiar with programming languages. On the other hand, if your team is already proficient in languages like Python, a more advanced solution might be appropriate.
Data Management and Analytics
When evaluating an IoT solution, it’s crucial to assess how it handles data management, storage, processing, and analytics. These components’ scalability, performance, and flexibility are key to ensuring that the system can handle growing data volumes efficiently. Strong data storage and analytics capabilities are essential for deriving actionable insights, making informed decisions, and optimizing processes based on the data collected from IoT devices.
Security and Privacy
Security is crucial in IoT solutions to safeguard data, devices, and networks from potential cyber threats and privacy breaches. It’s important to evaluate the solution’s security features, including encryption, authentication, access control, and secure bootstrapping. Additionally, consider how firmware updates are handled to ensure that devices remain secure and protected against vulnerabilities.
Conclusion
The backbone of today’s smart solutions lies in IoT solution architecture, which is revolutionizing industries such as healthcare, agriculture, smart cities, and industrial automation. A robust seven-layer IoT architecture allows businesses to tap into real-time data, optimize operations, and strengthen security, creating more efficient workflows.
If you’re entering the world of IoT, choosing the right partner is crucial. That’s where IntelliSoft comes in. With years of experience crafting secure, scalable, and efficient IoT systems, IntelliSoft helps businesses design custom solutions tailored to their specific needs. Whether you’re building a smart home system or developing an advanced industrial platform, IntelliSoft’s expert team will guide you through every step, ensuring your project runs smoothly and delivers results.
Contact us today to get a consultation!