Most tech companies have established an online presence through various digital platforms, making it easier for them to connect with their customers and offer seamless transactions. However, businesses should ensure the security and quality of these web apps to maintain customer satisfaction and trust in the brand.
To tackle these issues, development teams must perform web application penetration testing to identify any potential vulnerabilities in their system. This process involves techniques, methods, and tools to thoroughly check the web application for software issues, bugs, faults, and other user experience inconveniences.
We will walk you through the web application pen testing process and provide the tools and methods to ensure your platform is optimized, secure, and bug-free, ultimately providing a seamless experience to your customers.
Table of Contents
What Is Pen Testing?
A pen test is a cyber security assessment conducted to identify, investigate, and remediate vulnerabilities in an organization’s network or applications. Penetration testing involves using the same tactics, techniques, and procedures (TTPs) that a cybercriminal might use to launch an attack against the organization. The purpose of the test is to determine whether the organization’s security controls are strong enough to withstand different types of threats.
The methods used in a pen test can vary depending on whether the test is being conducted externally or internally. The objectives and outcomes of each penetration test are customized to meet the organization’s unique requirements under assessment. The level of information shared with the penetration tester varies based on the type of assessment being performed. Ultimately, the goal of penetration testing is to ensure that an organization’s security measures are effective in preventing real-life cyber attacks.
Why Is Penetration Testing Essential?
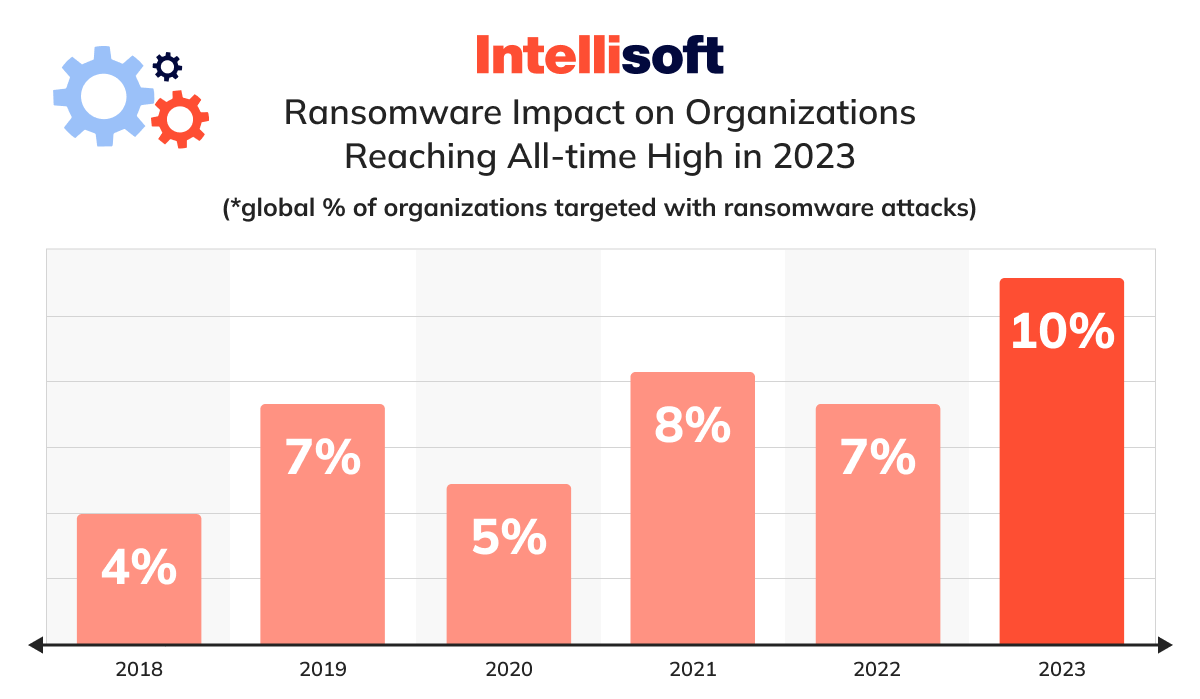
According to Checkpoint’s research, attempts of ransomware attacks on organizations worldwide increased to 10% in 2023, which is a significant rise from the previous year’s 7%. This percentage is the highest in the past years and indicates a growing threat of cyber attacks.
Here are some other notable statistics related to cyberattacks:
- The average cost of a data breach was recorded at $4.45 million in 2023, which is the highest on record. (IBM)
- Human error caused 74% of cybersecurity breaches. (Verizon)
- It takes an organization an average of 207 days to identify a breach. (IBM)
- The average lifecycle of a breach from identification to containment is 277 days. (IBM)
- The likelihood of a cybercrime entity being caught and prosecuted in the U.S. is estimated to be around 0.05 percent. (World Economic Forum)
- In 2023, 74% of breaches had a human element involved. (Verizon)
- In 2022, the US Federal Trade Commission received more than 1.1 million reports of identity theft. (US News)
- Security breaches increased by 68% in 2021. (CNET)
- Cyber fatigue, which is the apathy toward proactively defending against cyberattacks, affects up to 42% of companies. (Cisco)
- 64% of American people have never checked if their data was breached. (Varonis)
- The United States was the victim of 46% of all cyberattacks in 2020, which is more than twice the number of attacks on any other country. (Microsoft)
- 56% of Americans are not aware of how to respond in case of a data breach. (Varonis)
- Since the start of the Russia-Ukraine war in 2022, 97% of organizations have seen an increase in cyber threats. (Accenture)
How Does Penetration Testing Help with Data Breaches?
Web application security penetration testing is a critical process that helps prevent data breaches by identifying and mitigating vulnerabilities in an organization’s systems, applications, and networks. Here’s how it works:
Identifying Vulnerabilities
Penetration testing exposes weaknesses in an organization’s security infrastructure that malicious actors could exploit to launch a data breach.
Enhancing Security Posture
By conducting simulated attacks, penetration testing helps organizations improve their overall security posture, making it more challenging for attackers to infiltrate their systems and access sensitive data.
Risk Reduction
Penetration testing is a proactive approach to identifying and addressing vulnerabilities in a software system. It involves simulating a real-world attack on the system to detect potential weaknesses in technical controls or software security.
Automated Testing
Automated penetration testing tools enable organizations to continuously monitor their systems for vulnerabilities and detect and fix potential security issues before they can be exploited.
Business Continuity
Penetration testing is a crucial practice that assists businesses in maintaining optimal performance by identifying and mitigating potential security risks that could cause disruptions in operations. It is a proactive approach that helps prevent financial losses that could arise from data breaches and other security vulnerabilities.
How Is Web Application Penetration Testing Done?
Conducting penetration testing for web application involves steps and methodologies that aim to identify potential vulnerabilities within the system.
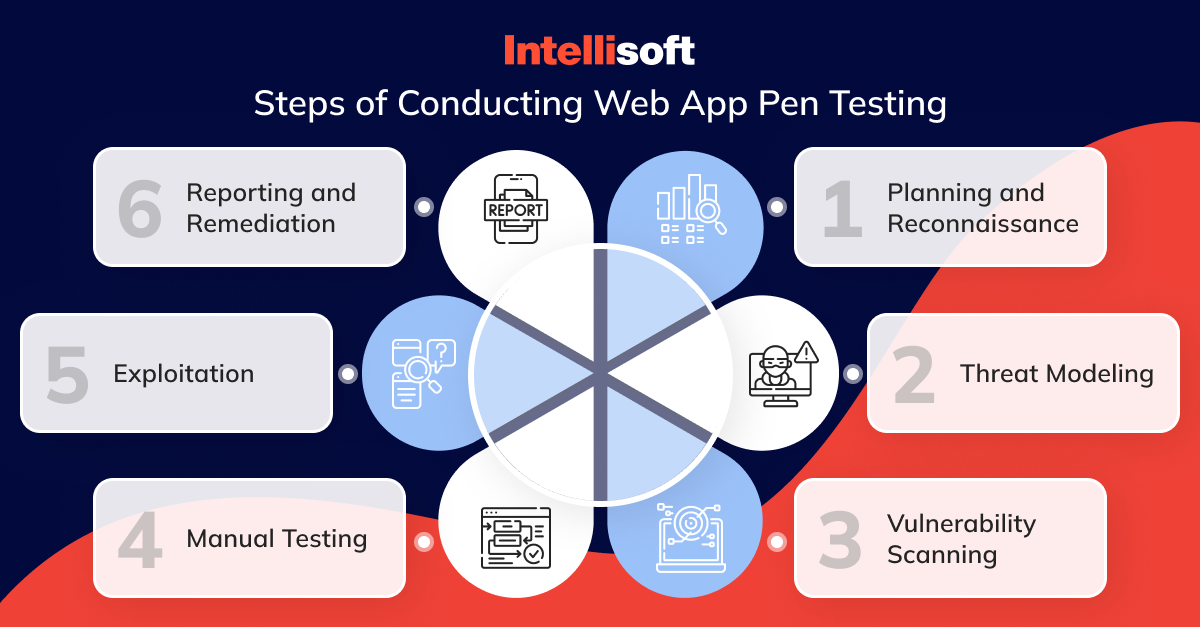
- Planning and Reconnaissance. During the initial phase of assessing a web application, it is crucial to gather as much information as possible regarding its architecture, the technologies employed, and any potential vulnerabilities that may exist. This step involves a comprehensive analysis of the target application to understand its underlying structure and any possible weak points that malicious actors could exploit.
- Threat Modeling. Analyzing and detecting any possible security risks that may harm the application is vital. Once potential threats are identified, evaluate them based on their severity and how much they can impact the application’s security. In this way, the most critical threats can be prioritized and addressed first to ensure the application remains secure and protected from potential attacks.
- Vulnerability Scanning. It’s essential to prioritize the security of your web application, and one way to do so is by taking advantage of automated tools for web application vulnerability assessment and penetration testing. These tools help you detect and address common security issues that can expose your application to threats, such as SQL injection, cross-site scripting (XSS), and insecure configurations. By utilizing these tools, you can proactively safeguard your web application and protect it against potential attacks.
- Manual Testing. Manual testing is important to assess a system’s security thoroughly. This method can reveal intricate weaknesses that automated tools might overlook. During manual testing, careful attention is essential to authentication mechanisms, session management, and business logic flaws.
- Exploitation. Identifying and assessing vulnerabilities’ impact is crucial in evaluating an application’s security. This approach involves exploiting the vulnerabilities to gain unauthorized access to sensitive data or execute arbitrary code.
- Reporting and Remediation. It is recommended that all findings related to the security of an application be thoroughly documented. This method includes identifying any vulnerabilities that were discovered, along with an evaluation of their potential impact on the system. Moreover, providing actionable recommendations for mitigating the identified vulnerabilities is important to enhance the application’s overall security posture.
What Are Types of Pen Testing?
There are ten different types of penetration testing. Let’s take a closer look at each one.
Network Services
Network services testing is a crucial process that assesses a network’s performance and functionality. It helps identify potential issues, make informed adjustments, and measure network performance to ensure that it meets necessary standards. Moreover, it plays a significant role in network security by providing insights and analysis to help businesses protect their networks from malicious attacks and vulnerabilities.
Client-Side
Client-side penetration testing is a method that focuses on identifying and exploiting vulnerabilities in client-side applications. This type of testing involves simulating attacks on software vulnerabilities present on client devices, such as workstations and mobile devices, to detect issues that could compromise the system’s overall security. Protecting the user side of applications and systems from potential threats is a crucial element of a comprehensive cybersecurity strategy.
Wireless
Wireless penetration testing is a process that assesses the security of wireless networks by simulating attacks. It targets Wi-Fi networks and devices that connect via wireless protocols and identifies vulnerabilities such as weak encryption, insecure network services, and device vulnerabilities. It reveals potential entry points for attackers and guides efforts to fortify the wireless infrastructure against real-world attacks.
Internal Network
Internal network penetration testing simulates an insider’s attack to assess the security of an organization’s internal network. It discovers weaknesses in components used within the organization, such as servers, workstations, and network devices. By mimicking an attacker, organizations can understand their security posture, identify critical vulnerabilities, and implement measures to mitigate risks.
External Network
External network penetration testing is a comprehensive and systematic approach to assessing the security of computer systems, applications, and services accessible from the Internet. The goal is to evaluate the effectiveness of an organization’s external defenses and provide valuable insights into strengthening its security posture and protecting against external threats.
Web Application
Web application penetration testing is a security measure used to simulate cyberattacks against a web app with the aim of identifying and mitigating vulnerabilities. It covers the web application’s source code, database, and backend network connections. The goal is to present practical insights and suggestions to enhance the app’s security.
Mobile Application
Mobile application penetration testing evaluates mobile apps’ security features to identify vulnerabilities that attackers could exploit. It thoroughly examines the app’s code, data storage, authentication processes, and interaction with external systems. The goal is to detect and address security weaknesses before malicious parties exploit them.
APIs
API penetration testing, or API pen testing, is a comprehensive security assessment that aims to determine the security posture of application programming interfaces (APIs). This type of assessment involves conducting simulated real-world attacks on an API to identify potential vulnerabilities that malicious attackers could exploit to gain unauthorized access or cause harm to the system.
The process includes techniques such as manual testing, automated scans, code reviews, and sending specially crafted requests to the API. The primary objectives of API penetration testing are to:
- Validate the security of the APIs
- Identify vulnerabilities
- Simulate real-world attacks
- Recommend mitigations
API penetration testing is crucial for protecting customer data and maintaining an organization’s overall security. APIs facilitate communication between software systems in modern apps. Therefore, securing them is of the utmost importance. Conducting API penetration testing regularly, ideally every six months, is recommended to ensure continuous security as APIs evolve and new threats emerge.
Containers
Container penetration testing is a specialized security assessment that evaluates the security of containerized applications and environments that are deployed using Docker. Containers are becoming increasingly popular due to their efficiency and scalability in each software development phase. The primary objectives of container penetration testing are:
- Identifying vulnerabilities within the container and container orchestration tools
- Simulating real-world attacks to assess the container’s resilience against security breaches
- Providing actionable insights and recommendations to improve the security posture of the containerized environment
Testing techniques for Docker containers include manual testing, automated scans, and code reviews. Tools such as Docker Bench and CDK can be used to audit containers and ensure compliance with security benchmarks.
Cloud
Cloud penetration testing is a security assessment focusing specifically on cloud environments. This testing aims to identify and evaluate any security vulnerabilities within an organization’s cloud-based applications, infrastructure, and services. Cloud penetration testing can uncover potential security weaknesses that attackers could exploit by simulating real-world cyber attacks. The benefits of cloud penetration testing include:
- Strengthening the security of cloud environments to protect against possible breaches.
- Preventing security breaches that could have been avoided by identifying and addressing security loopholes.
- Maintaining compliance with security standards and regulations is crucial to protect sensitive data stored or processed in the cloud.
- Improving the overall company’s security posture by providing actionable insights and suggestions for making cloud security measures more stringent.
Performing cloud penetration testing is an essential component of a robust cloud security plan. It involves using open-source and commercial tools, such as Wireshark and Metasploit, to assess and mitigate risks associated with cloud computing.
What Are The Different Approaches To Penetration Testing?

Black Box Testing
Black Box penetration testing is an essential cybersecurity practice involving simulated real-world attacks on a system without prior knowledge or access. During this process, testers operate like external attackers and use various methods to identify and exploit vulnerabilities that may exist in the system. The primary objective of this technique is to determine the exploitable vulnerabilities outside the network perimeter and assess the overall security posture of the system from an outsider’s perspective.
White Box Testing
White Box Testing is a comprehensive software testing technique that involves in-depth analysis of an application’s internal workings, structures, logic, and code. This methodology requires testers to have a thorough understanding of the code and its functionalities, allowing them to scrutinize the software’s inputs and outputs and detect potential security vulnerabilities.
Grey Box Testing
Grey Box Testing is a popular software technique combining White Box and Black Box Testing elements. It is a powerful approach that gives testers partial knowledge of an application’s internal workings, enabling them to provide more comprehensive test coverage. The Grey Box Testing methodology is based on generating requirement test cases and utilizes matrix, orthogonal, and pattern testing techniques to debug software or applications efficiently. This approach is beneficial for complex logic and algorithms applications, as it can help uncover potential bugs that other testing techniques may miss.
Red Teaming Testing
Red Teaming Testing is an advanced web application penetration testing methodology where a group of offensive security professionals, known as the “Red Team,” simulate real-world attacks on an organization’s security posture. It aims to mimic actual adversaries’ techniques to test the organization’s capabilities and identify vulnerabilities in its digital infrastructure and physical and human elements.
It’s a comprehensive assessment that goes beyond traditional penetration testing, including social engineering, system and network exploitation, and physical security breaches. The objective is to identify and remediate vulnerabilities before they can be exploited by real attackers, thereby strengthening the organization’s overall security framework.
Difference Between Black Box vs Gray Box vs White Box Pen Testing Methods
Black Box Testing
Black box testers are professionals who aim to identify system vulnerabilities without prior knowledge of their internal workings. To achieve this, they simulate real-world attacks and approach the system as an external attacker, attempting to exploit weaknesses through various attack vectors. This approach mimics real-world scenarios and provides an outsider’s perspective, which helps identify vulnerabilities that internal teams may overlook.
Gray Box Testing
Gray box testing is a software testing technique that combines elements of both black box testing and white box testing. It involves testers having limited knowledge of the system’s internal workings, such as system architecture or limited credentials, which allows them to simulate user behavior and test the system’s functionality and security from a semi-informed perspective.
Testers combine black-box and white-box testing aspects and leverage their partial knowledge to simulate attacks more effectively. This approach allows for a more targeted and efficient testing approach, enabling testers to focus on specific areas of concern while providing an external perspective.
White Box Testing
White box testing is a method in which testers have detailed knowledge of the system’s internal workings, including its source code, architecture, and configurations. This approach allows them to thoroughly examine the system’s internals, using their knowledge to identify vulnerabilities and weaknesses. This approach provides in-depth insights into the system’s security posture, which enables precise vulnerability identification. It also facilitates targeted remediation efforts.
Each type of pen testing offers unique advantages and is chosen based on the testing scenario’s specific requirements, objectives, and constraints.
Related articles:
- What Is Software Testing and When Does Your Product Need It?
- Cracking the Code: How to Write a Bug Report That Developers Love
- QA, QC, and Testing: The Three Pillars of Software Quality Management
- Today’s World’s Most Popular Tools for Testing REST API
- Best Testing Automation Tools: Today’s Most Popular Solutions for Examining Apps
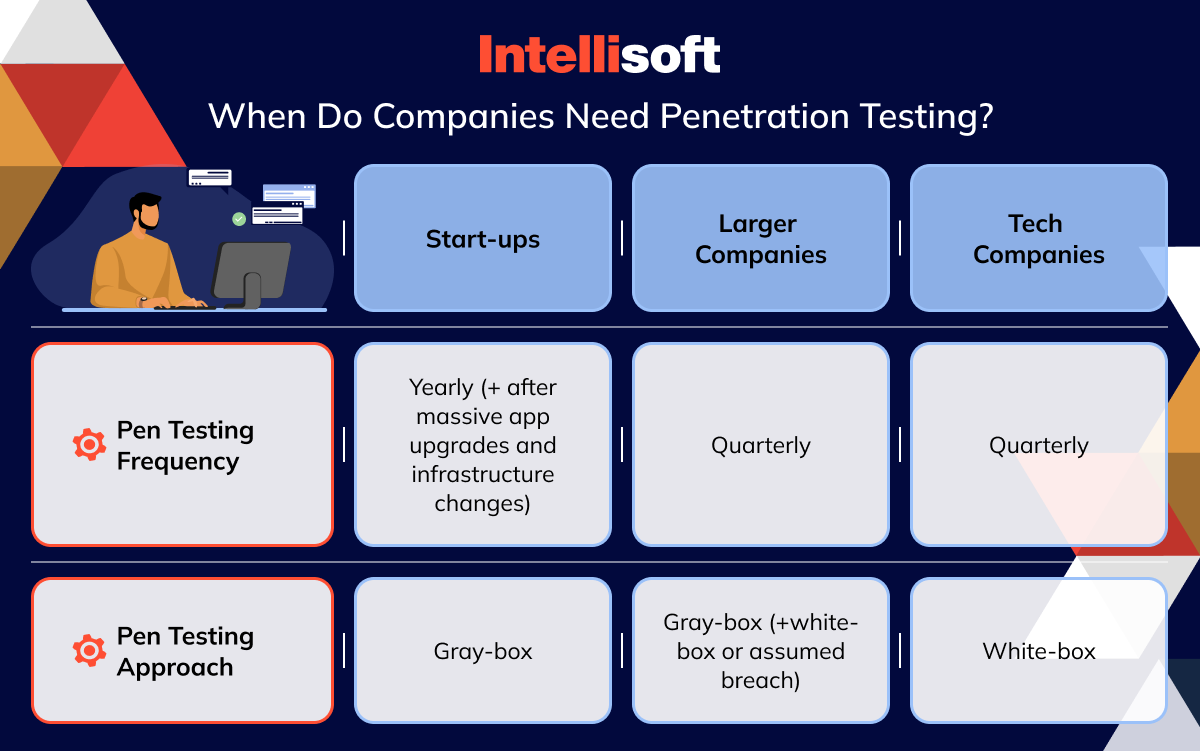
When Do You Need Penetration Testing?
For start-ups or small businesses, conducting an annual penetration test can be a great way to start identifying and addressing vulnerabilities regularly. By doing so, these companies can reduce their exposure to cyber threats and improve regulatory compliance and vendor risk assessment.
On the other hand, organizations that handle sensitive data or are at higher risk of cyber attacks, such as healthcare institutions, government agencies, R&D-heavy companies, financial institutions, and e-commerce businesses, should consider conducting more frequent in-depth penetration testing at least once every quarter. These organizations often have strict compliance needs and could face more significant risks if their data is compromised.
Quarterly pen testing is critical for large organizations with complex networks or those in the tech/SaaS industry that constantly update their systems or add new devices. These environments can be more challenging to secure, and vulnerabilities may be introduced more quickly.
Lastly, some organizations may opt for continuous or on-demand penetration testing, especially those with a high-risk tolerance or working in heavily regulated industries. While this approach may be more resource-intensive, it provides the most comprehensive protection against cyber threats.
Signs It’s Time For a New Penetration Test
If you’re having trouble figuring out whether it’s time to conduct another pen test, this brief questionnaire can help. Responding to these questions allows you to evaluate and determine whether another penetration test is necessary.
- Has your last pen test for a given scope been a year or a quarter?
- Have you recently made significant changes or updates to your infrastructure, networks, or applications (especially to critical systems)?
- Have you retested after patching vulnerabilities?
- Have you recently added multiple new functionalities to your SaaS platforms?
- Are you preparing to obtain an ISMS certification, such as SOC 2 or ISO 27001?
- Are you in the process of due diligence for M&A deals or planning to go public in an IPO?
What Is The Difference Between Automated vs. Manual Pentesting?
There are two primary approaches to conducting a penetration test on a web application: manual testing and automated testing. It is essential to carefully evaluate the strengths and weaknesses of each approach before deciding which one to use.
Automated testing is a technique that involves using specialized software tools to scan a system for vulnerabilities and simulate attacks. This approach is highly efficient and fast, as it can cover a large number of vulnerabilities in a short amount of time. However, automated web application penetration testing can also produce false positives, which means that the software may report vulnerabilities that do not exist. Moreover, automated tools may miss some vulnerabilities, especially those that require a more human touch to discover.
Manual system testing is a process where a highly skilled security professional manually tests a system for vulnerabilities and exploits them. This approach demands more time and effort but can be more thorough and accurate than automated testing. Manual web application penetration testing has the potential to unveil vulnerabilities that automated tools might overlook, as it gives the tester the freedom to think creatively and adapt to unexpected situations.
While both manual and automated testing approaches have their own advantages and disadvantages, combining them can produce the best results. Integrating automated and manual testing can help companies benefit from the strengths of each approach and create a more comprehensive test. Ultimately, the choice of which strategy to use will depend on the specific needs and resources of the company.
5 Best Web Application Penetration Testing Tools
Web app security has become a crucial concern for companies worldwide. Due to the increasing number of cyber threats businesses face, the protection and reliability of web apps are crucial. The key to achieving robust web application security is comprehensive testing and assessment. A range of essential tools are available for security professionals to make the security process smoother. These tools can detect vulnerabilities and potential security issues that may compromise web app integrity.
How To Choose Web Application Penetration Testing Tools
Choosing the right web application penetration testing tool can be daunting, given the plethora of options available in the market. Selecting a tool that best suits your needs is essential to ensure your web application is robust and secure. To help you make an informed decision, we’ve compiled some valuable tips that you can follow to narrow down your options.
Identify the problem you want to solve
When picking a tool, assess the feature gap you need to fill. Once you do this, understand the specific features and functionalities the tool must possess to meet your needs. This approach will assist you in choosing the most suitable tool that meets your requirements.
Consider who will use it
When considering the cost and requirements of software, consider the intended users and the number of licenses required. You should determine whether only the software testers will require access or must be accessible to the entire organization. You can evaluate these factors to choose the most suitable software solution.
Clarify what other tools it needs to work with
Assess the current tools, determine which to keep, and integrate new ones. This approach may include other testing tools, automation tools, or bug-tracking software. It is essential to determine if the new tool will need to integrate with the existing ones or if it can replace multiple tools with a single consolidated solution.
Consider the important outcomes
When deciding which software to use, it’s essential to clearly understand what you want to achieve and what success looks like to you. Before you select any software, take a step back and assess the specific capabilities you require and the areas in which you hope to improve. Once you’ve done that, it’s essential to determine how you will measure success.
This approach may involve tracking the number of users, monitoring the amount of time saved, or using any other relevant metric that aligns with your goals and objectives. By taking these steps, you can rest assured that you are selecting the right software to help you achieve your desired outcomes.
Evaluate how it will work within your company
When selecting software for your business, you should examine closely how the software aligns with your workflows and delivery methodology. Evaluate the aspects of your current system that are functioning well and identify any problem areas that need to be addressed. You can ensure that the software you choose will support your business processes and contribute to your overall success by conducting a thorough evaluation.
New Relic

New Relic is an advanced penetration testing web application that helps you track your application’s real-time performance. It enables you to identify performance issues, locate bottlenecks, and fix them before they become problematic.
This platform provides real-time monitoring, allowing you to monitor your app’s performance as it happens so you can quickly identify and resolve any issues. Moreover, it offers detailed analytics, enabling you to drill down into your app’s performance data to better understand what is happening. The data is presented in an easy-to-understand way.
Some key features of New Relic include backend, Kubernetes, mobile, model performance, infrastructure, log, error, network, vulnerability, and browser monitoring. The platform provides an impressive range of services with over 500 integrations, catering to various popular applications such as AWS, Google Cloud, and Microsoft Azure. It also supports multiple CI/CD tools like Jenkins, CircleCI, and Travis CI, as well as essential communication tools such as Slack and PagerDuty.
Moreover, the platform offers other tools for monitoring and analytics, such as Grafana, Datadog, and Splunk. Along with all these integrations, the platform also provides an API, which can be used to create custom integrations to meet your unique needs.
New Relic pricing starts from $49 per user per month, and a free plan is available that offers 100 GB/month of data ingest and supports one user.
Intruder
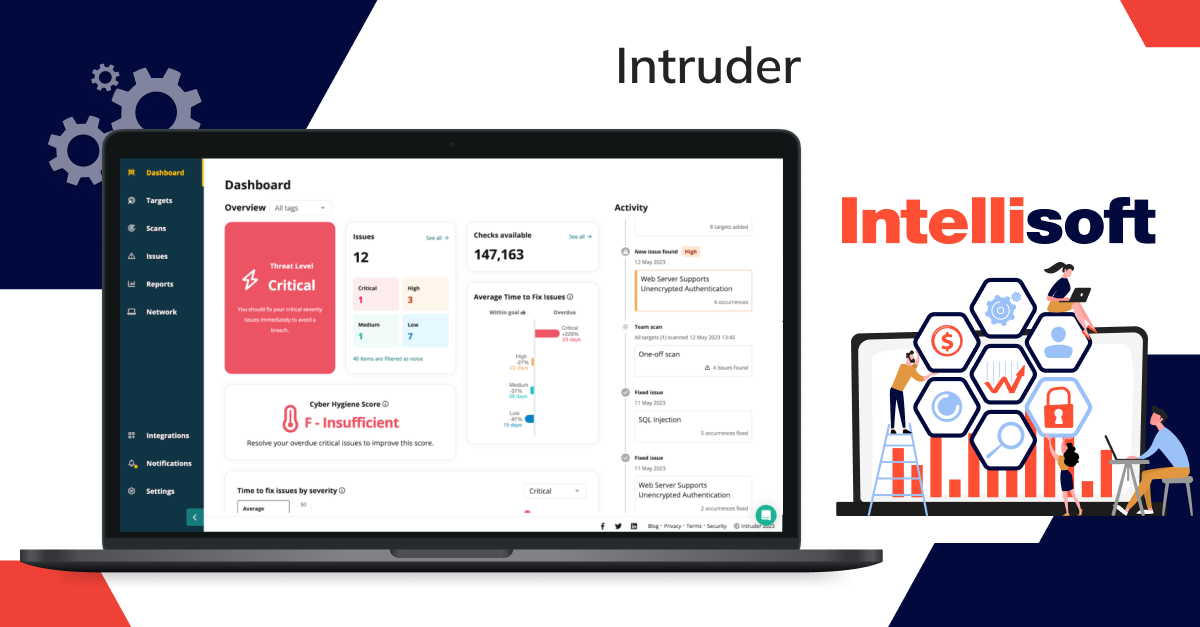
Intruder is a robust tool for vulnerability assessment and penetration testing of web application. Its features include continuous network monitoring, automated vulnerability scanning, and proactive threat response, all of which contribute to creating a more secure IT environment, reducing the attack surface, and minimizing the risk of cyberattacks.
One of the most outstanding features of Intruder is its automation capabilities. It utilizes underlying vulnerability scanners to take a proactive approach to vulnerability management, allowing for regular and systematic vulnerability assessments of digital assets with minimal manual effort. Additionally, its continuous monitoring and real-time threat monitoring capabilities ensure that security statuses are always up to date, adapting to new threats and environmental changes.
Intruder seamlessly integrates with popular business tools such as Slack, Microsoft Teams, Jira, Github, and Gitlab and can also be accessed through Zapier and API.
Pricing for Intruder starts at $196 per month per application, with a 14-day free trial available for new users.
AppTrana
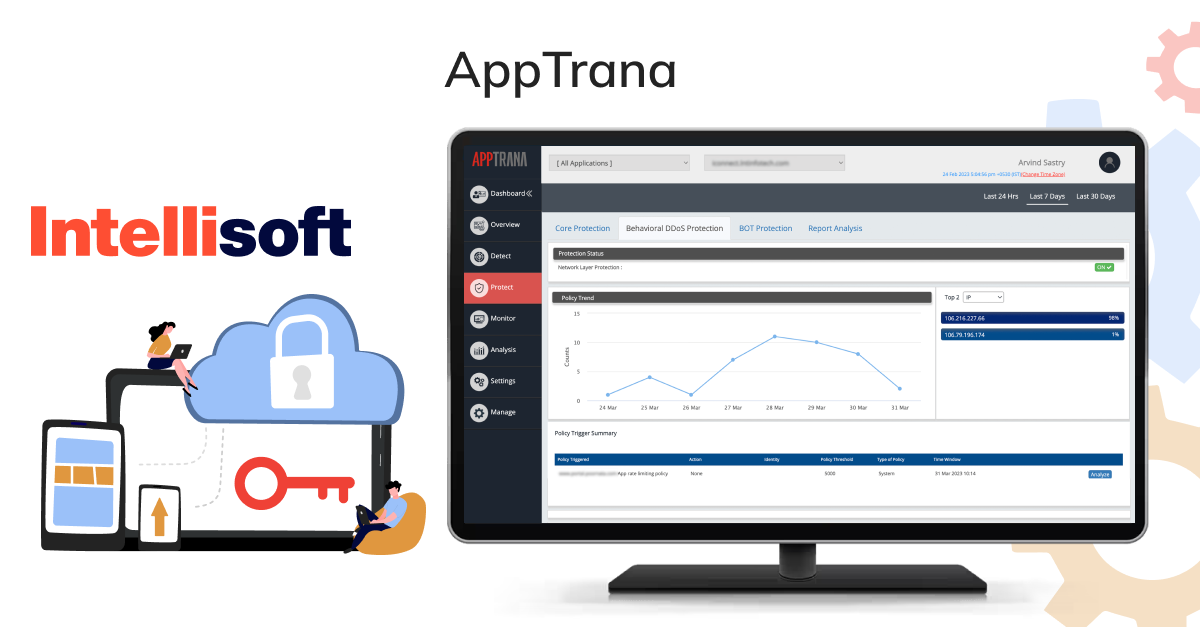
AppTrana is a web app firewall (WAF) that provides complete security solutions. It is designed to help companies protect their web applications against various cyber threats, such as penetration testing, DDoS attacks, bot attacks, and other vulnerabilities. Many security-conscious companies across different industries, such as Axis Bank, Jet Aviation, Niva Health Insurance, and TRL Transport, use AppTrana to secure their web applications.
AppTrana is a fully managed security solution, meaning its expert team analyzes and updates security policies for you. Higher-level accounts get a named account manager to assist them, while the highest subscription level comes with quarterly web application penetration testing service reviews, which are highly recommended.
Some key features of AppTrana include unlimited application security scanning, manual pen-testing of applications, managed CDN, false positive monitoring, custom SSL certificates, and risk-based API Protection. The website also explains each feature and includes a blog, learning center, whitepapers, infographics, and datasheets. So, you should visit the official website to learn more.
AppTrana costs $99 monthly per app and comes with a free 14-day trial.
Gobuster
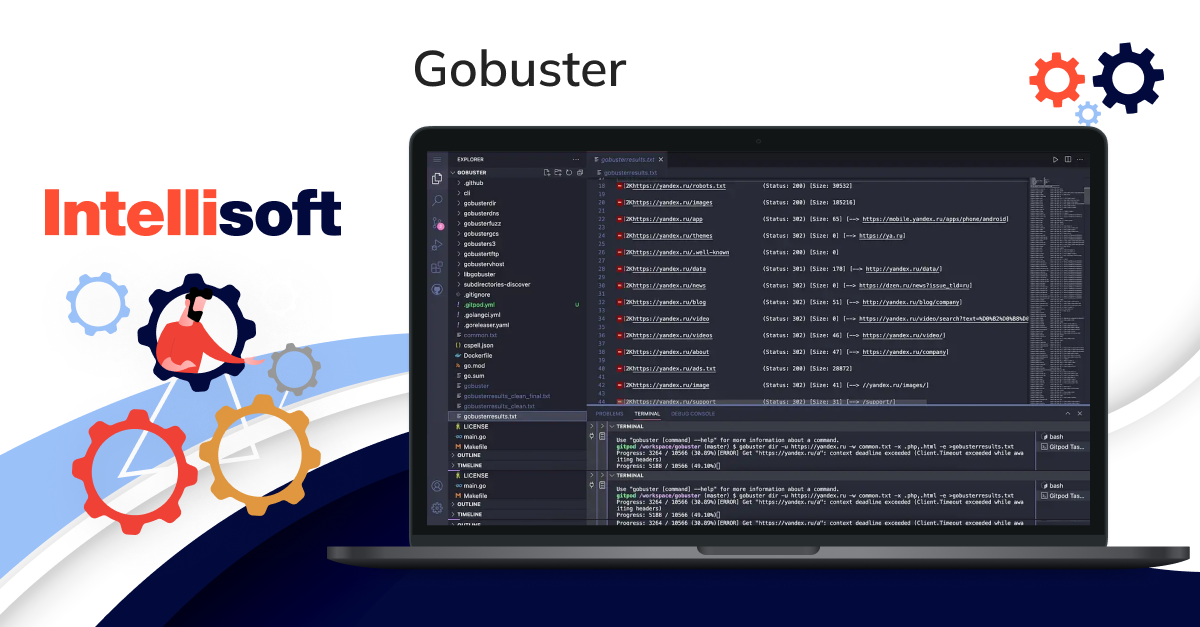
Gobuster is a web & mobile application penetration testing tool available on GitHub. It lets you scan your web application and brute force your URIs, DNS subdomains, and Virtual Host names on target web servers. This approach helps you identify unprotected scripts and old configuration files that could pose a security risk.
You can easily install Gobuster using your terminal. The tool allows you to conduct recon tests, which is an effective way to delve into the depths of your web application and detect vulnerabilities. Once the test is completed, the tool generates a detailed report, which you can use to review your code effectively.
Gobuster is an entirely open-source tool and is free to use.
Amass
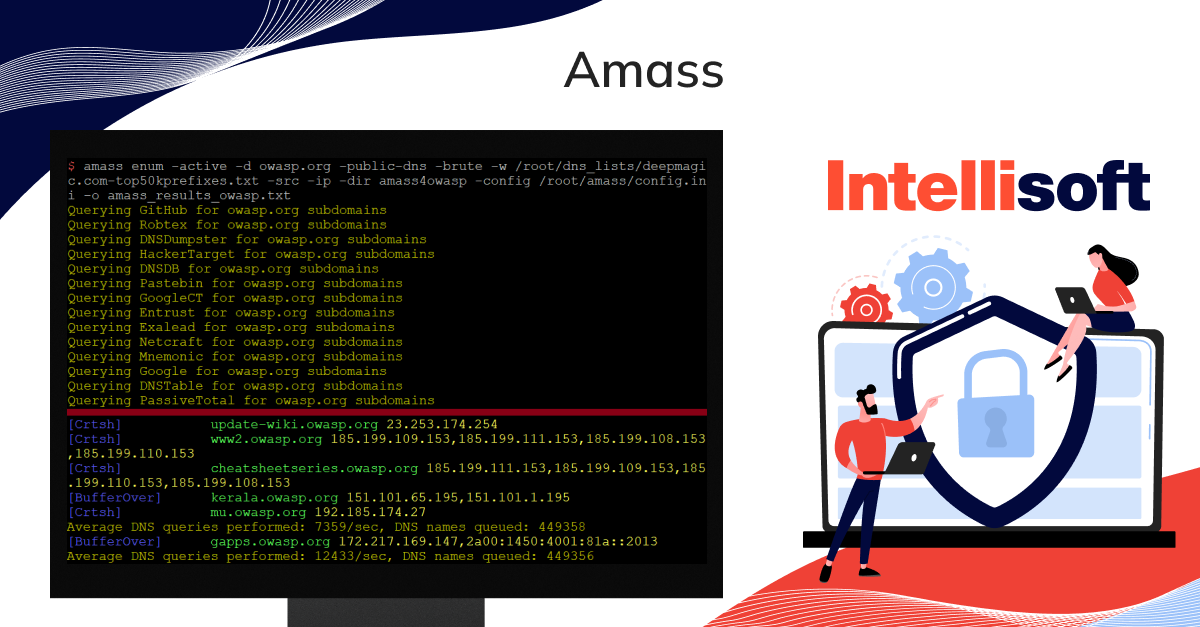
Amass is a useful penetration testing tool that enables you to conduct network mapping of cyber-attack surfaces, known as Attack Surface Management (ASM). This feature continuously monitors your changing attack surface, which helps you ensure your application is protected against cyberattacks. Additionally, the tool offers reporting of the results of these penetration tests.
Amass comes with various features, including external asset discovery, which allows you to identify active and inactive assets unknown to your organization. This feature enables you to monitor the security of your application 24/7 and improve your team’s vulnerability management.
Moreover, Amass is fully open source and free to use.
Checklist for Web App Penetration Testing
Preparation and Reconnaissance
To gather information about a web application’s architecture, it is crucial to identify its web server, the technologies it utilizes, and the databases involved. This approach can help identify potential entry points and vulnerabilities. By identifying the various components of the web application’s technology stack, testers can better understand how data flows through the system and how it is stored.
Authentication and Session Management Testing
Perform a thorough evaluation of all usernames and passwords used in your web application to ensure they meet the necessary level of complexity and security. You should also verify the strength and effectiveness of the authentication mechanisms employed in your application to prevent unauthorized access and safeguard sensitive data.
Input Validation
It is critical to ensure the security of web applications from various types of attacks such as SQL injection, Cross-site Scripting (XSS), and other injection flaws. One of the most effective ways to prevent unauthorized data processing is to validate all inputs from users and the environment. Doing so can help identify potential vulnerabilities and prevent the exploitation of such flaws. Therefore, the testing team should implement robust measures to detect and mitigate these types of attacks to maintain the security and integrity of web applications.
Functionality Testing
Ensure that providing and removing access to resources is verified thoroughly. You should also ensure proper authorization checks and access controls to ensure the system’s security.
Data Protection and Privacy
Encrypting sensitive data both during transmission and storage provides an extra layer of security to prevent unauthorized access. Moreover, carefully review how the application handles sensitive data and ensure that privacy settings are set appropriately to protect the confidentiality of the data.
Error Handling and Logging
Evaluate how the application handles errors and ensure no sensitive information is disclosed through error messages. You should also examine the logging mechanisms to determine whether they can securely capture and store essential events.
Server and Technology Configuration
Review the security setups of web servers, application servers, and databases for outdated software or missing security patches. This step is critical to protecting sensitive data and preventing security breaches. Therefore, routine checks to keep your systems up-to-date and secure are highly recommended.
Business Logic Testing
Thoroughly examine and assess an app’s business logic to identify potential vulnerabilities or exploitable weaknesses. Doing so can address and mitigate any areas of concern to ensure the safety and security of the application’s users and data.
Client-side Testing
Review the client-side codes of your web application, such as JavaScript and HTML5, to identify potential vulnerabilities that attackers could exploit. By comprehensively examining your codebase, you can ensure your web app is secure and protected against potential threats.
Report Generation
The task at hand is to gather all the relevant information, including findings, evidence, and recommendations, to address the vulnerabilities that have been identified. Testers will follow a checklist to guide them through thoroughly testing all the critical objectives and ensuring they consistently achieve the best possible outcomes.
Upgrade Your Cybersecurity With Penetration Testing Services
Penetration testing is an essential process that enables organizations to view their systems from the perspective of a potential attacker without causing harm. Organizations can prevent cyberattacks by performing pen tests as part of their cybersecurity strategy. However, navigating the vast array of options for penetration testing and determining the appropriate time for each can be complex and challenging. This is where the expertise of the cybersecurity professionals becomes invaluable, as they can tailor solutions to meet your company’s unique requirements.
IntelliSoft’s Penetration Team is renowned for its expertise and unrivaled track record of uncovering security gaps in even the most fortified systems. Through rigorous testing and evaluation, we consistently reveal that no organization is entirely impervious to potential breaches. Our approach goes beyond speculation about your system’s vulnerabilities; we provide concrete evidence of possible risks and threats. Our team is committed to being your partner in strengthening your cybersecurity measures.
To better understand your organization’s risks and explore strategies for mitigating them, we invite you to inquire further about IntelliSoft’s web application penetration testing services. Contact us to learn how we can help you protect your digital solutions from cyber threats.