Sleepless nights spent worrying about API security breaches are more common than you might think. The anxiety over data leaks and unauthorized access isn’t just your burden – it’s a widespread concern in the tech community. APIs have become the essential framework of countless applications, powering everything from mobile apps to enterprise systems.
But with their growing importance comes an increased risk of security vulnerabilities that can have serious consequences.
Consider the impact of a data breach; lost revenue, a damaged reputation, and legal troubles that could set your business back years. These are not just abstract threats—they’re real possibilities if your API security isn’t airtight.
But there’s no need to face this challenge alone. With the API security best practices 2024, you can protect your APIs and keep your sensitive data secure.
For over 15 years, IntelliSoft has been a leader in REST API security best practices predictions. Our team doesn’t just follow trends; we understand the evolving threat landscape and craft solutions that are specifically designed to meet your needs.
Table of Contents
What Is an API Security
API security protects Application Programming Interfaces (APIs) from malicious attacks, unauthorized access, and misuse. API gateway security best practices enable different software systems to communicate and share data, making them a key component of modern digital infrastructure. However, their open nature also makes them vulnerable to various threats, including data breaches, injection attacks, and abuse of API endpoints.
REST API security best practices involve several layers of protection. These include authentication and authorization mechanisms, rate limiting, input validation, and continuous monitoring for suspicious activity.
The importance of API security has become even more critical as the number of attacks continues to rise. According to the State of API Security Report Q1 2023, unique attackers have increased by 400% in six months. Despite this alarming trend, 30% of organizations still lack a formal API security strategy, exposing them to potential threats.
Given the growing reliance on APIs and the increasing sophistication of cyberattacks, ensuring robust API best practices security is no longer optional – it’s a necessity.
Why is API Security Important?
API security is vital for safeguarding your digital assets, ensuring that your data remains protected and trustworthy. As Prabath Siriwardena aptly stated, “Confidentiality, integrity, and availability (CIA), with a touch of non-repudiation, form the cornerstone of API security.” This quote encapsulates what API security best practices aim to achieve – keeping your information safe, reliable, and always accessible to those who need it.
But the numbers tell an even more compelling story. According to the State of API Security Report Q1 2023, 94% of companies encountered security issues with their production APIs in the past year. This isn’t just a minor hiccup – it’s a widespread challenge that highlights the vulnerabilities many organizations face.
And it’s not just a concern for IT departments. A global survey conducted by Global Surveyz for Salt Security found that 78% of CISOs now see API security as a higher priority than it was two years ago. Looking ahead, 95% believe it will remain a top concern in the coming years. These statistics aren’t just numbers; they reflect a growing awareness that robust API key security best practices are essential for the stability and success of any organization.
Related Readings:
- SaaS Security Tips and Checklists: Best Practices To Protect Your SaaS Application
- IoT Device Security Concepts: IntelliSoft’s Roadmap to Robust IoT Protection
- What Threatens Your Web Application Security
- What Are the Security Risks of Cloud Computing? Threats & Solutions
- Web Application Penetration Testing: How It Ensures Security
The Different Types of API Security: From REST APIs to SOAP and GraphQL
REST API Security
API gateway security best practices offer a streamlined and scalable approach to building web services, but their widespread use comes with its own set of security challenges.
HTTPS Encryption
One of the foundational elements of REST API security is encrypting data in transit using HTTPS. This ensures that all communication between clients and servers is encrypted, protecting sensitive information from eavesdropping and man-in-the-middle attacks.
Rate Limiting
Rate limiting is essential to prevent abuse and ensure fair usage. This technique controls the number of requests a user can make to the API in a given period, mitigating risks such as denial-of-service (DoS) attacks and reducing the load on your server.
Input Validation
Proper input validation is critical to protect against injection attacks and data corruption. Ensure that all user inputs are thoroughly checked and sanitized before processing to prevent malicious data from compromising your system.
Regular Security Updates
Keeping security protocols up-to-date is crucial for defending against emerging threats. To address new vulnerabilities, regularly review and update your API management security best practices, including libraries and dependencies.
SOAP Security
SOAP APIs are celebrated for their robustness and adherence to strict standards, but they also necessitate additional security measures to protect against potential vulnerabilities fully. Beyond the built-in WS-Security features, implementing access controls, secure tokens, and encryption ensures comprehensive protection.
WS-Security
SOAP APIs benefit from built-in security features provided by WS-Security. This standard facilitates end-to-end message security by implementing encryption and digital signatures, which protect the integrity and confidentiality of the messages being exchanged.
Access Controls
Enforcing strict access controls is essential to prevent unauthorized access. This includes defining and implementing user roles and permissions to ensure that only authenticated and authorized users can access specific API functionalities.
Secure Tokens
Utilize secure tokens, such as those generated through token-based authentication mechanisms, to authenticate API requests.
Message Encryption
Encrypting both the SOAP messages and communication channels helps to secure data against interception and unauthorized access. This includes using SSL/TLS for transport encryption and employing XML encryption for message payloads.
Error Handling and Logging
Proper error handling and logging practices enable you to detect and respond to security incidents effectively. Maintained detailed logs of API interactions and implemented robust error-handling mechanisms to identify and address potential security breaches promptly.
GraphQL Security
GraphQL APIs provide unmatched flexibility in data querying, but this flexibility can introduce specific security risks. Effective query complexity management, alongside robust authentication and authorization mechanisms, is crucial to protecting against potential overexposure and attacks.
Query Depth Limiting
To mitigate the risk of denial-of-service (DoS) attacks, implement query depth limiting. This approach restricts the maximum depth of nested queries, preventing clients from executing excessively complex queries that could overwhelm your server.
Complexity Analysis
In addition to depth limiting, perform complexity analysis on incoming queries to evaluate their resource consumption. Don’t forget to adhere to Restful API security best practices when doing this. By assessing the computational cost of queries, you can set thresholds and reject overly complex queries that could degrade performance.
Authentication and Authorization
Implement strong authentication and authorization mechanisms to control access to your GraphQL API. Ensure that users are authenticated before they can make requests, and enforce fine-grained access controls to manage which users can access or modify specific data.
Regular Audits
Conduct regular audits of your GraphQL API to review its security posture. This includes analyzing query patterns, monitoring for unusual activity, and evaluating access controls to maintain the integrity and security of your data.
Monitoring and Logging
Implement robust monitoring and logging to detect abnormal query patterns and potential security threats. Continuous monitoring helps in early identification of malicious activities and allows for a swift response to mitigate risks.
API Security Threats: OWASP API Top 10 and More
As APIs weave their way into nearly every corner of modern technology, knowing how to safeguard them from vulnerabilities is essential. Let’s dive into some of these critical threats and API security best practices OWASP, illustrating them with real-world examples to highlight their impact and urgency.
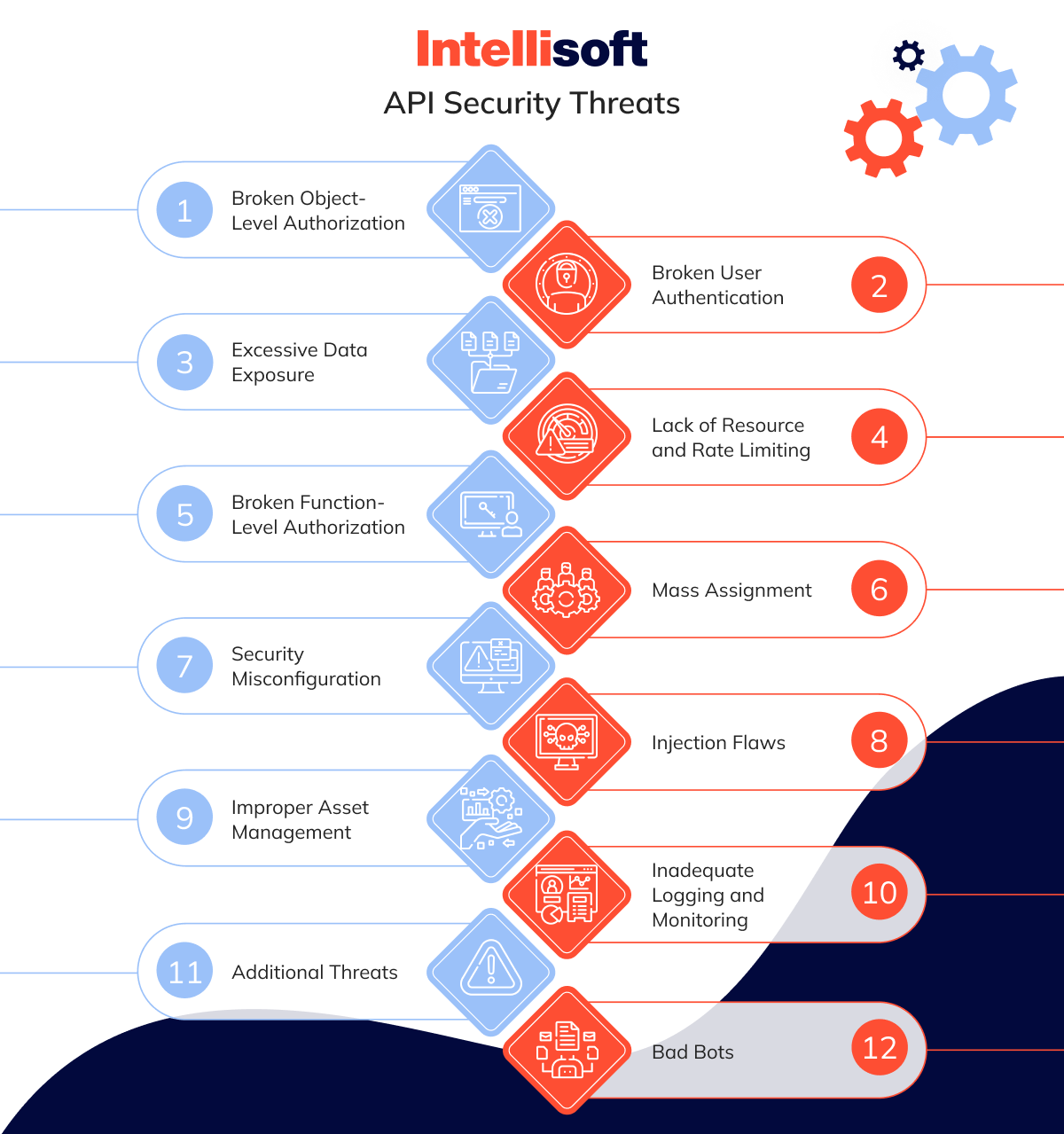
Broken Object-Level Authorization
What It Is: Imagine walking into a party and finding yourself in the VIP section without the proper credentials. Broken Object-Level Authorization is similar – when an API doesn’t check if you’re allowed to access a specific piece of data, you could end up snooping where you shouldn’t be.
Example: Picture a movie streaming service where users can view their watchlist but not those of others. If the API isn’t set up to enforce these boundaries, a curious user could manipulate requests to peek at someone else’s favorite films or even private viewing history. This happened in a recent security breach where attackers exploited a flaw to access confidential user data.
Prevention: To keep your API’s “party” secure, ensure it checks credentials meticulously before granting access to any data. Implement robust object-level access controls and Web API security best practices C# and regularly test these controls to confirm they’re in place and working as intended.
Broken User Authentication
What It Is: Broken User Authentication is like using a flimsy lock on a safe – if it’s not strong enough, unauthorized people can break in. When APIs don’t authenticate users correctly, they risk allowing unauthorized access to sensitive data.
Example: Think of a banking app where users log in with just a username and password. If these credentials are weak or if there’s no additional security layer, an attacker could easily guess or steal login details, gaining access to personal financial information. A notorious case involved a financial institution where weak authentication allowed hackers to access thousands of accounts, leading to a major financial and reputational fallout.
Prevention: Fortify your API’s authentication “lock” by using strong, multi-layered security measures and AWS API gateway security best practices. Implement multi-factor authentication (MFA), secure password storage practices, and conduct regular security audits to stay ahead of potential threats.
Excessive Data Exposure
What It Is: Excessive Data Exposure is like leaving sensitive documents on a park bench for anyone to see. When APIs reveal more data than necessary, they risk leaking sensitive information that could be exploited.
Example: Imagine an API for a healthcare app that not only returns a patient’s basic info but also detailed medical history and test results. If this data is exposed, it’s like handing out confidential health records to strangers. There have been instances where APIs unintentionally leaked sensitive customer data due to overly broad response configurations, causing serious privacy concerns.
Prevention: Keep your data “under wraps” by carefully controlling what information your API returns. Adhere to best practices for API security and limit responses to only what’s needed and use data masking techniques to protect sensitive details from unnecessary exposure.
Lack of Resource and Rate Limiting
What It Is: Lack of Resource and Rate Limiting is akin to leaving the floodgates open – without restrictions, your API could be overwhelmed by excessive traffic or misuse.
Example: Consider an online retailer’s API that doesn’t limit how often users can request product information. An attacker could flood the API with thousands of requests, causing the system to crash and disrupting service for everyone. In 2018, a major retailer faced significant outages due to such abuse, underscoring the importance of implementing proper rate limits.
Prevention: Close the “floodgates” by setting rate limits on API requests and monitoring traffic patterns. Implement thresholds to prevent any one user or IP address from overwhelming your system, ensuring smooth and reliable service for all.
Broken Function-Level Authorization
What It Is: Broken Function-Level Authorization is like letting a guest into a restricted area of a concert venue simply because they have a general admission ticket. If your API doesn’t verify that a user has permission to access specific functions, they might gain access to features or actions they shouldn’t.
Example: Imagine a project management tool where users can view their own tasks but not those assigned to others. If the API doesn’t check whether a user has permission to view or modify another user’s tasks, someone could exploit this flaw to see confidential project details or alter someone else’s work. A similar incident occurred recently when a vulnerability allowed unauthorized users to access and modify admin-level functionalities.
Prevention: Ensure that every function within your API checks for proper authorization before executing. Implement role-based access controls and NIST API security best practices and thoroughly test these permissions to ensure users can only perform actions within their designated scope.
Mass Assignment
What It Is: Mass Assignment is like a guest at a party being able to RSVP for other people or even change the event details. When APIs allow users to modify multiple attributes in a single request without validating what they’re allowed to change, it can lead to unauthorized modifications.
Example: Consider an API for an e-commerce site where users can update their profile information. If the API doesn’t restrict which fields users can modify, an attacker might exploit this to change their user roles or access levels, potentially gaining unauthorized access to admin features. A notable breach occurred when attackers used mass assignment to escalate their privileges and compromise sensitive systems.
Prevention: Guard against this by validating and restricting which attributes can be modified through your API keys security best practices. Use explicit whitelists for attributes that users are allowed to update and reject any unexpected changes to prevent unauthorized modifications.
Security Misconfiguration
What It Is: Security Misconfiguration is like leaving the door to your house unlocked and the windows wide open. It occurs when API settings or components are improperly configured, leaving your system vulnerable to attacks.
Example: Imagine a cloud-based API that has default credentials or overly permissive settings. If these configurations aren’t hardened, an attacker could exploit them to gain access to your system. For instance, a well-known security incident involved an API left exposed with default settings, leading to a massive data breach and significant financial loss.
Prevention: Secure your API by performing thorough security configurations and implementing cloud API security best practices. Disable default settings, apply the principle of least privilege, and regularly review and update your configurations to ensure they adhere to best security practices.
Injection Flaws
What It Is: Injection Flaws are like a sneaky hacker slipping malicious code into a seemingly harmless request. When an API doesn’t properly validate or sanitize user input, it’s susceptible to various injection attacks, including SQL injection, which can compromise the entire system.
Example: Consider a travel booking API where user inputs are directly included in database queries without proper validation. An attacker could inject malicious SQL code to manipulate or access the database in unintended ways, such as retrieving confidential customer information or altering booking details. A high-profile example involved attackers using SQL injection to breach a major retailer’s database, causing widespread damage.
Prevention: Protect against injection attacks by rigorously validating and sanitizing all user inputs and adhering to Azure API gateway security best practices. Use parameterized queries and prepared statements to ensure that inputs are treated as data rather than executable code, reducing the risk of injection vulnerabilities.
Improper Asset Management
What It Is: Improper Asset Management is like losing track of the keys to all the doors in your house. When you don’t have a clear inventory of your APIs and their components, you risk leaving some doors unlocked or unattended, making your system vulnerable to attack.
Example: Imagine a company that launched multiple APIs over the years but fails to keep track of them. Some APIs might still be running outdated versions or might have been forgotten altogether. These “shadow APIs” can become easy targets for attackers who find and exploit them. For instance, a company recently faced a breach when hackers discovered and exploited an old, unmonitored API that had never been properly secured or decommissioned.
Prevention: Keep a detailed inventory of all your APIs, including versions, endpoints, and security measures. Regularly audit and update your APIs and decommission any that are no longer in use to minimize exposure and adhere to Azure API security best practices.
Inadequate Logging and Monitoring
What It Is: Inadequate Logging and Monitoring is like having a security camera that doesn’t record or a guard who isn’t paying attention. Without proper logging and monitoring, you might not even realize that your API is under attack until it’s too late.
Example: Picture an online service that doesn’t log API requests or monitor for unusual activity. If an attacker starts probing the API for vulnerabilities, the lack of monitoring means these attempts go unnoticed, allowing the attacker to exploit weaknesses without detection. A high-profile breach occurred when a company discovered too late that attackers had been siphoning off sensitive data for months, undetected due to inadequate monitoring.
Prevention: Implement comprehensive logging and real-time monitoring for all API activity and adhere to .NET Core Web API security best practices. Set up alerts for suspicious patterns or anomalies and regularly review logs to ensure any potential threats are identified and addressed promptly.
Additional Threats
What It Is: Beyond the well-known threats, APIs face various other risks that can compromise their security. These additional threats often arise from unique system configurations, emerging technologies, or evolving attack techniques.
Example: One such threat is API chaining attacks, where an attacker exploits multiple interconnected APIs to escalate privileges or access unauthorized data. Imagine a scenario where an attacker uses one API to gather information and another to perform unauthorized actions based on that data. This type of attack was highlighted in a recent security breach where interconnected APIs were exploited to gain full access to a company’s internal systems.
Prevention: Stay vigilant by regularly updating your threat models and security practices. Educate your team on emerging threats and consider employing advanced security tools that can identify and mitigate complex attack vectors.
Bad Bots
What It Is: Bad Bots are like unwanted pests that sneak into your home, causing all sorts of trouble. These automated scripts are programmed to interact with your APIs in malicious ways, such as scraping data, performing unauthorized transactions, or overwhelming your system with traffic.
Example: Think of a ticketing service where bots are used to purchase large numbers of tickets the moment they go on sale, only to resell them at a higher price. If the API doesn’t have defenses against bots, legitimate customers might be left empty-handed, and the system could be strained by excessive traffic. In 2020, a major concert ticketing platform faced backlash when bots bought up most of the tickets for a popular event, frustrating customers and damaging the company’s reputation.
Prevention: Protect your APIs from bad bots by implementing measures such as CAPTCHA challenges, rate limiting, and bot detection services. Regularly update your bot mitigation strategies to stay ahead of increasingly sophisticated automated attacks.
API Security Best Practices
Safeguarding your APIs isn’t just a technical requirement – it’s a trust pact with your users. Whether you’re in the development phase or already running in production, these Azure API management security best practices will help you keep your APIs secure and resilient against evolving threats.
Development and Testing
Design with Security at the Core
Think of secure API development as building a house on solid ground. Start with the right foundation by embracing secure coding practices and configurations. Follow standards such as the OWASP Application Security Verification Standard (ASVS) to guide your decisions, ensuring that your API is resilient from the inside out.
Protect What Matters
Not all data needs to be shared, and in the world of APIs, less is often more. Avoid overloading your client apps with too much information, and instead, send only what’s necessary. This not only reduces the risk of data leaks but also keeps your API running smoothly.
Make Design Reviews Count
Design reviews should be more than just a checkbox on your to-do list. Dive into the business logic – how your API functions in the real world—and identify any potential vulnerabilities early on. This proactive approach can save you from headaches down the road.
Document for Clarity
Good documentation is like a map for anyone navigating your API. It helps developers understand how to use it, and for your team, it’s essential during security testing and protection. Go a step further and use machine-readable formats like OpenAPI Specification (OAS). This not only aids in communication but also allows for automated testing, making your API stronger and more reliable.
Keep Track of Everything
Imagine trying to protect a house without knowing how many doors or windows it has. Similarly, keeping an accurate inventory of your APIs gives your security team a clear picture of what needs to be protected. Automated tools can help you keep tabs on all your APIs, whether they’re REST, GraphQL, or something else.
Test Like Your Security Depends on It (Because It Does)
Before your API meets the world, it needs to pass the ultimate test. Use AWS API security best practices and security tools to identify any weak spots, but remember, no tool is perfect. Pair automated scans with manual testing to catch those tricky issues that only a human eye can spot.
Production
Monitor Like a Hawk
Once your API is live, you need to keep a close watch. Turn on logging and monitoring to collect data that shows you how your API is behaving. This data helps you spot unusual activity—like someone trying to break in—and lets you respond quickly before any real damage is done.
Use Gateways as Guardians
API gateways do more than just manage traffic – they’re your security checkpoints. They give you visibility into what’s happening with your APIs and can be paired with additional security tools to provide deeper insights and stronger defenses.
Stay Alert for API Drift
APIs change over time, but these changes can introduce new risks. Make sure you have a plan to detect when an API behaves differently from its original design. Automated platforms can compare your documentation with real-world behavior, helping you catch any discrepancies and update your security measures accordingly.
Fortify Your Network
Think of network security controls as the locks and alarms on your digital house. Encrypt data as it moves, use dynamic rate limiting to control traffic, follow C# Web API security best practices, and maintain IP allow and deny lists where appropriate. These steps help protect your API from unauthorized access and potential attacks.
Authenticate and Authorize on Repeat
Security isn’t a one-time thing – it’s continuous. Instead of relying on static API keys, use external access controls and identity management systems that regularly authenticate and authorize users. Adhere to Microsoft Graph API security best practices, too. This ensures that only the right people have access to your API’s resources.
Shield Your API in Real-Time
Once your API is out in the wild, it needs ongoing protection. Deploy runtime protection that can detect configuration issues and unusual behaviors, like credential stuffing or brute force attacks. This keeps your API safe, even as new threats emerge.
How to Secure APIs: Implementation Strategies
Securing your APIs isn’t just about setting up a few defenses; it’s about creating a robust, multi-layered approach with the help of API authentication security best practices that adapts to evolving threats. Here’s how you can strategically implement security measures to keep your APIs safe and sound.

Start with Secure Design Principles
Before a single line of code is written, ensure that your API is built on solid security foundations. This includes adopting secure coding practices, following industry standards like OWASP ASVS, API security best practices NIST 800-53, and integrating security considerations into every phase of the development lifecycle. Think of this as laying down the blueprints for a well-fortified structure – everything else builds on this foundation.
Enforce Strong Authentication and Authorization
APIs often serve as gateways to critical data and services, so you need to control who gets through the door. Implement strong authentication methods, such as OAuth 2.0, to verify users, and enforce strict authorization checks to ensure that each user only accesses what they’re allowed to. By continuously authenticating and authorizing users, you reduce the risk of unauthorized access.
Use Encryption Everywhere
Encryption is your best defense against eavesdropping and data tampering. Make sure that all data transmitted through your API is encrypted using HTTPS, and consider encrypting sensitive data at rest as well. This adds an additional layer of security, ensuring that even if data is intercepted, it remains unreadable to unauthorized parties.
Implement Rate Limiting and Throttling
To protect your API from abuse, such as denial-of-service attacks or excessive requests that could overload your system, implement rate limiting and throttling. These measures control the number of requests a client can make in a given timeframe, preventing malicious actors from overwhelming your API and ensuring that resources remain available to legitimate users.
Monitor and Log Activity
Logging and monitoring are crucial for detecting and responding to security incidents. By keeping a close eye on your API’s activity, you can spot unusual patterns or potential threats in real time. Logs provide a trail that can be invaluable in investigating breaches, while monitoring tools can alert you to issues before they escalate.
Regularly Update and Patch APIs
Security isn’t a set-it-and-forget-it task. Keep your APIs up to date with the latest security patches and updates. Vulnerabilities can emerge over time, so regularly reviewing and updating your API’s components – such as libraries and frameworks – helps protect against newly discovered threats.
Conduct Security Testing and Audits
Regular security testing and audits are essential to identifying vulnerabilities in your APIs. Use tools like penetration testing and fuzzing to simulate attacks and uncover weak points. Security audits, both internal and external, help ensure that your API meets the latest security standards and best practices.
Employ API Gateways and Security Tools
API gateways serve as intermediaries that manage, secure, and monitor API traffic. They offer features like rate limiting, authentication, and data transformation. Combine these with specialized API security tools that provide deeper insights and protection, ensuring that your APIs are both robust and resilient.
Keep Documentation Up to Date
Clear, detailed documentation isn’t just for developers – it’s a vital part of your security strategy. Up-to-date documentation helps your team understand the API’s structure and security measures, making it easier to maintain and protect. Use machine-readable formats like OpenAPI to automate testing and ensure consistency between your documentation and your API’s actual behavior.
Educate Your Team
Finally, ensure that everyone involved in the API lifecycle – from developers to security teams – understands the importance of API security. Regular training and awareness programs help keep security top of mind, ensuring that best practices are followed and potential threats are recognized early.
By implementing these strategies, you’re not just reacting to threats – you’re building a proactive, resilient approach to API security. This way, your APIs remain robust, your data stays protected, and your users’ trust is well-placed.
If you’re looking for expert guidance or support in securing your APIs, don’t hesitate to contact IntelliSoft – our team is here to help you safeguard your digital assets with confidence.